The Spur IP Intelligence Platform.
Verified, explainable context for every connection.
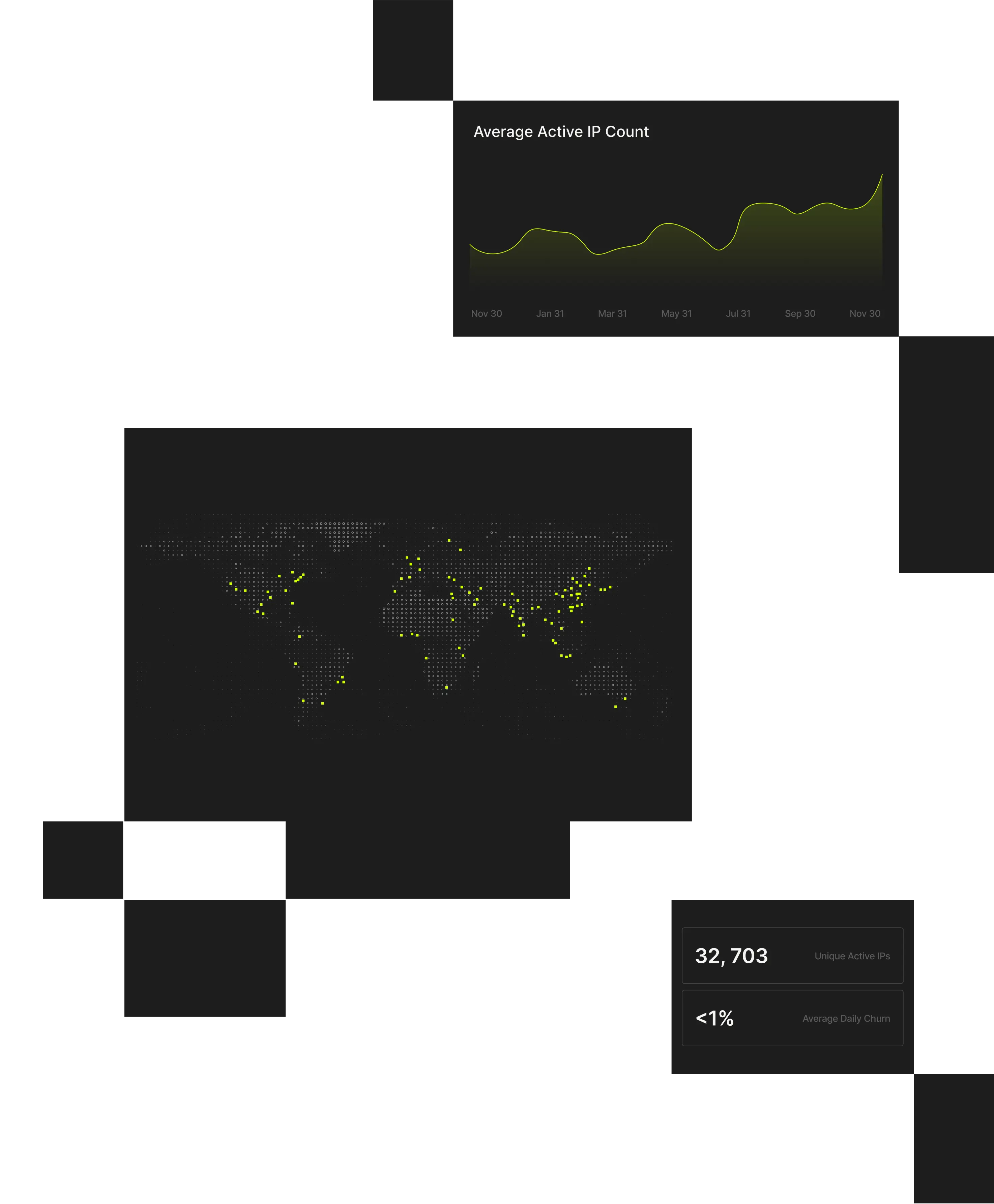
Spur turns raw IP data into verified, explainable intelligence that exposes hidden infrastructure and malicious intent, so security, threat, and fraud teams can act with speed and confidence.
