Government Agencies. Detect masked threats across public systems.
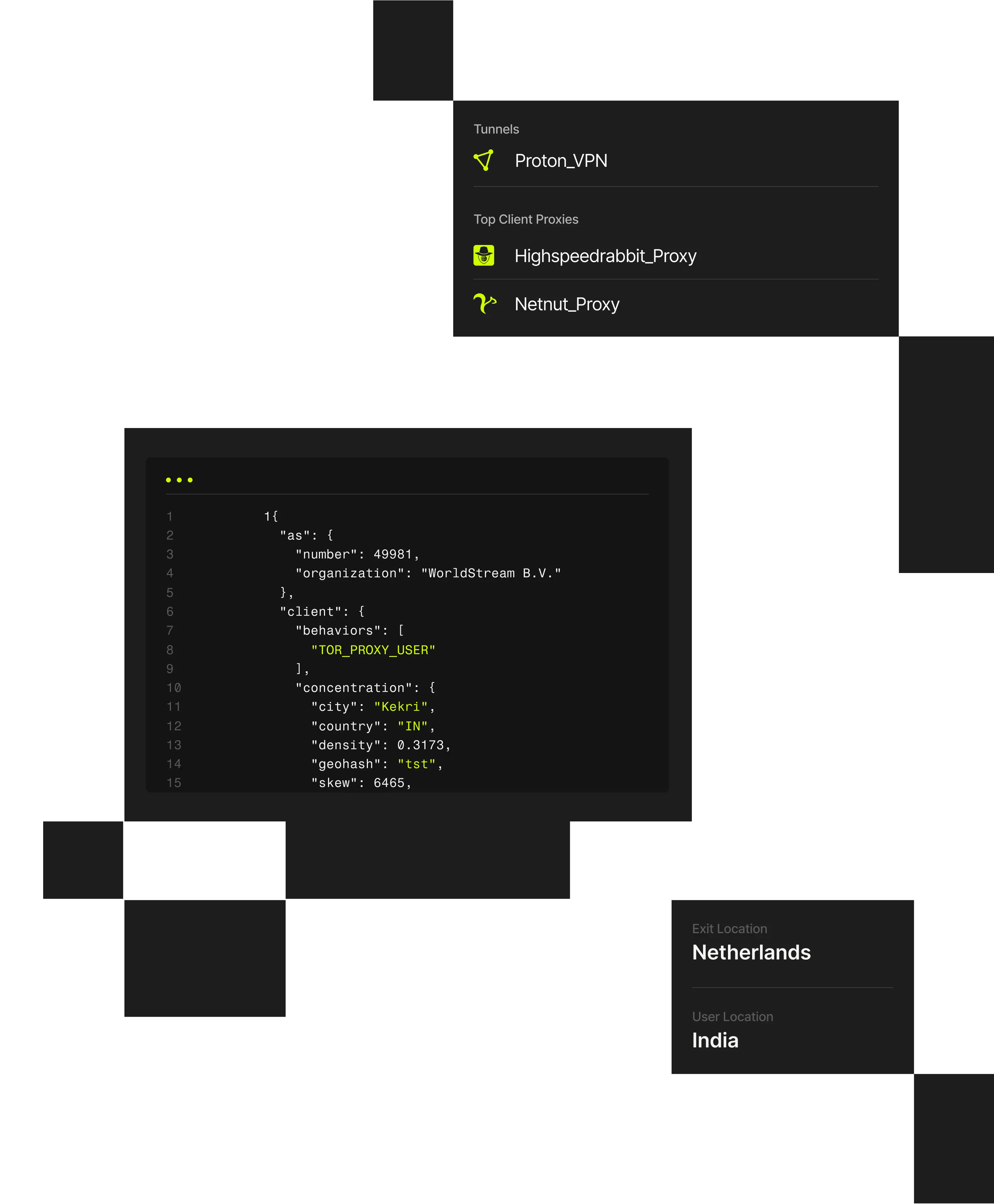
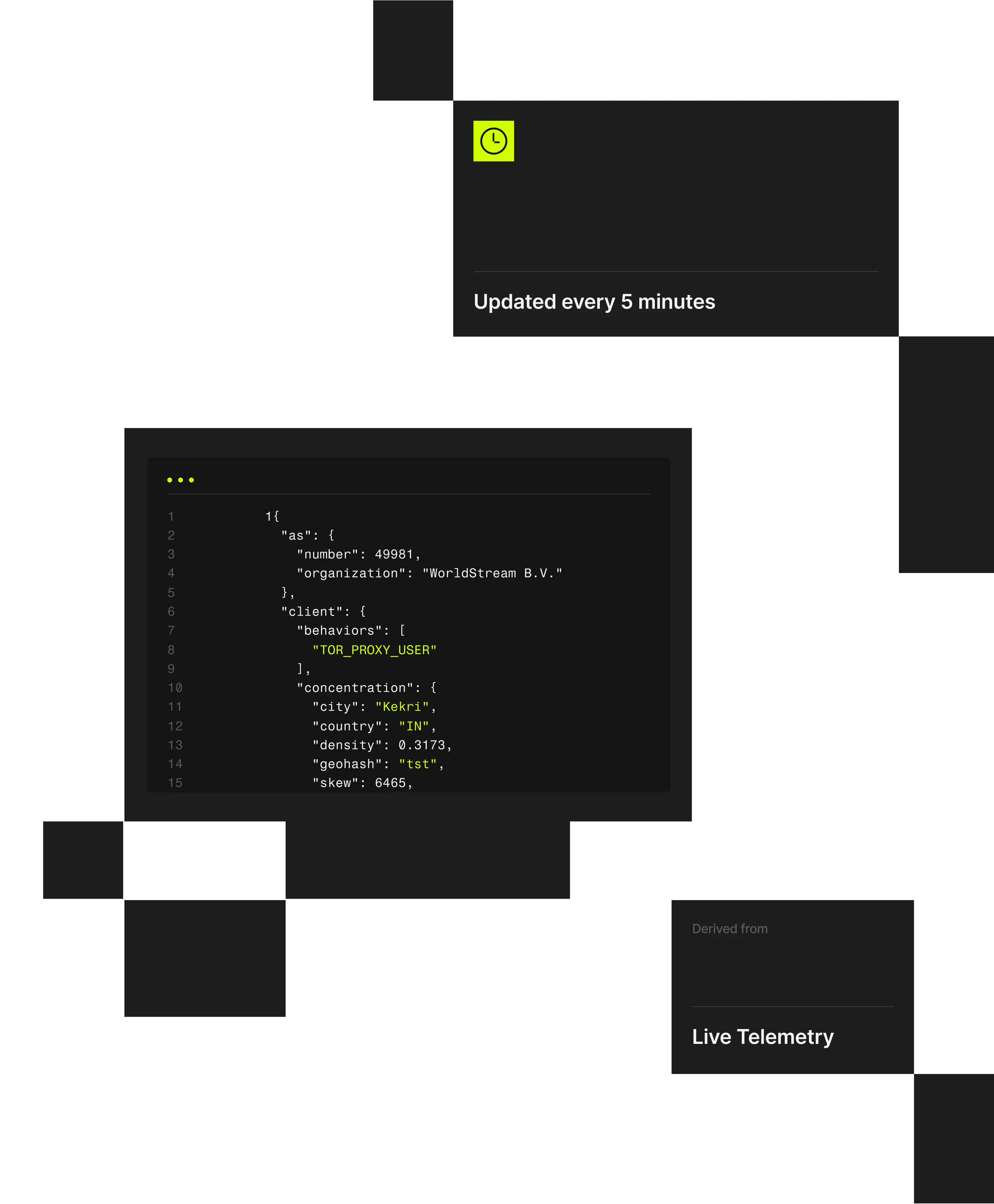
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
