IP Intelligence API.
Implement real-time IP enrichment at scale.
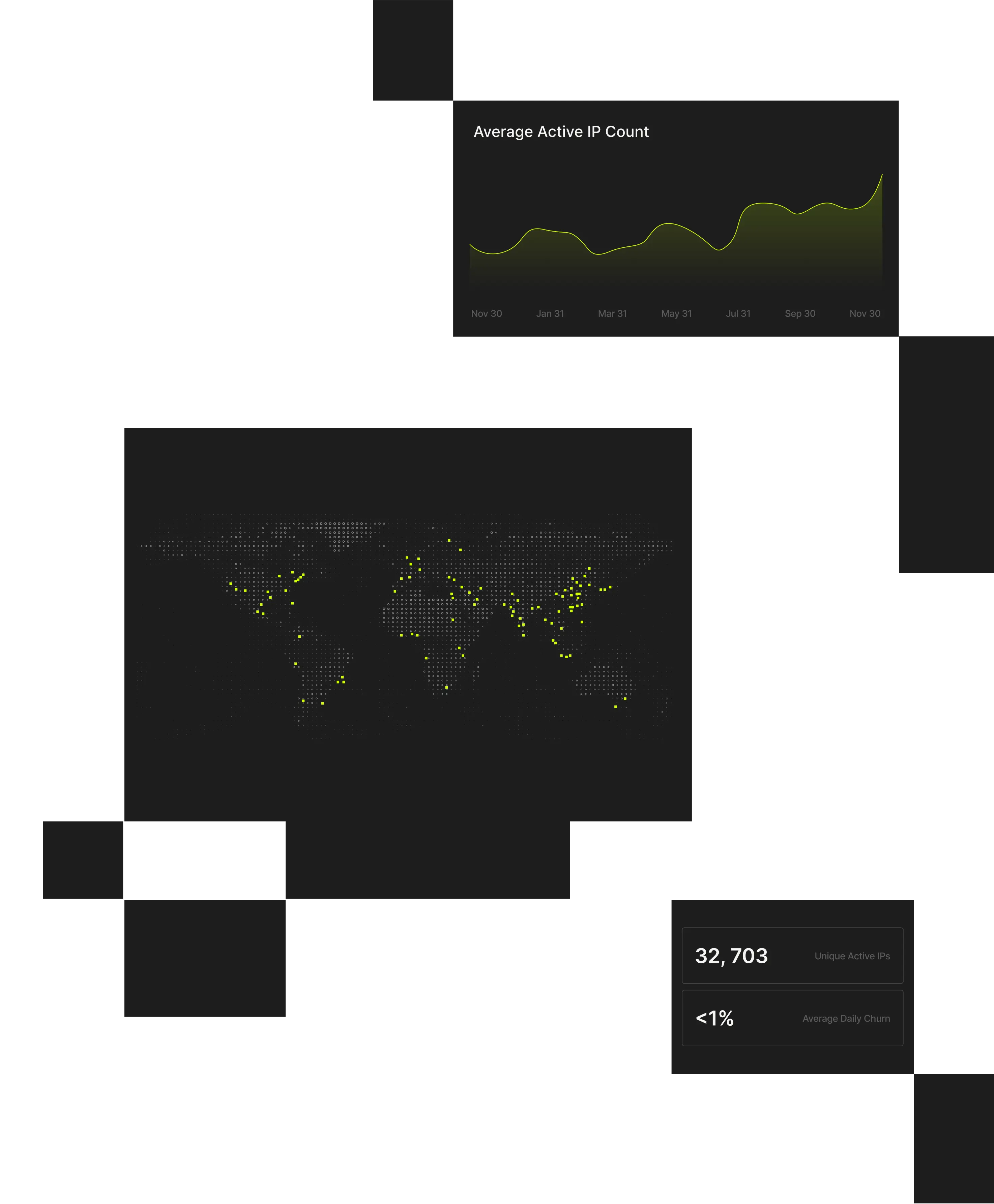
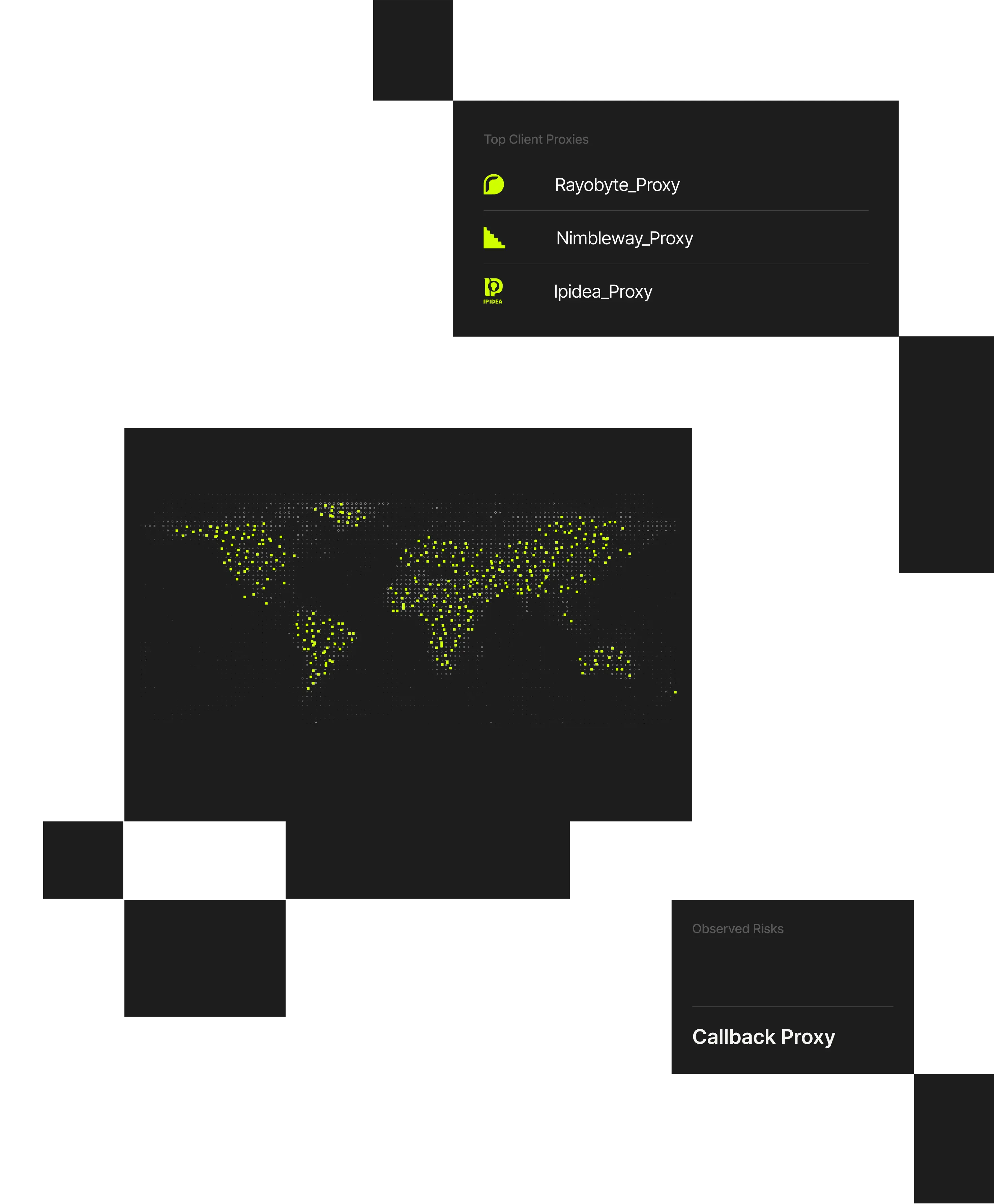
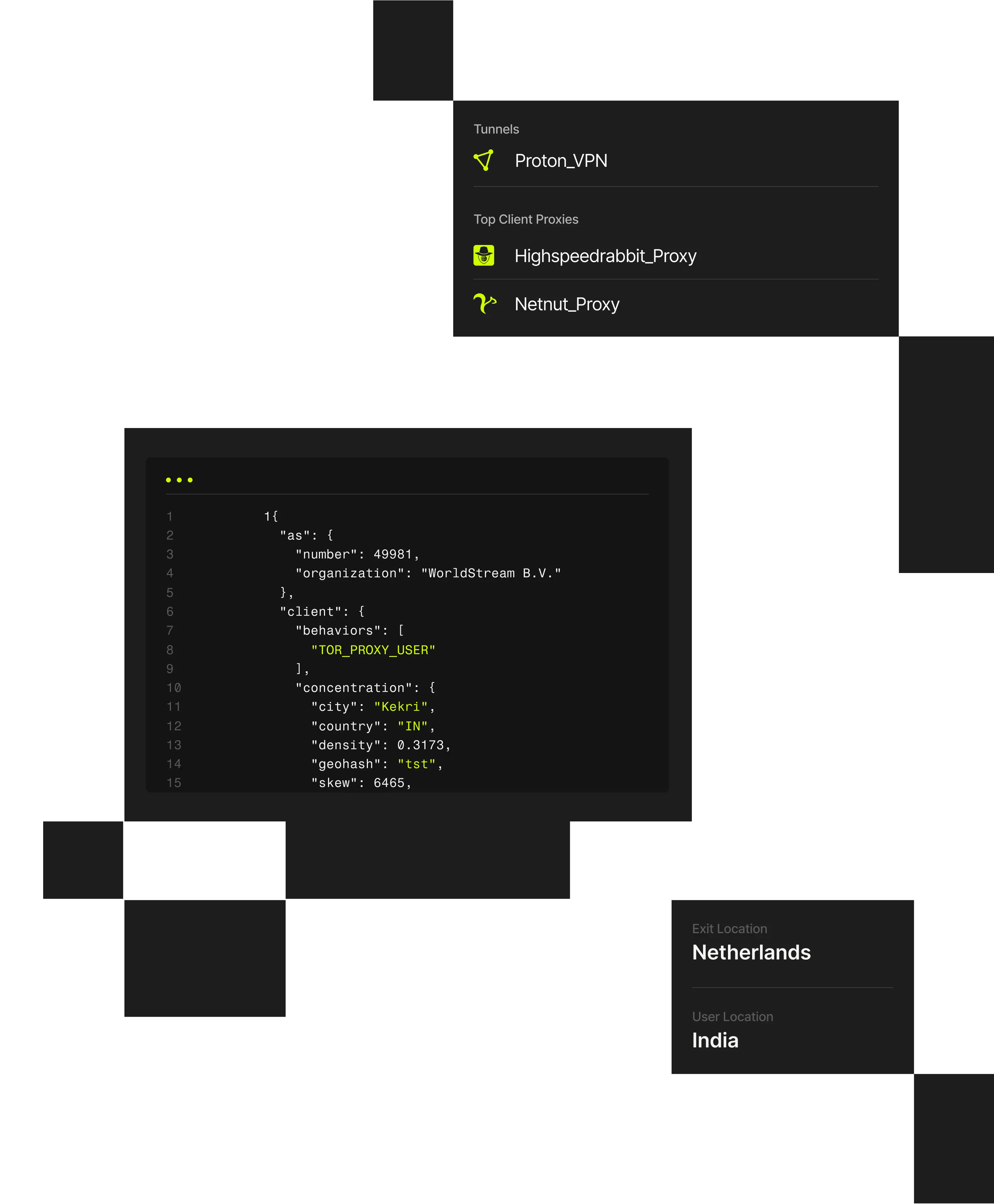
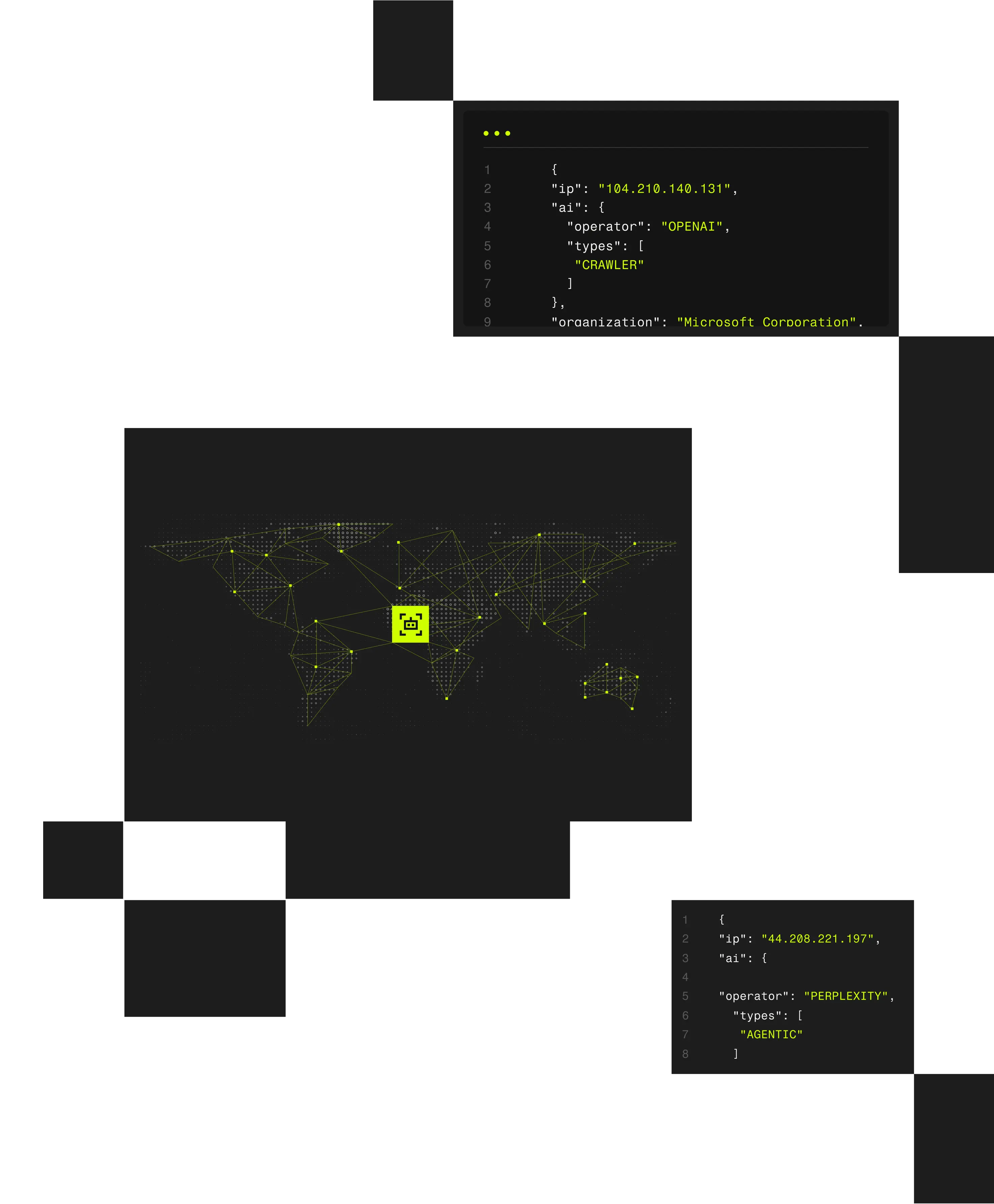
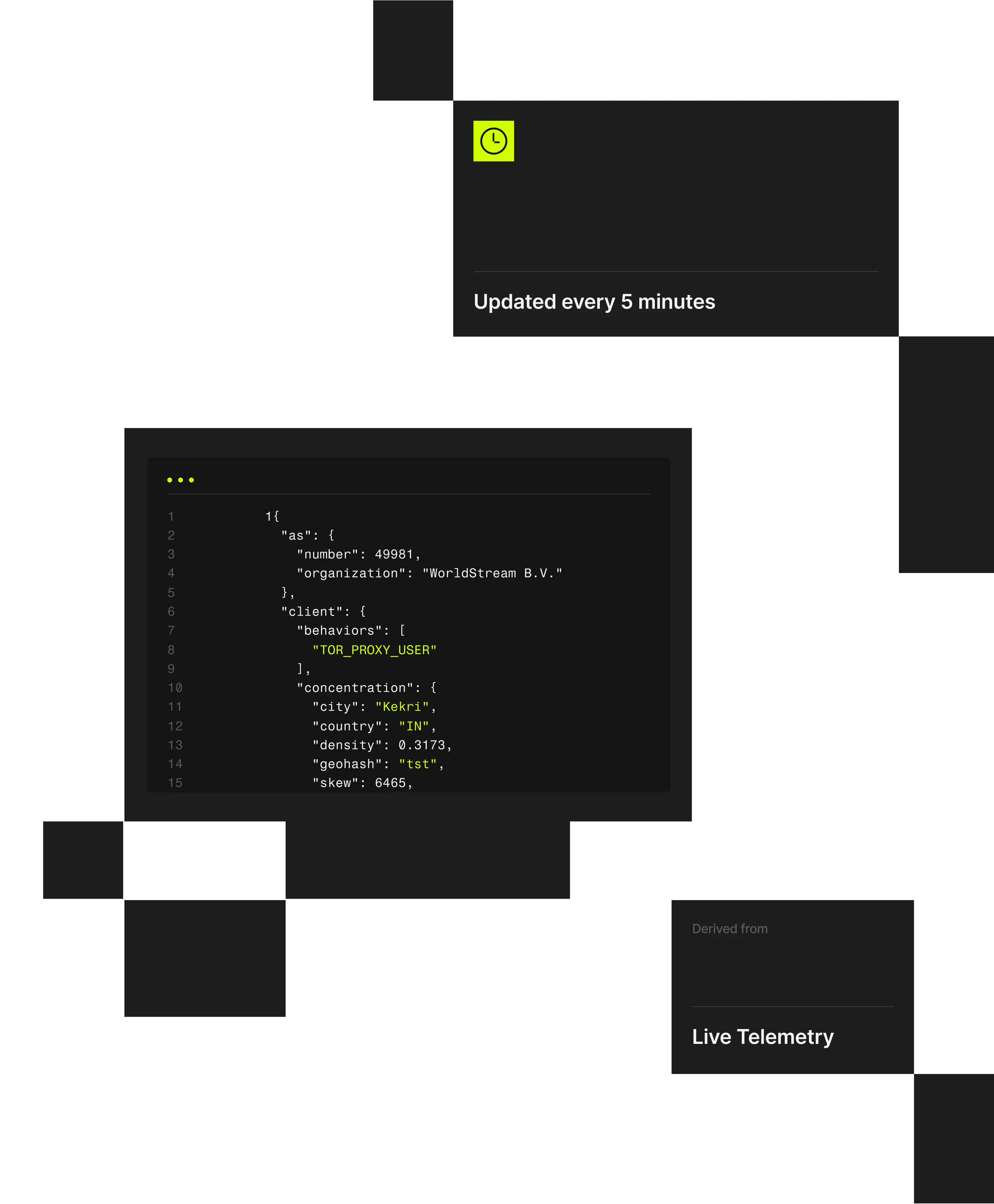
Spur Context API transforms raw IPs into actionable intelligence in milliseconds, delivering verified, explainable context where it matters most.