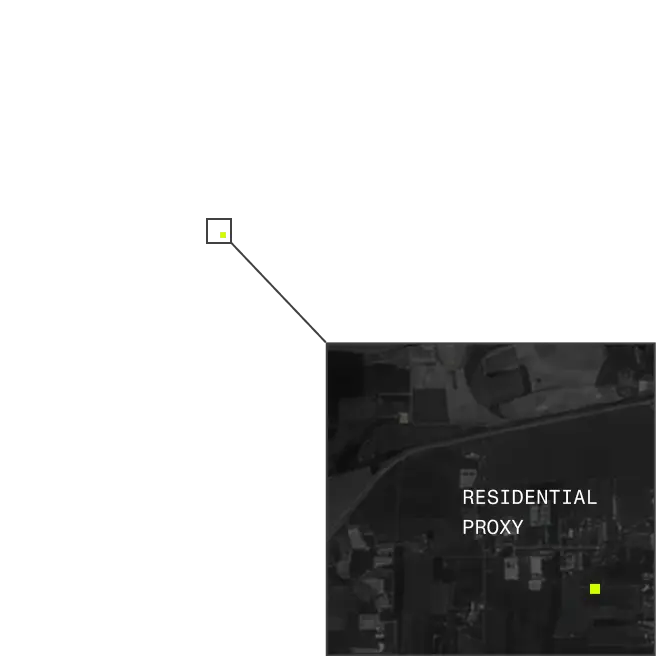
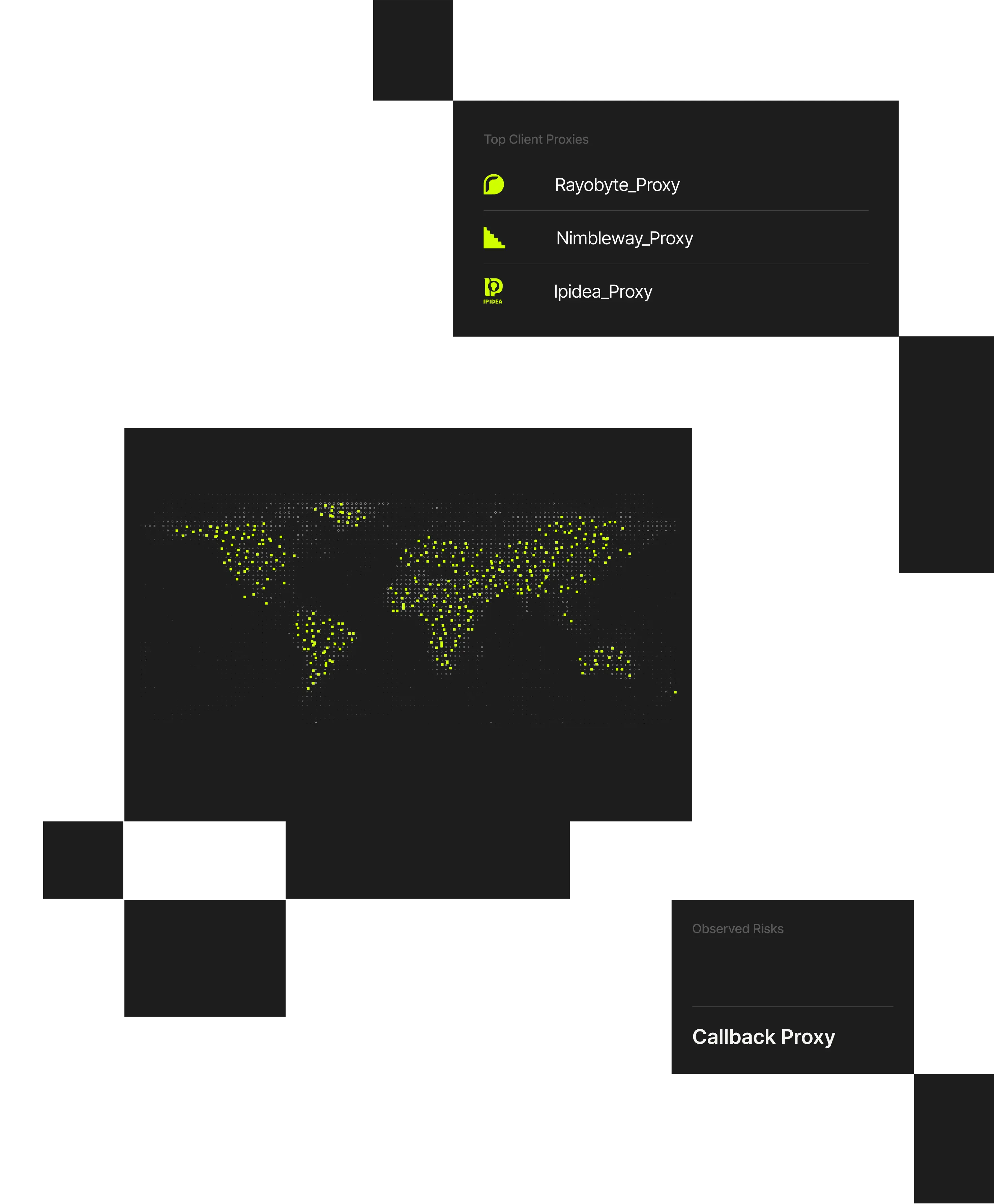
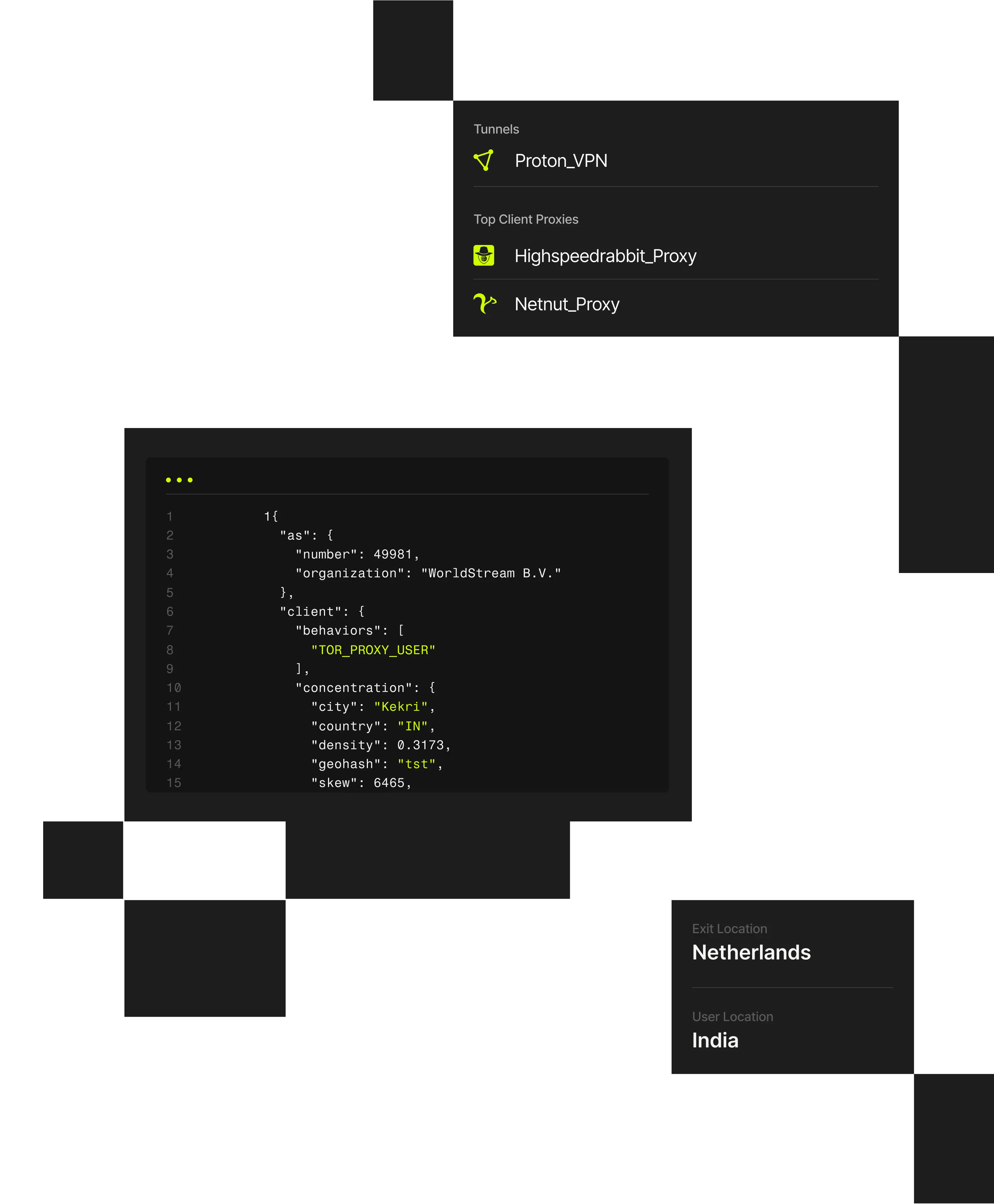
VPNs, proxies, and co-opted networks with