What Is a Residential Proxy?

How Residential Proxies Work and Why They Matter for Security and Fraud Teams
Residential proxy services route traffic through real consumer devices and ISP networks, producing IP signals that appear identical to typical household users. This makes them useful for legitimate regional purposes such as ad verification and QA testing, but also provides attackers with a scalable way to hide automation, bypass geo-controls, and evade reputation-based defenses.
Because these IPs originate from trusted residential networks, proxy-driven traffic blends easily with real user behavior. For security and fraud teams, this creates a significant visibility challenge: malicious activity using residential proxies often slips past IP-based reputation filters, rate limits, and basic geolocation controls.
As residential proxy networks grow in scale and sophistication, it’s essential to understand how they operate and how they differ from VPNs, mobile proxies, and datacenter infrastructure. This guide explains how residential proxies work, why they’re so widely used, the risks they introduce, and the signals that help teams detect and mitigate them.
Understanding Residential Proxies
A residential proxy is an intermediary service that routes a user’s traffic through an IP address assigned to a real household by a consumer internet service provider (ISP). Instead of appearing to come from a datacenter or cloud network, the connection looks like it originates from a normal home router on a cable, fiber network, or other broadband network.
If you’ve ever seen traffic coming from consumer ISPs but the behavior seems automated, high-velocity, or geographically inconsistent, there’s a good chance a residential proxy may be involved.
How Residential Proxy Providers Source Their IPs
Residential proxy pools are created using several methods, including:
- Embedded SDKs: Many mobile apps or desktop applications include third-party SDKs that effectively turn users’ devices into proxy nodes. Some users knowingly opt in; others may be unaware the capability exists.
- Peer-to-peer proxy clients: Software that allows users to “share” their bandwidth in exchange for compensation, credits, or free software features.
- Compromised devices: Malware, botnets, and hijacked IoT devices can silently add infected systems into residential proxy networks.
- ISP/static residential allocations: Some providers lease or repurpose consumer-assigned IP ranges for “static residential” services.
In all cases, the result is the same: the proxied traffic travels through an IP that looks and behaves like a normal household user on the open internet.
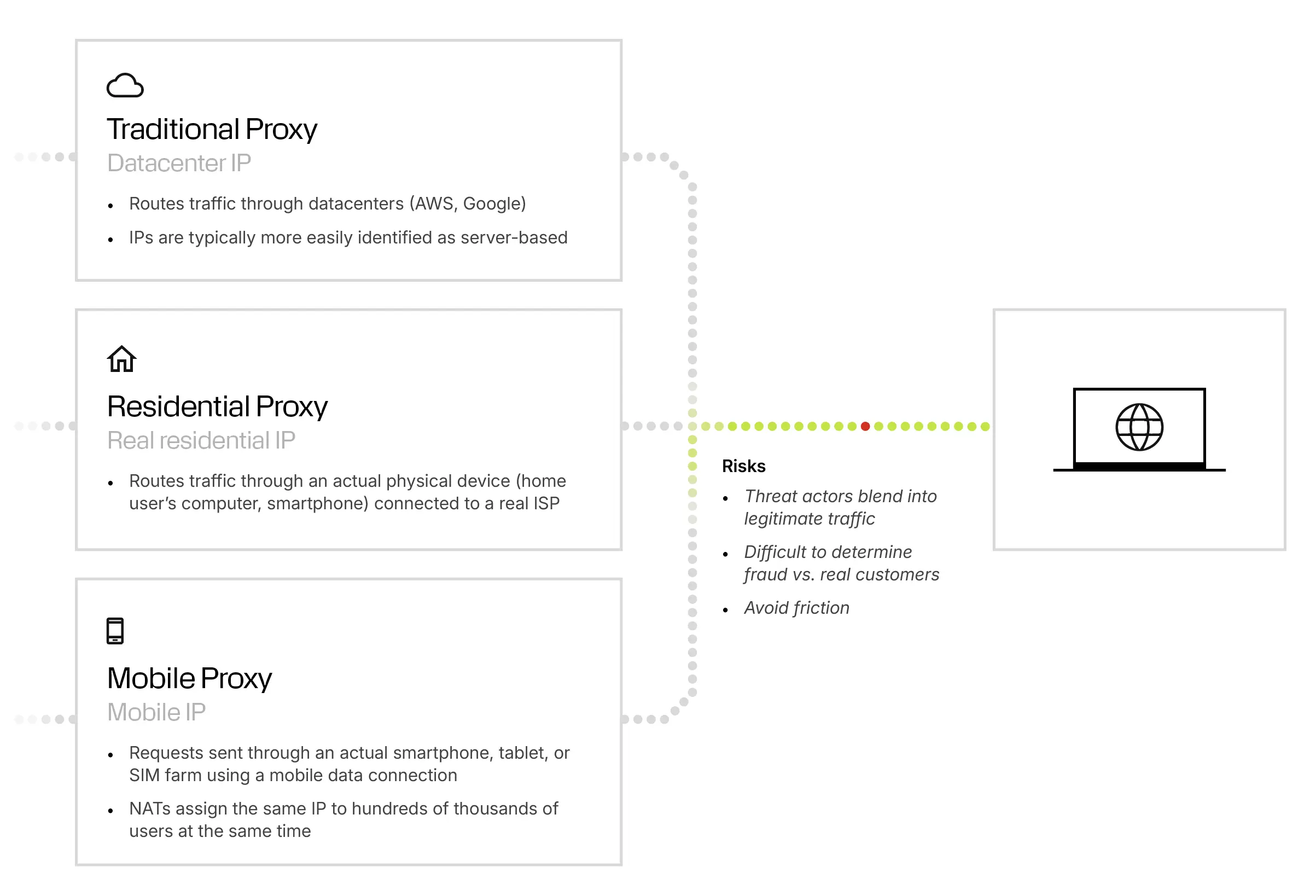
How Residential Proxies Differ from Datacenter and Mobile Proxies
Not all proxies behave the same way. Understanding the distinctions helps security teams calibrate their defenses.
Datacenter Proxies
Datacenter proxies route traffic through cloud providers or hosting environments such as AWS, GCP, DigitalOcean, or OVH.
Characteristics:
- IPs are server-hosted and easier to identify
- Commonly used for automation, scraping, and bot operations
- Often blocklisted based on known hosting ASN ranges
- Lower risk of false positives when blocking