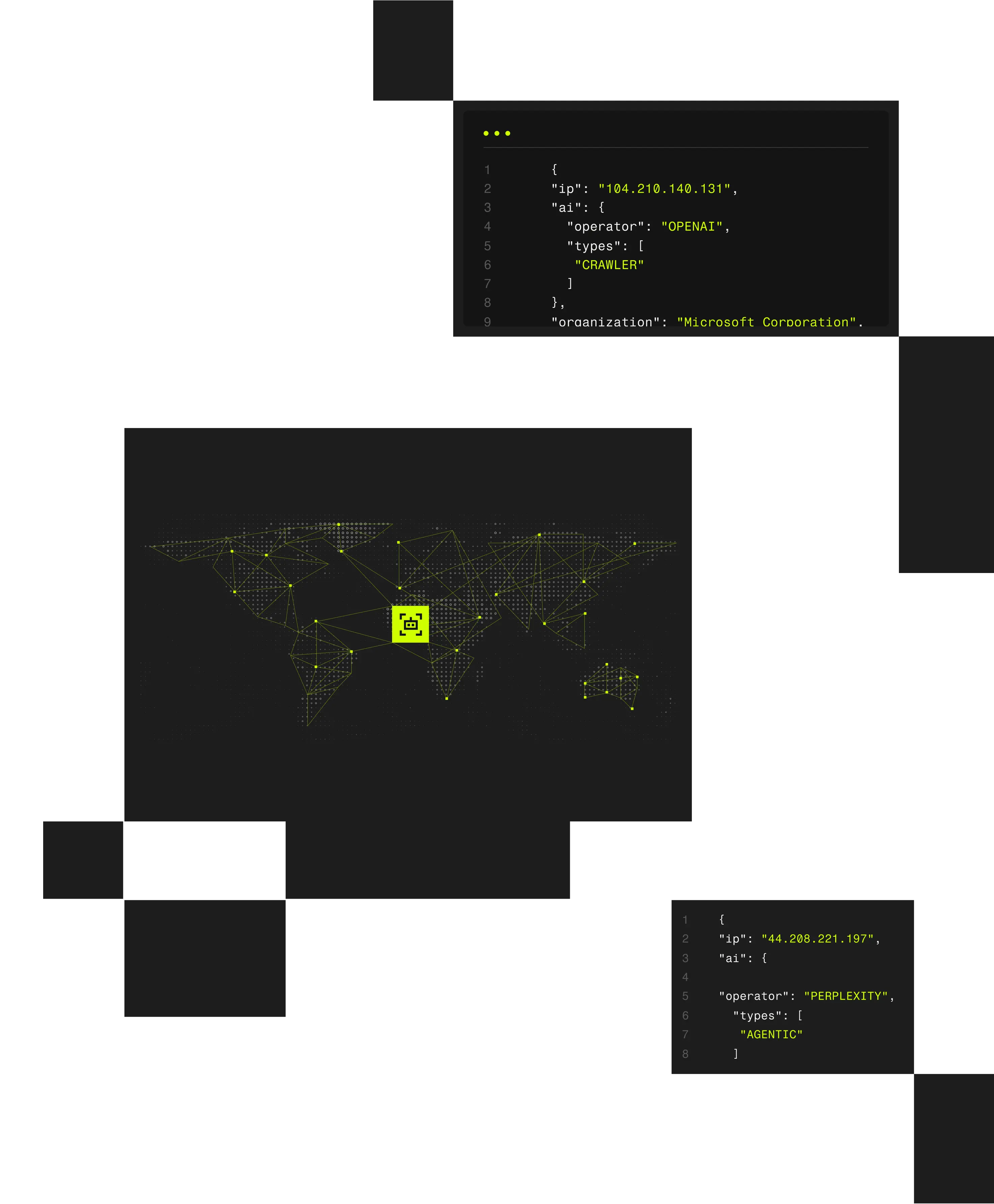
Government agencies face persistent cyber threats, fraud, and abuse targeting public-facing systems and services. Spur exposes anonymized infrastructure behind user activity, helping agencies detect threats, protect systems, and maintain trust without disrupting legitimate access.


Anonymized Access Obscures Threats to Public Systems.