residential proxies enable attackers to appear legitimate, making real users and threats look the same. Spur delivers a central platform for making sense of obscured IP traffic, without disrupting workflows or adding unnecessary friction.

Unified IP Intelligence & Session Enrichment
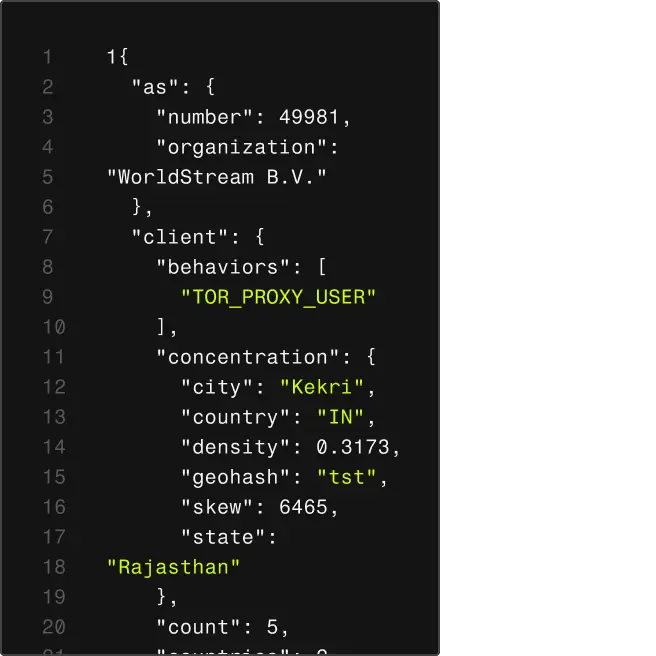