Spur Context API provides hosted IP enrichment lookups of the highest-fidelity IP intelligence available. With pre-built integrations into the most common threat analysis platforms and services, Spur ensures that security teams can instantly leverage data to protect their environments from the latest evasion and obfuscation methods.
Static IP reputation lists can’t keep pace with dynamic infrastructure. Spur API provides instant, explainable enrichment for every connection, enabling inline fraud detection and access control without latency or opaque scoring.
Key Benefits:
- Enrich IPs in milliseconds to detect anonymized, proxy, or high-risk traffic in real time.
- Correlate signals across authentication, fraud, and investigation workflows.
- Integrate directly into existing security and fraud systems using a RESTful interface or SDKs.
- Enable flexible IP enrichment workflows with a consumption-based model.

How The Spur API Delivers IP Intelligence to Your Systems
- 01
Query:
- 02
Enrich:
- 03
Return:
Why Teams Choose Spur Context API
Where the Spur API Delivers Value
Trusted by Teams Who Need to See What’s Real.
- Read Case Study
Technology Company:
Reduced fraudulent signups by enriching traffic with real-time VPN and proxy detection.
- Read Case Study
Financial Institution:
Reduced account takeover risk by integrating real-time IP enrichment into login workflows.
- Read Case Study
Security Operations Team:
Improved attribution by enriching alerts with VPN, proxy, and infrastructure context via API.
FAQs About Spur Context API
Add Real-Time IP Intelligence to Your Workflows.
Discover how real-time IP enrichment brings clarity and control to security, fraud, and threat hunting workflows.