Compliance Teams. Apply Geographic and Access Controls with Confidence.
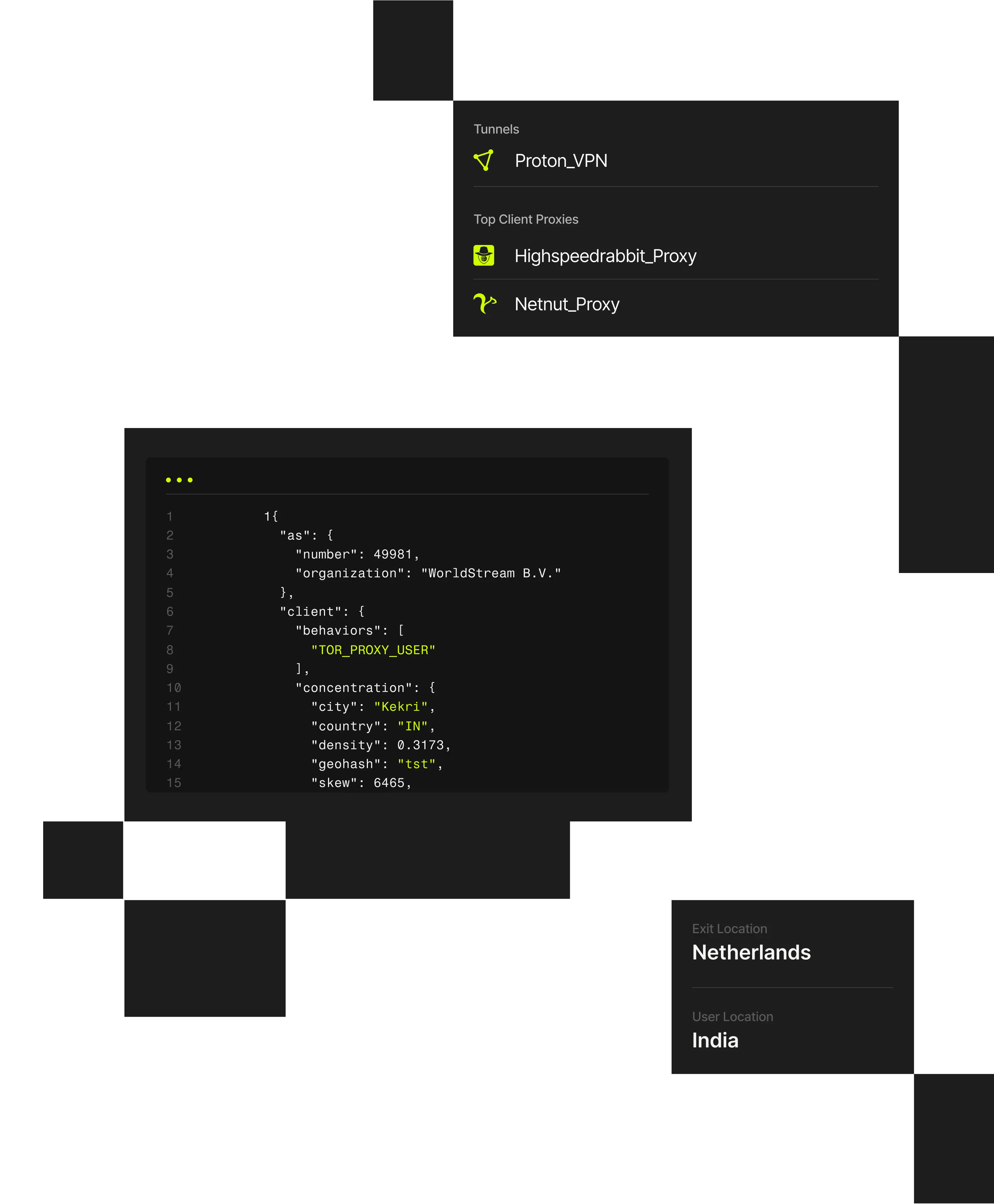
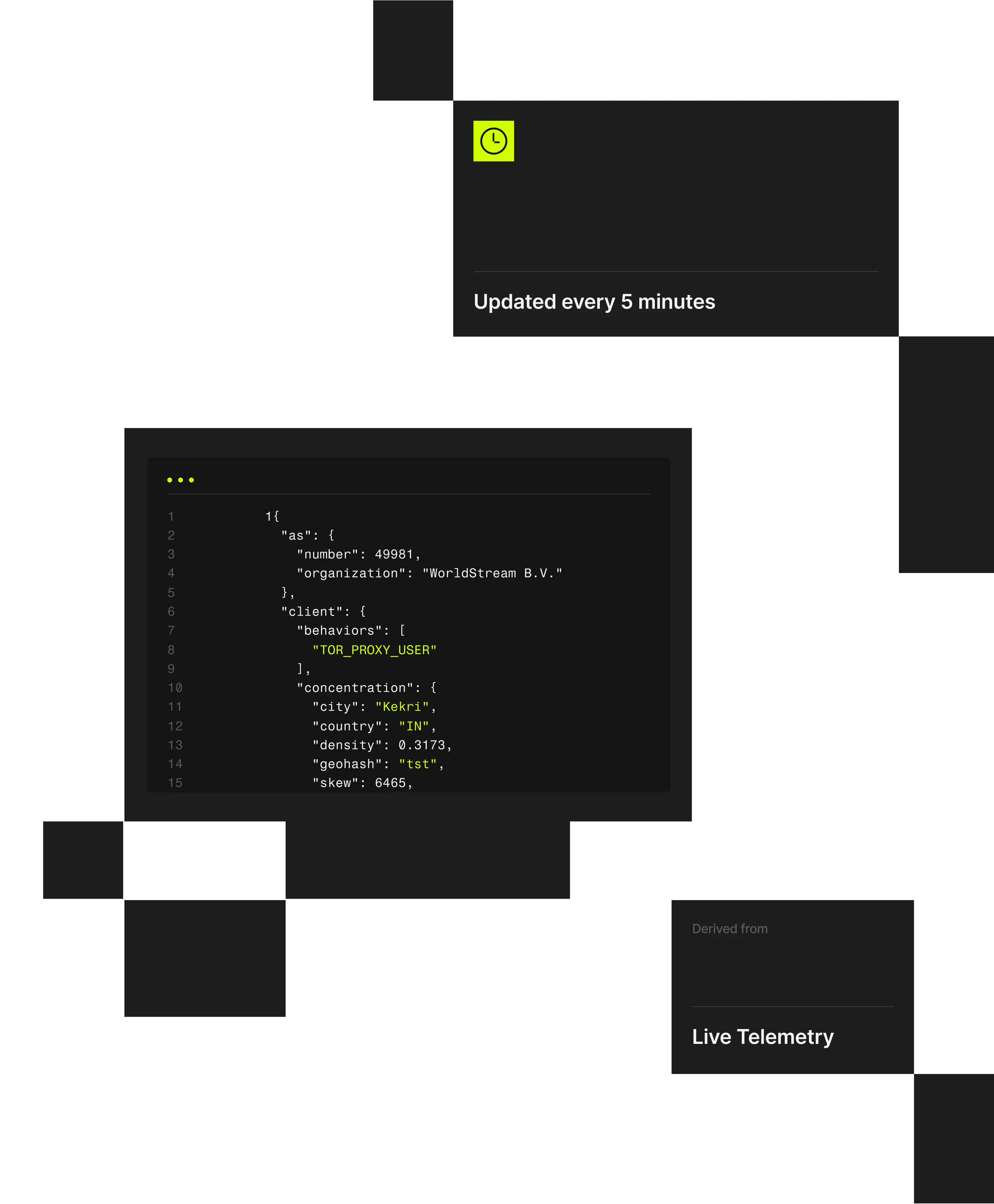
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
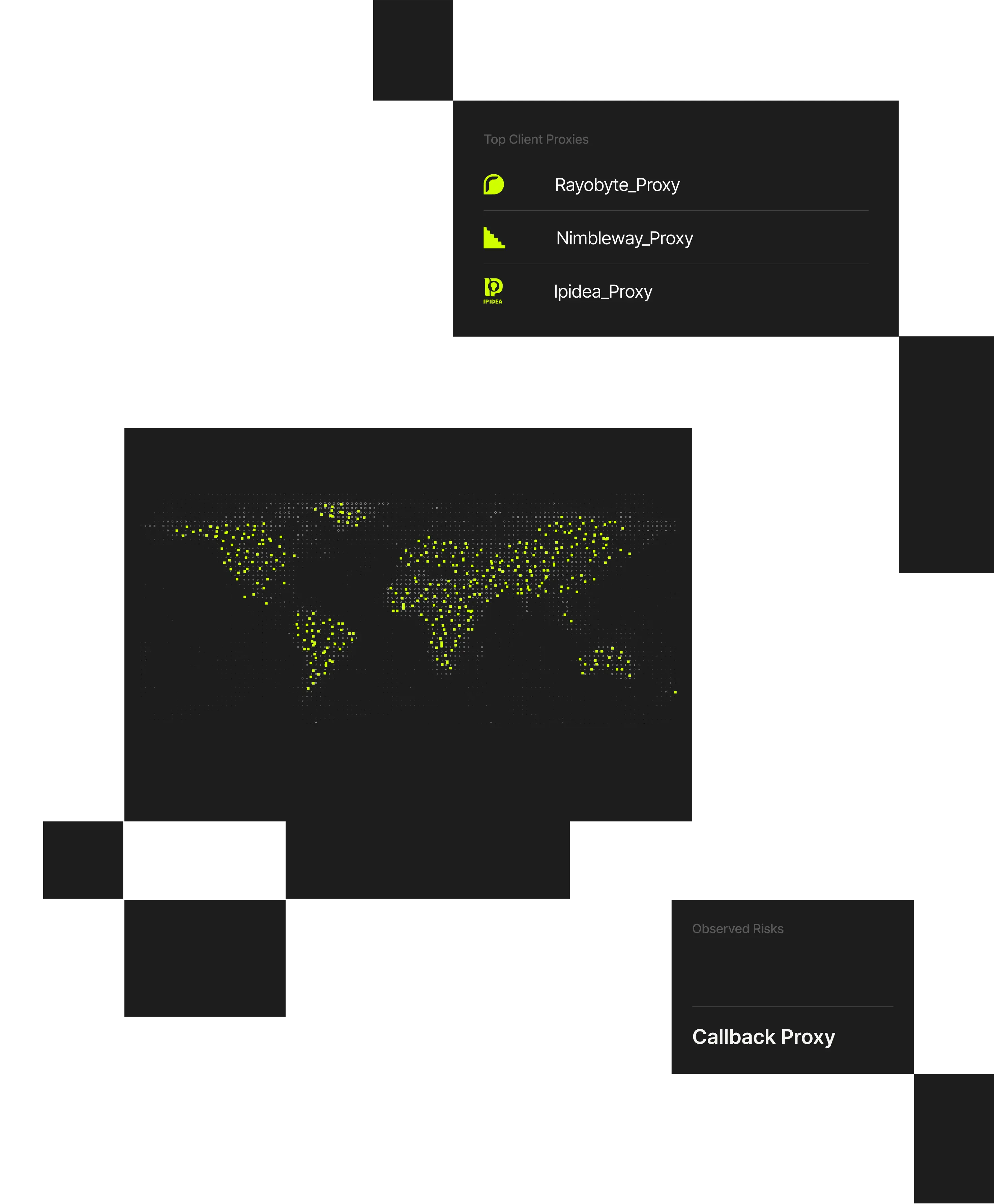
Compliance teams must ensure users are not masking their true location to bypass jurisdictional controls or regulatory requirements. Spur exposes anonymized infrastructure and validated geographic context, enabling accurate, defensible enforcement without relying on self-reported or opaque data.


Compliance Controls Break Down Behind Masked Geography.
Regulatory and policy enforcement depends on knowing where users are actually accessing systems from. However, VPNs, proxies, and anonymized routing enable users to misrepresent location while appearing compliant to basic controls. This creates risk for platforms handling sensitive content, financial operations, or regulated access.
Spur provides infrastructure-aware IP intelligence and validated geolocation that help compliance teams identify location spoofing, apply controls accurately, and demonstrate that enforcement decisions are auditable and defensible.

Verify Geography and Enforce Regional Restrictions Confidently.
Spur delivers infrastructure-aware IP intelligence and validated geolocation that help compliance teams apply geographic and access controls accurately, document decisions clearly, and withstand audit or regulatory scrutiny.