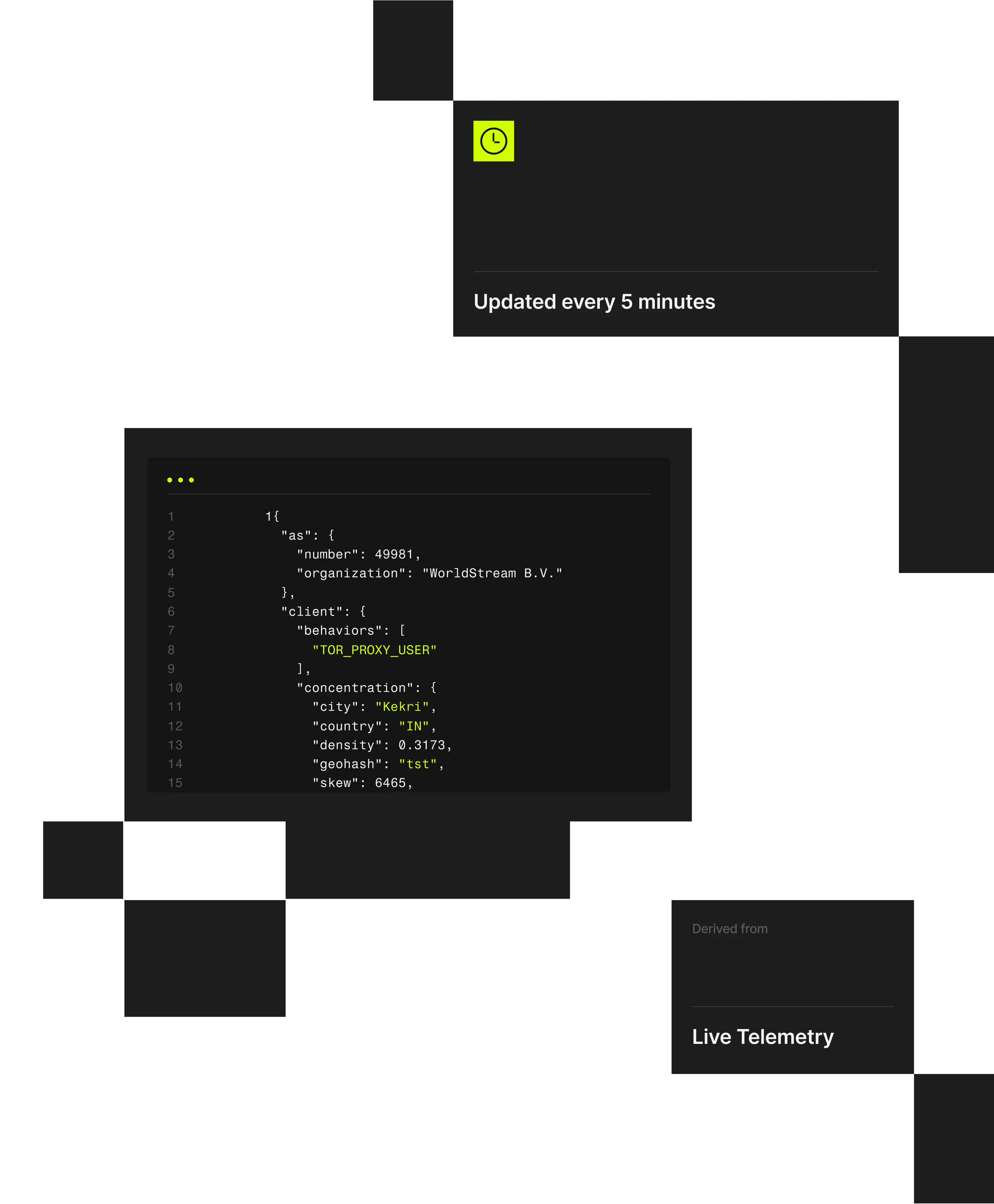
The Spur platform runs on a unified data model, ensuring consistent, explainable intelligence across all products and deployment options.