Mobile Proxies
Mobile proxies route traffic through smartphones, tablets, SIM farms, or carrier networks. IPs sit behind carrier-grade NATs, meaning thousands of devices may share the same public IP.
Characteristics:
- Very high churn and session diversity
- Hard to link activity to an individual device
- Useful for evasion, geo-spoofing, and bot operations
- Higher risk of over-blocking legitimate mobile users
Residential Proxies
Residential proxies sit in the middle. They combine the legitimacy of consumer ISP ranges with the flexibility and scale of commercial proxy networks.
Characteristics:
- Hard to detect via basic IP reputation
- Highly effective at bypassing geo-controls and rate limits
- Blend malicious automation into legitimate user traffic
- High false-positive risk if blocked indiscriminately
Residential Proxies vs. VPNs
Residential proxies and VPNs are often lumped together because both mask the user’s true IP address, but they work very differently.
How VPNs Work
A VPN routes traffic through centralized servers owned or leased by the VPN provider. These servers are typically located in datacenters. All VPN subscribers share the provider’s exit nodes. All of the traffic from a VPN node corresponds with the VPN service.
VPN signals include:
- Dedicated IP ranges
- Predictable ASN and registration patterns
- Publicly announced VPN netblocks
- Consistent port signatures and services
Detection is generally easier because VPN endpoints are internet-facing by default and in common hosting providers.
How Residential Proxies Work
A residential proxy routes the traffic through an actual home connection — not a server. This creates a far more convincing disguise.
Residential proxy signals include:
- Consumer ISP ranges with legitimate user traffic
- IPs associated with real households and physical locations
- Organic churn and device dispersion
- Regionally consistent IP footprints
This makes them significantly harder to identify using traditional signals like IP reputation or ASN lookups.
Why Residential Proxies Are Hard to Detect
Organizations often rely on tools or controls that were designed before commercial-scale residential proxy networks were common. As a result, many legacy detection methods struggle.
Key detection challenges include:
- Consumer ISP Sources: Because the IP originates from a home or business instead of a datacenter (e.g., Comcast, Vodafone), reputation systems treat it as benign.
- Geographic Legitimacy: Traffic appears to come from the correct local region, bypassing basic geo-controls. This is frequently achievable down to a specific address.
- Large, Diverse IP Pools: Residential proxy providers manage millions of rotating IPs, making static blocklists ineffective.
- High-Frequency Rotation: Users can rotate IP address exist at will, defeating per-IP thresholds and rate limits.
- Blended Human and Automated Traffic: Because multiple app users may share the same device or network, the automated traffic is more difficult to isolate.
Modern detection requires attributing IPs to known proxy services, understanding rotation behaviors and the tradecraft of the threat-actor managing the traffic, allowing for more granularity in defense strategy.