What Security Frameworks and Regulations Say About Anonymized Traffic.
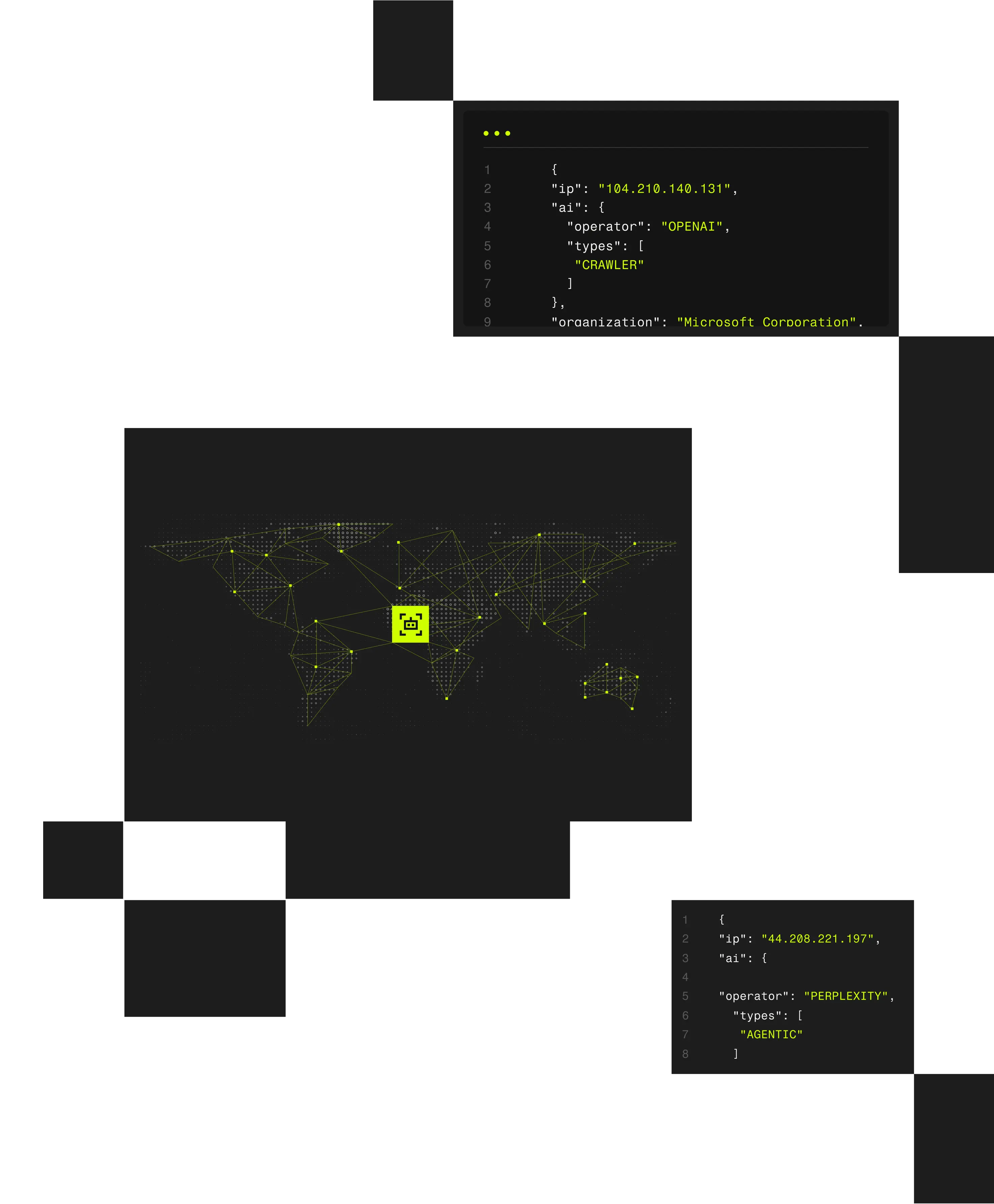
Anonymized traffic creates compliance and monitoring challenges across security and regulatory frameworks.
This post examines how common standards govern VPN and proxy use, when IP addresses are treated as PII, and how organizations can balance regulatory requirements with sound security and governance practices.