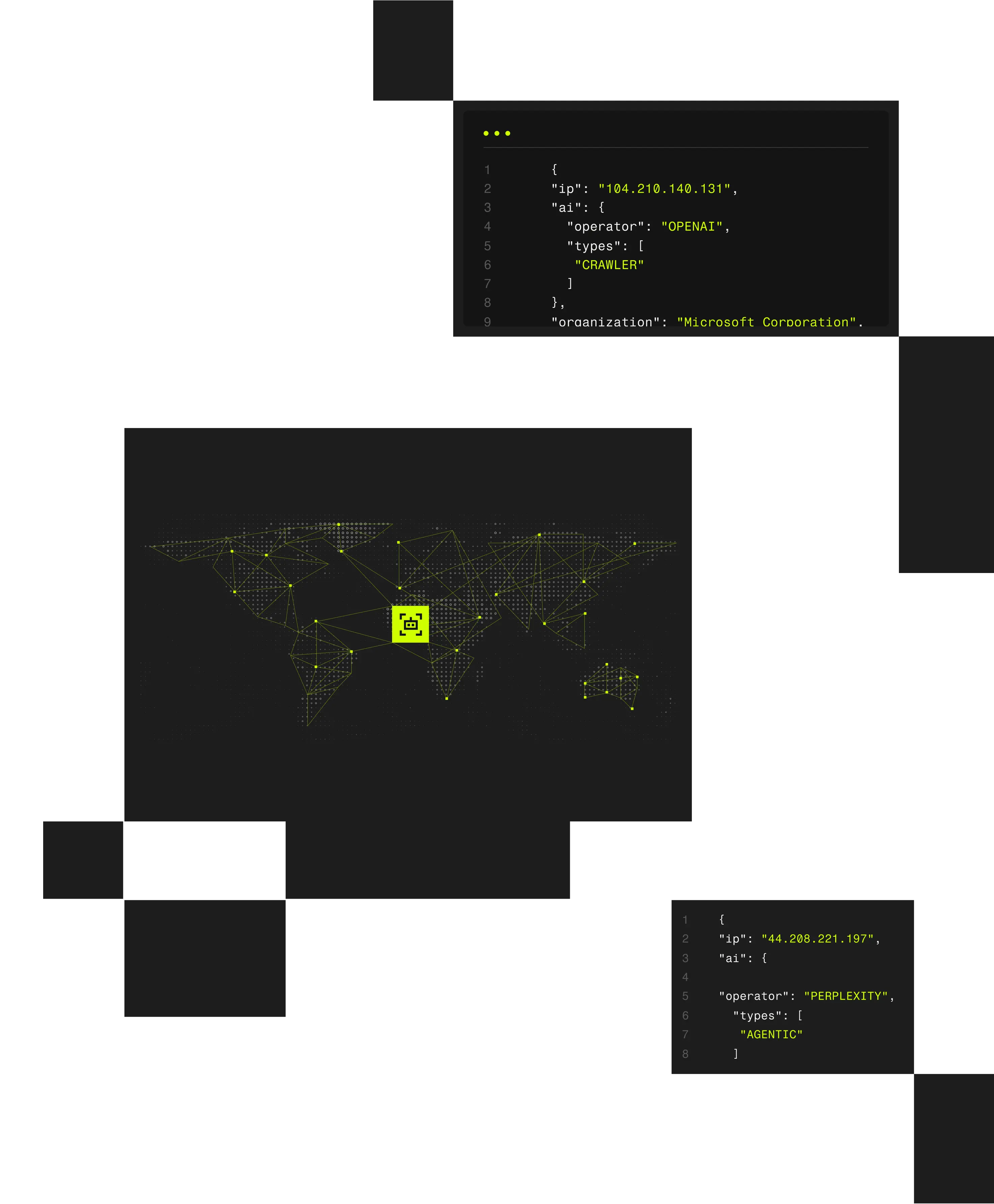
What Spur Detects
[Our Capabilities]
Unified Data Model
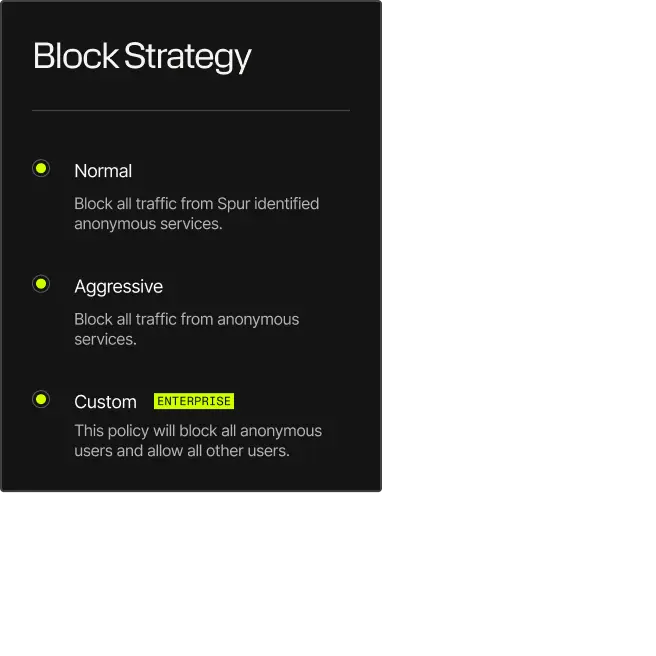
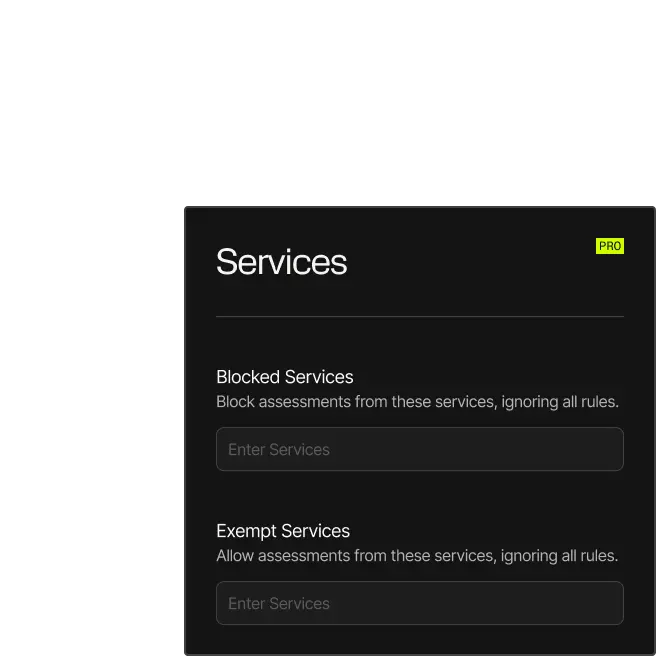
Centralized Management with Minimal Friction
Built for transparency, scale, and control, Spur platform capabilities adapt to security, fraud, and threat hunting workflows without tradeoffs.
Alerting
Escalates traffic spikes, and network anomalies, ensuring teams gain visibility into the most impactful risks.
Analysis and Reporting
Provides AI and ML-driven insights into aggregated datasets, both for local traffic and industry trends. Enables teams to visualize data that matters to them.
User Role Management
Defines roles for administrators and practitioners segmenting core platform functions, securing the environment and ensuring segregation of duties.
Token Management
Enables you to create and manage your own tokens for integrations across the corporate ecosystem, simplifying access to data.
SSO
Provides integration into single sign-on for all leading providers, supporting organizational groups and ensuring secure solution delivery.
Integrations
Delivers integrations into SIEM/SOAR tools, CDNs, and intelligence reporting solutions, enabling teams to leverage familiar toolsets for security management.
Delivery
Enables access to data via real-time website session enrichment, API calls, or daily downloads.
Content Access
Delivers seamless access to IP enrichment data across VPN/datacenter and residential proxies; AI and bot traffic; and geolocation.
Spur powers fraud, security, and threat hunting programs across industries, from fintech to enterprise security.
- Read Case Study
Financial services firm
Achieved near-zero logins from malicious actors without adding unnecessary user friction by integrating Spur data into progressive authentication flows.
- Read Case Study
Gaming company
Accurately identified 92% of anonymized services, reducing risk to player safety.
- Read Case Study
Technology company
Blocked 99.8% of fradulent sign-ups with Spur Data Feeds.
Why Teams Choose Spur.
Customer Success & Support Services
Spur offers a range of services tailored to your subscription tier. Our Enterprise offering includes:
- 01
Premium Technical Support
- 02
Priority SLAs
- 03
Dedicated Customer Success Manager (CSM)
FAQs About Spur IP Intelligence
Further Reading & Insights
Bring Clarity to Every Connection.
Detect anonymized infrastructure, validate user access, and accelerate incident response with Spur’s high-fidelity IP enrichment.