Stop Account Takeovers (ATO). Expose Risky Login Infrastructure.
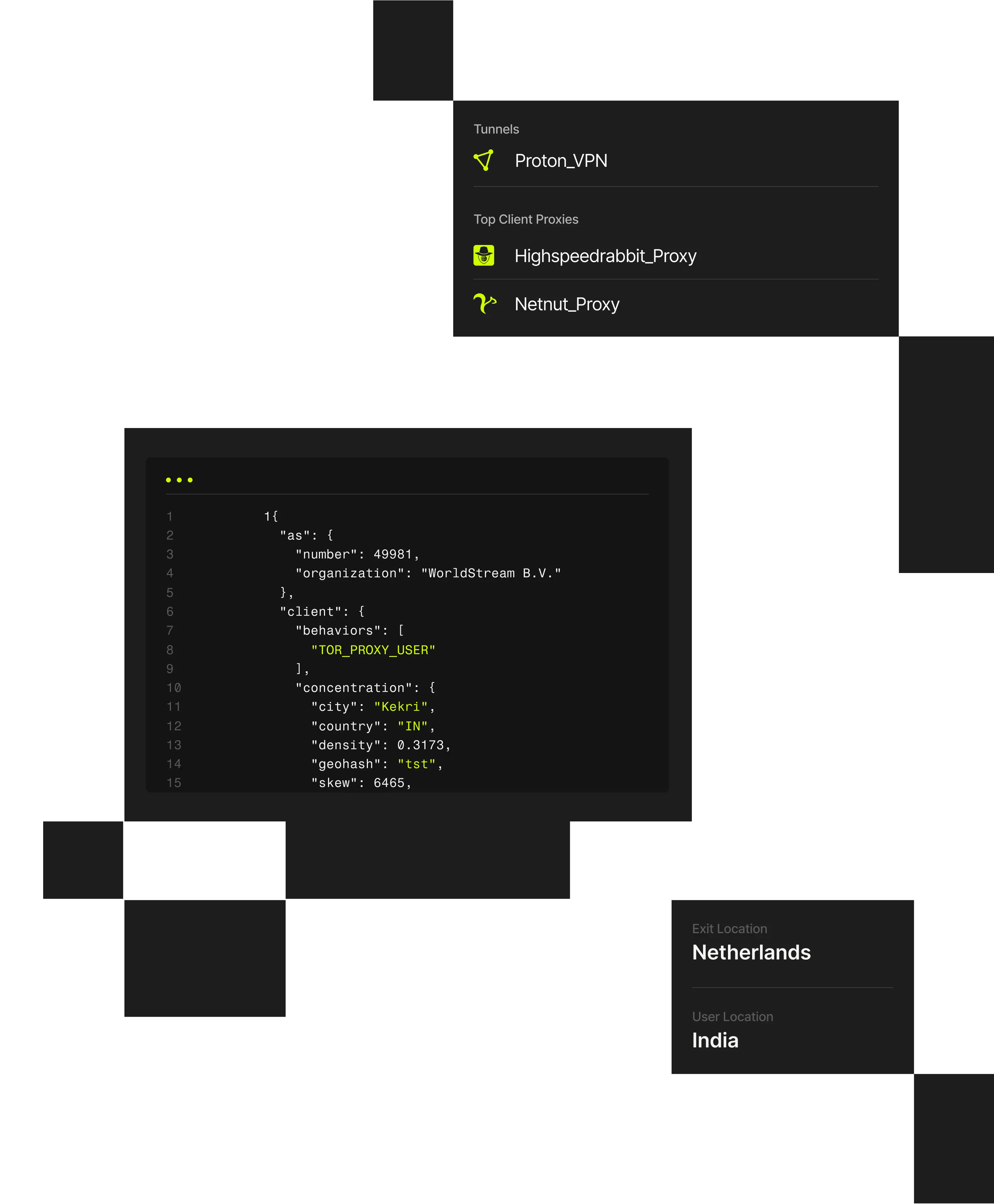
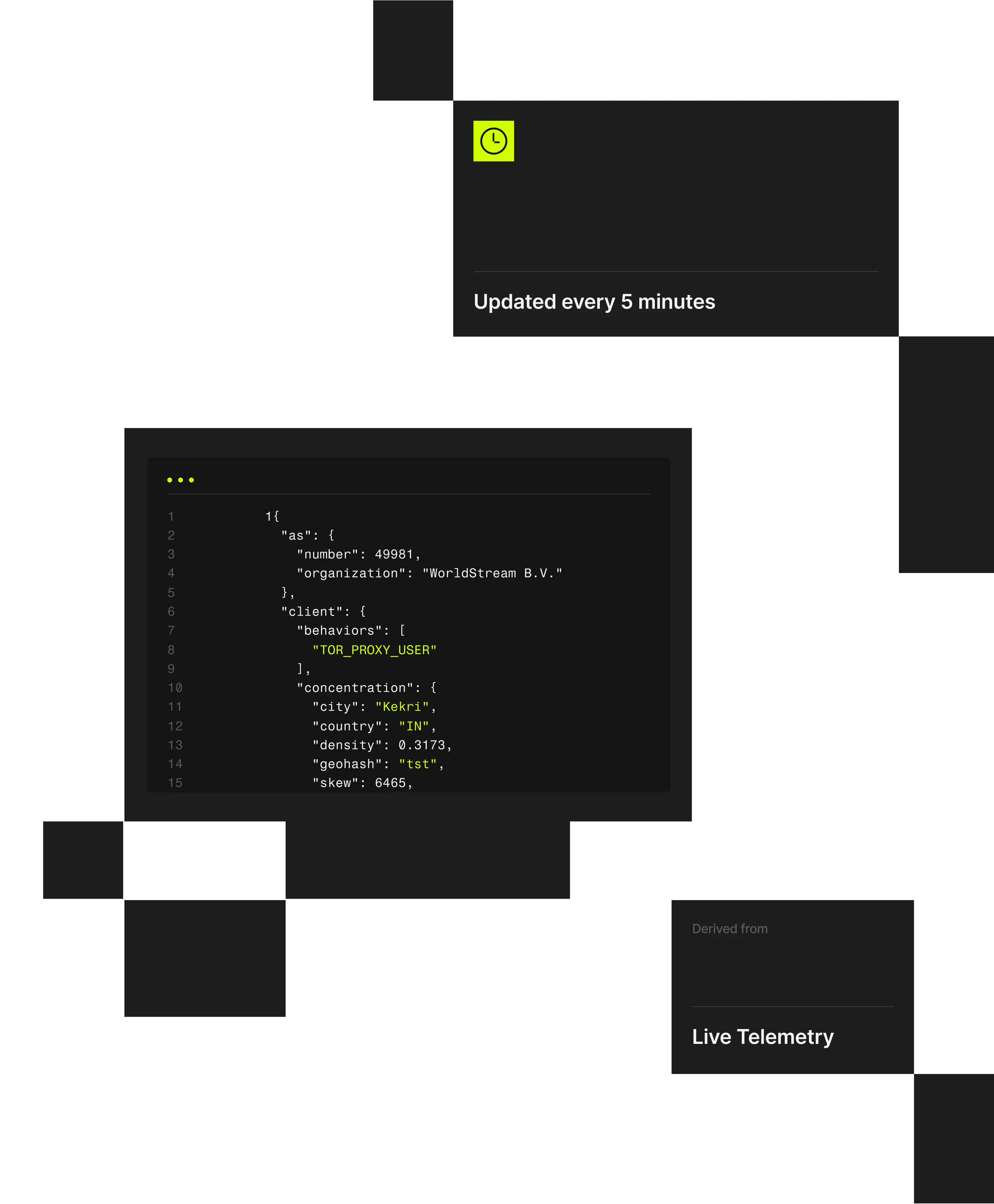
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
Account takeover attacks combine stolen credentials with VPNs, residential proxies, and automation to make malicious logins appear legitimate. Spur adds high-fidelity IP intelligence to authentication workflows, helping teams detect and disrupt ATO attempts without unnecessary friction.


Modern ATO Campaigns Exploit Anonymized Infrastructure.
Modern authentication defenses often fail not just because credentials are weak, but because attackers hide abusive login activity behind anonymized infrastructure. When login decisions lack network context, teams are forced to rely on blunt controls that increase friction for legitimate users.