Evidence You Can Act On.
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
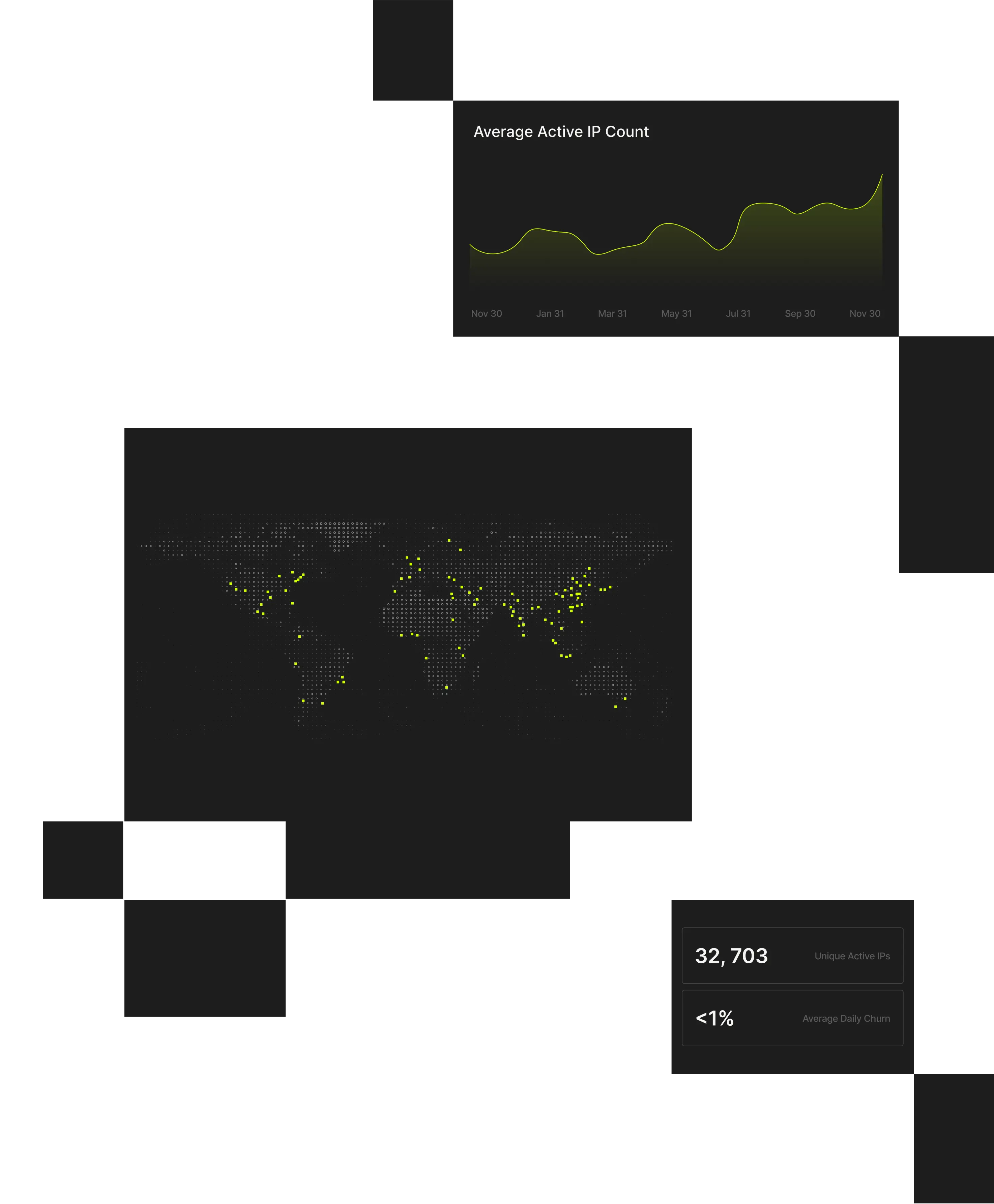
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
1000+
VPN and proxy services detected
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Strengthen Every Team’s Visibility with Verified IP Intelligence.
Apply Compliance Controls with Confidence.
Detect anonymized access, validate geographic context, and support defensible compliance decisions with infrastructure-aware IP intelligence built for modern regulatory environments.