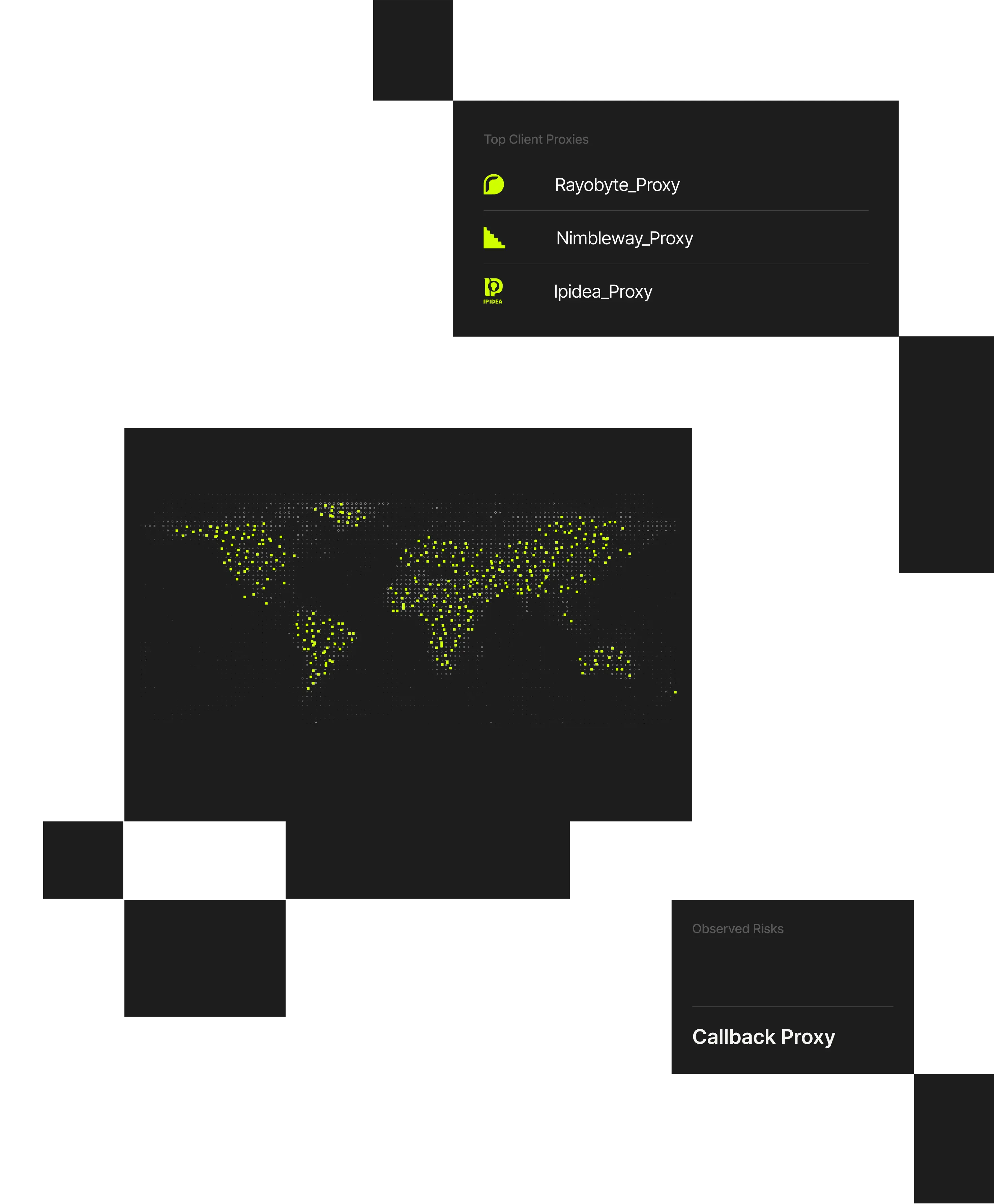
Government agencies operate critical services that must remain accessible while defending against cybercrime, fraud, and state-aligned activity. Attackers use VPNs, residential proxies, and shared infrastructure to conceal reconnaissance, abuse public benefits, and bypass geographic or rate-based controls.
When malicious activity blends into normal access patterns, detection and investigation become difficult. Spur provides infrastructure-aware IP intelligence that helps agencies identify masked access, correlate activity, and strengthen security and fraud controls across public systems.

Detect Fraud, Identify Threats, and Protect Public Systems.
Spur provides infrastructure-aware IP intelligence that helps government agencies detect masked threats, prevent fraud and abuse, and protect public-facing systems while preserving access for legitimate users.
Evidence You Can Act On.