Spur enriches authentication events with infrastructure intelligence, enabling more accurate risk assessment and proportional controls at the point of login.

How Spur Reduces Account Takeover Risk.
Spur delivers high-fidelity IP intelligence that strengthens authentication decisions, detects ATO patterns, and enables proportional defenses against anonymized login abuse.
Financial Institution Reduces ATO By Over 40%
A financial institution reduced successful account takeovers by more than 40% by incorporating high-fidelity IP intelligence into its authentication workflows.
By identifying VPN- and proxy-backed login attempts and applying targeted controls, the institution disrupted ATO campaigns without increasing friction for legitimate users.
Evidence You Can Act On.
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
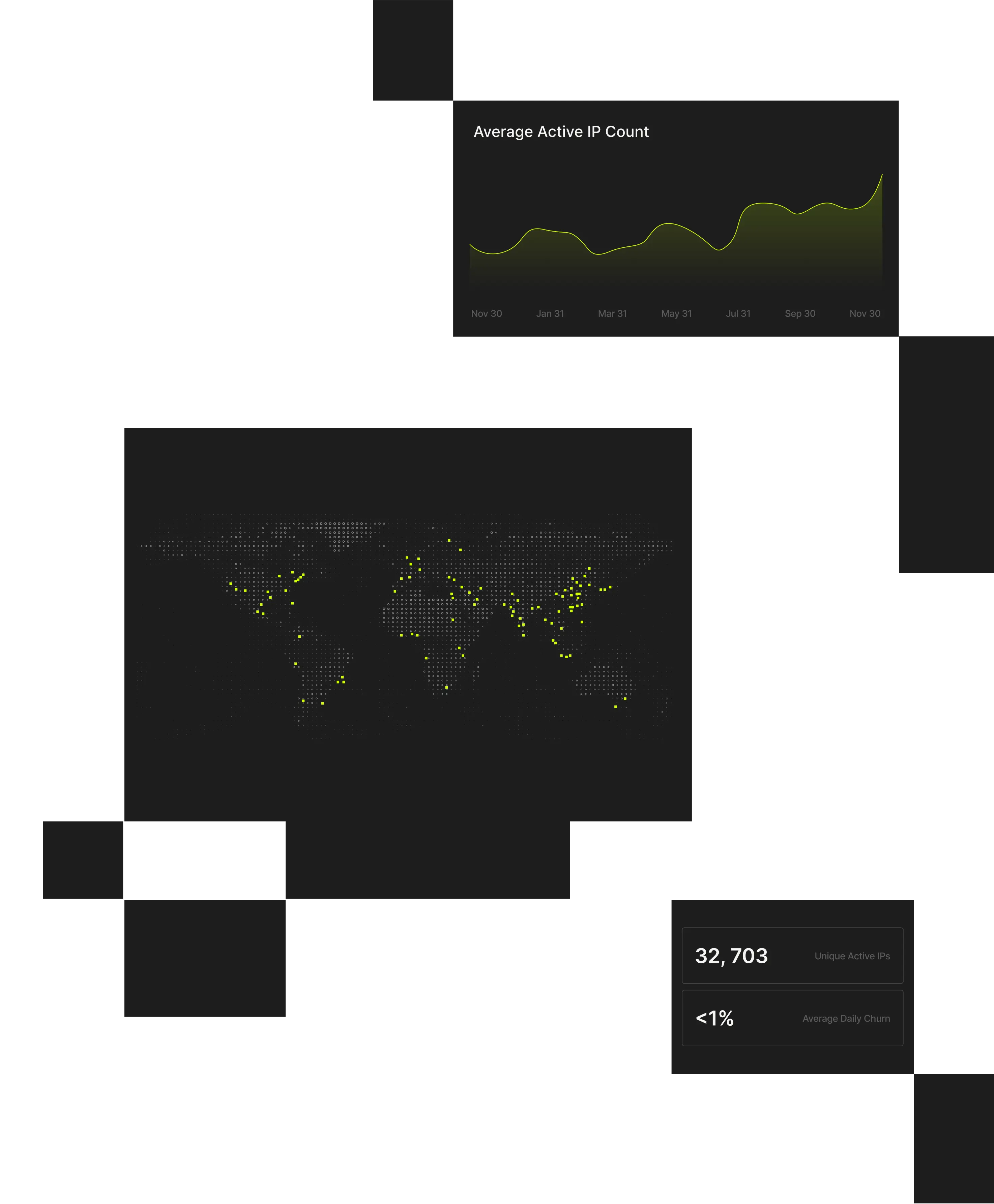