Why Residential Proxies Are Widely Used
Residential proxies serve some legitimate purposes, though these are also frequently against a site’s terms of service:
- Localized ad verification
- Multi-region UX testing
- Competitive intelligence scraping
- Local SEO validation
- Red team and Pen test operations
However, their anonymizing properties and ease of acquisition make them attractive for malicious use.
Common Abuse Scenarios Involving Residential Proxies
- Account Takeovers (ATO) & Credential Stuffing: Attackers pair automated tools with rotating residential IPs to test credential pairs at scale. Because each attempt appears to come from a different household from a geographically consistent location, per-IP lockouts are ineffective.
- Account Farming & Fake Account Creation: Fraudsters create thousands of accounts by spreading requests across many residential IPs to avoid rate limits and reputation systems.
- Inventory & Ticket Scalping: Bots use residential proxies to bypass IP-based purchase or cart limits, appearing as thousands of individual shoppers.
- Scraping & Competitive Intelligence Abuse: Large residential proxy pools help evaders slip under rate thresholds and avoid WAF rules and steal price or inventory data.
- Coupon & Promo Abuse: Attackers generate many accounts to repeatedly redeem offers without exceeding IP-based thresholds.
- Ad Fraud: Fraudsters simulate impressions or clicks from “real users,” making attribution difficult.
- Evasion of Geo-Controls: Residential proxies enable access to unlicensed or region-locked content at scale.
- Regulatory & Compliance Blind Spots: Government platforms, citizen services, and financial systems face attribution and KYC challenges when masked access hides problematic origins.
Want the full technical analysis?
Our white paper, “Why Residential Proxies Are a Security Risk,” goes deeper into detection signals, proxy provider ecosystems, architectural diagrams, and detailed case studies.
How to Detect Residential Proxy Traffic
Identifying residential proxy usage requires deeper IP intelligence combined with broader context. The following signals are critical.
1. ASN & ISP Context
Residential proxies are supposed to look like consumer ISP traffic — but some patterns give them away over time:
- Rapid shifts across unrelated ISPs during the same session
- Residential IPs appearing in high-risk automation patterns
- Suspicious geographic clustering or skew
2. Known Proxy Service Fingerprints
Detection datasets can map traffic to known services (e.g., IPIdea, Oxylabs, SmartProxy) and identify dynamic proxy pools and ISP/static residential allocations.
3. Rotation Patterns
Short-lived sessions, inconsistent user-agent fingerprints, or rapid city/ISP hopping strongly indicate automated residential proxy use.
4. Mismatched Telemetry
Examples include:
- Browser language ≠ IP geolocation
- Impossible travel patterns
- Device claims inconsistent with ISP type
- Session fingerprints changing while the user stays “logged in”
5. Behavior + IP Correlation
Residential proxies become more obvious when paired with platform specific knowledge:
- High login failure rates
- Automated navigation patterns
- Direct API calls without page renders
- Abnormal signup or checkout flows
The strongest detection approaches combine third-party IP intelligence, user behavior, device fingerprinting, and historical patterns.
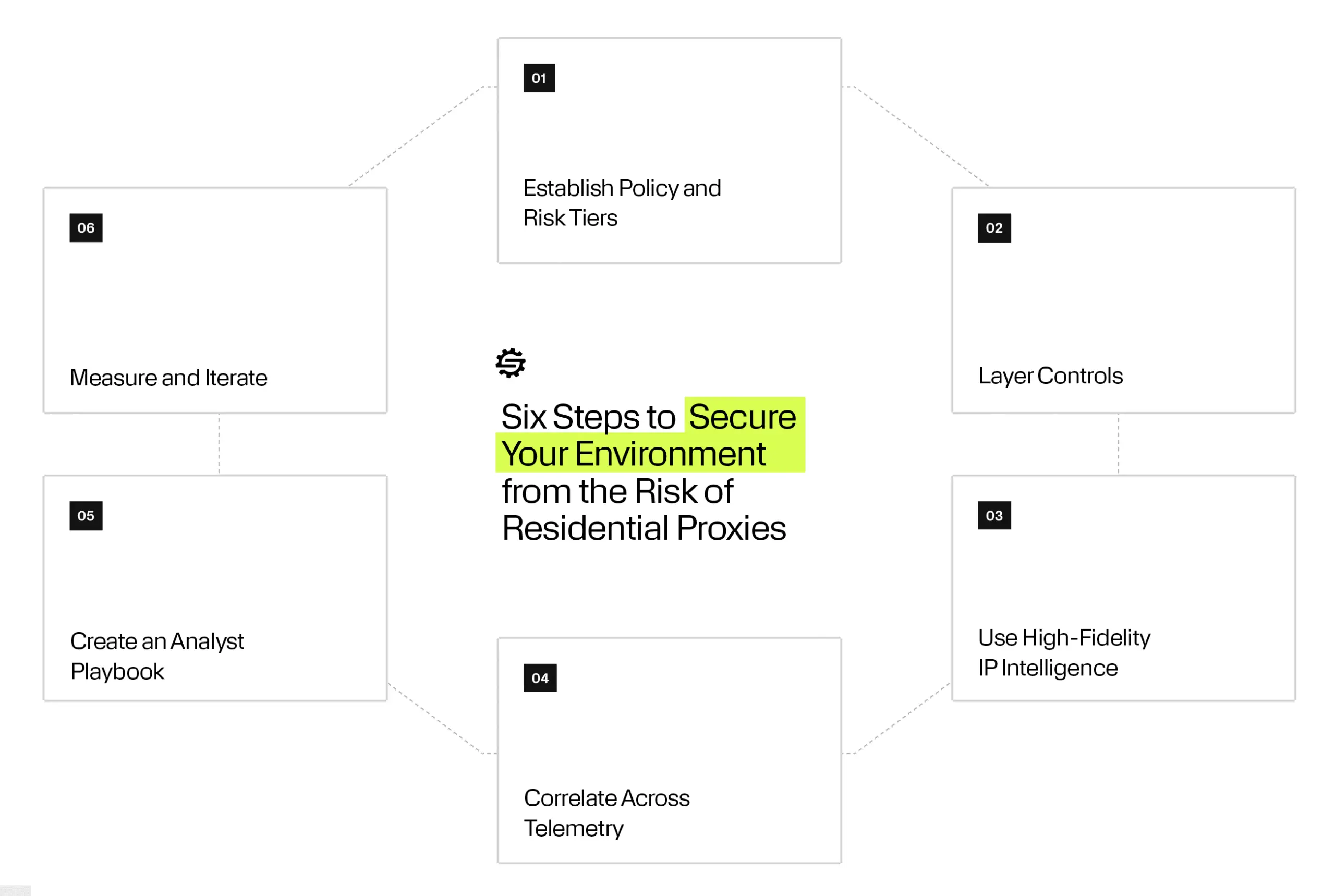
Practical Steps to Reduce Residential Proxy Risk
Organizations can dramatically improve defenses by moving beyond single-signal detection.
1. Establish Policy and Risk Tiers
Identify which workflows are sensitive (e.g., authentication, checkout, account creation) and where residential proxy use is acceptable or should trigger friction.
2. Layer Controls
Combine MFA, CAPTCHA, bot challenges, rate limits, and step-up authentication — triggered adaptively based on assigned session risk.
3. Use High-Fidelity IP Intelligence and Session Enrichment
Ingest datasets that differentiate and attribute:
- Residential vs. mobile vs. datacenter proxies
- Dynamic vs. static residential IPs
- Known proxy and VPN services
- Device and tunnel context
4. Correlate Across Telemetry
Blend IP intelligence with behavioral analytics, session data, and device fingerprints for a fuller picture.
5. Create an Analyst Playbook
Document how to respond when proxy usage is detected:
- Tighten limits
- Issue challenges or increase friction
- Block or throttle
- Escalate for investigation
- Share indicators internally
6. Measure and Iterate
Track false positives, user friction, and emerging proxy types. Update controls regularly.
How Spur Helps Bring Clarity to Obscured Internet Traffic
Advanced IP intelligence is essential for distinguishing real users from anonymized traffic.
Spur provides:
- High-fidelity residential, mobile, and datacenter proxy detection
- Detection of 230M+ active anonymized IPs every 90 days
- Identification of ~60M suspect IPs daily
- Attribution across 1,000+ active VPN and proxy services
- Real-time session intelligence for the highest accuracy
- Deep IP attributes (tunnels, device types, behaviors, risk signals)
- Historical data back to 2020
These capabilities help organizations reduce fraud, prevent account abuse, improve attribution, and protect critical systems without harming the experience of legitimate users.
To experience our high-fidelity IP intelligence in action, sign up for a free trial or request a demo today.
Download the Full Residential Proxy White Paper
Residential proxies introduce both operational benefits and meaningful security risks, and their growing adoption makes visibility increasingly critical. To explore the underlying attribution challenges, proxy fingerprints, evasion patterns, and real-world case studies in more depth, download our white paper “Why Residential Proxies Are a Security Risk.”
This report provides a comprehensive technical foundation for analysts, fraud teams, and security engineers evaluating the impact of anonymized residential traffic.
Residential Proxies: Frequently Asked Questions
See the Difference Between Raw Data & Real Intelligence
Start enriching IPs with Spur to reveal the residential proxies, VPNs, and bots hiding in plain sight.