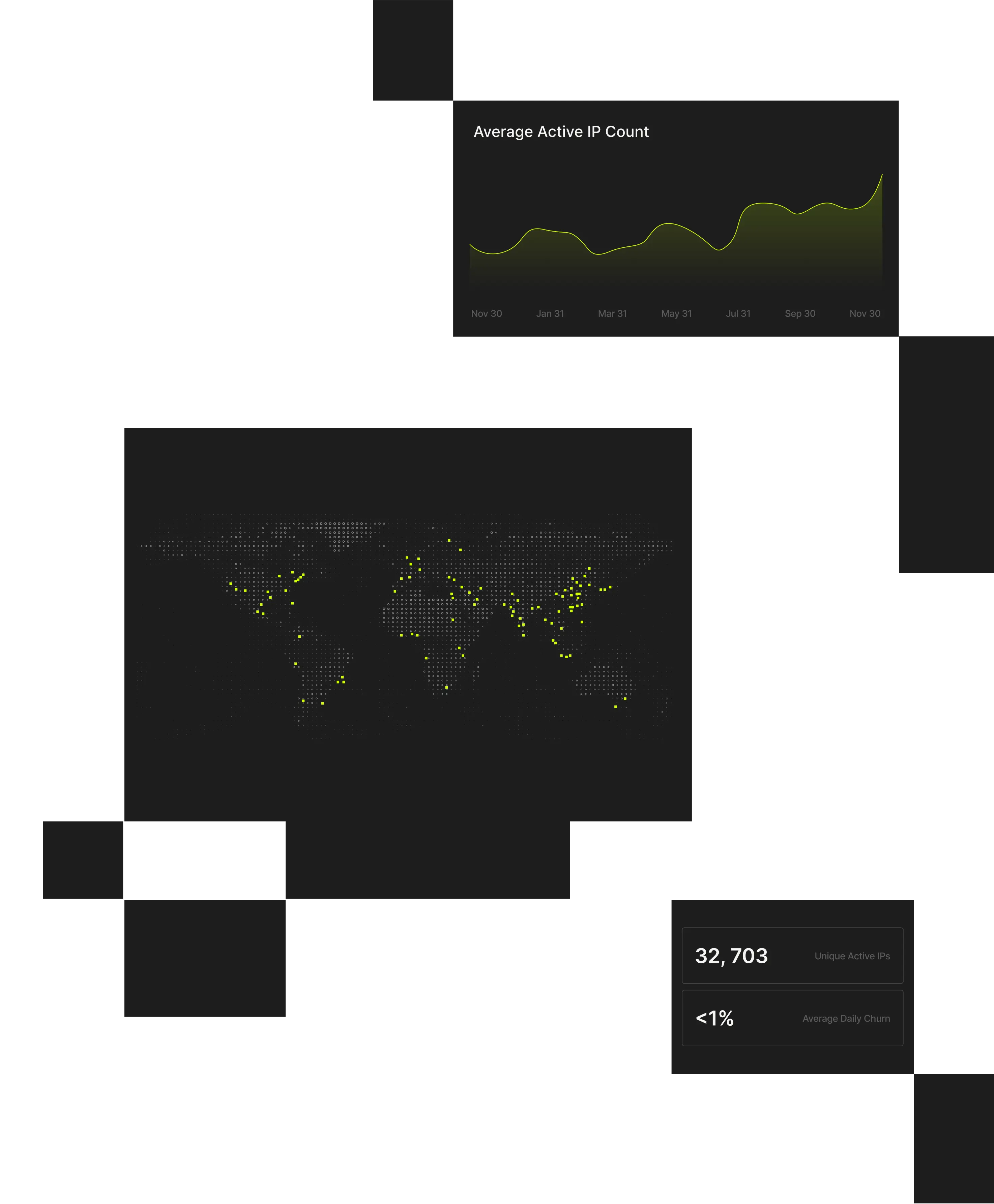
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
1000+
VPN and proxy services detected
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Reveal the truth hiding in plain sight across the sectors Spur protects.
Protect Public Systems with Greater Visibility.
Detect anonymized access, uncover coordinated abuse, and support investigations across public-facing systems with infrastructure-aware IP intelligence built for government environments.