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
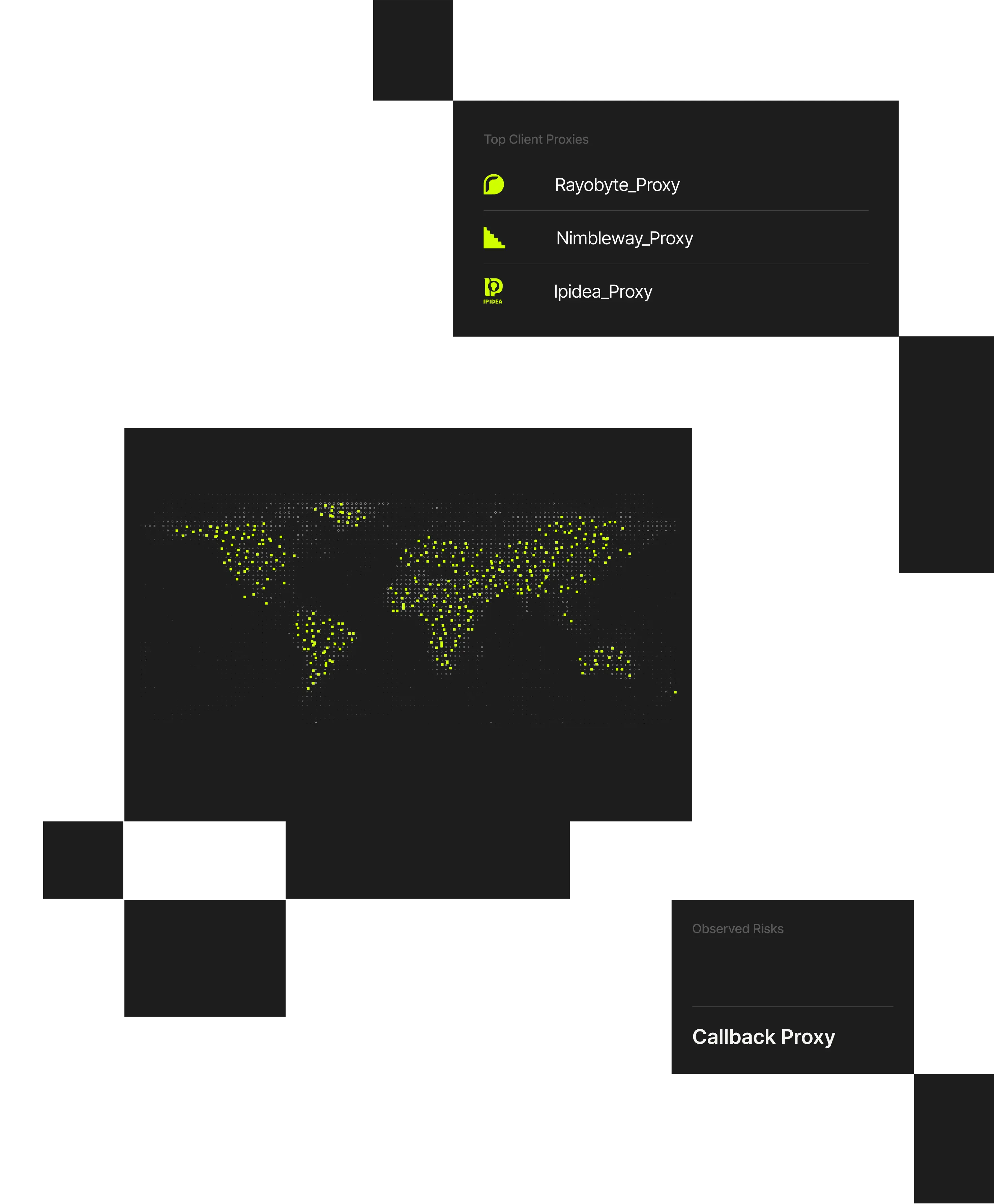
1000+
VPN and proxy services detected
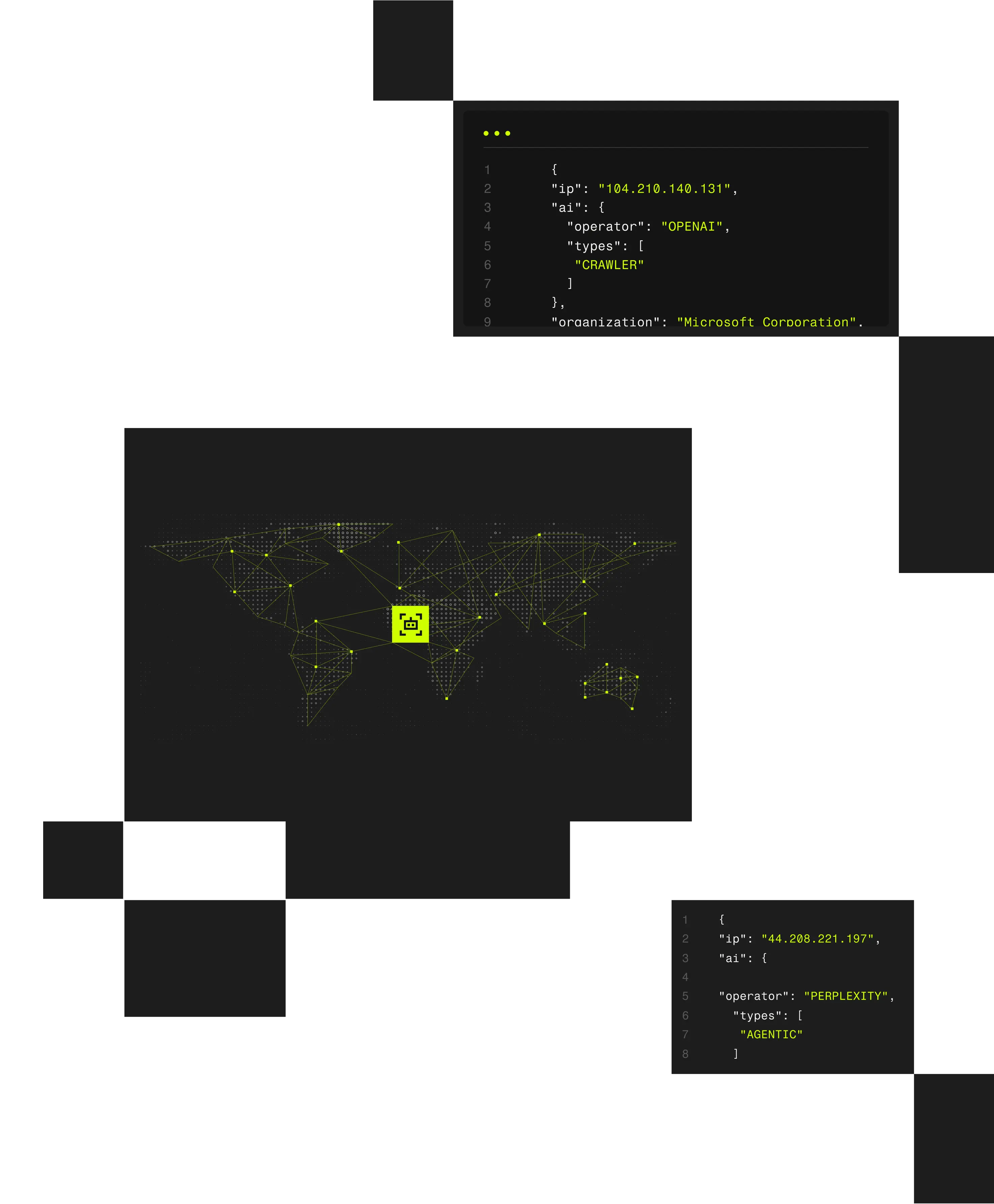
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Where Spur Strengthens Every Layer of Defense.
Disrupt ATO Campaigns Without Added Friction.
Identify anonymized login attempts, detect distributed credential abuse, and strengthen authentication decisions with high-fidelity IP intelligence.