Prevent Fraudulent Account Creation. Expose Fraud at Signup.
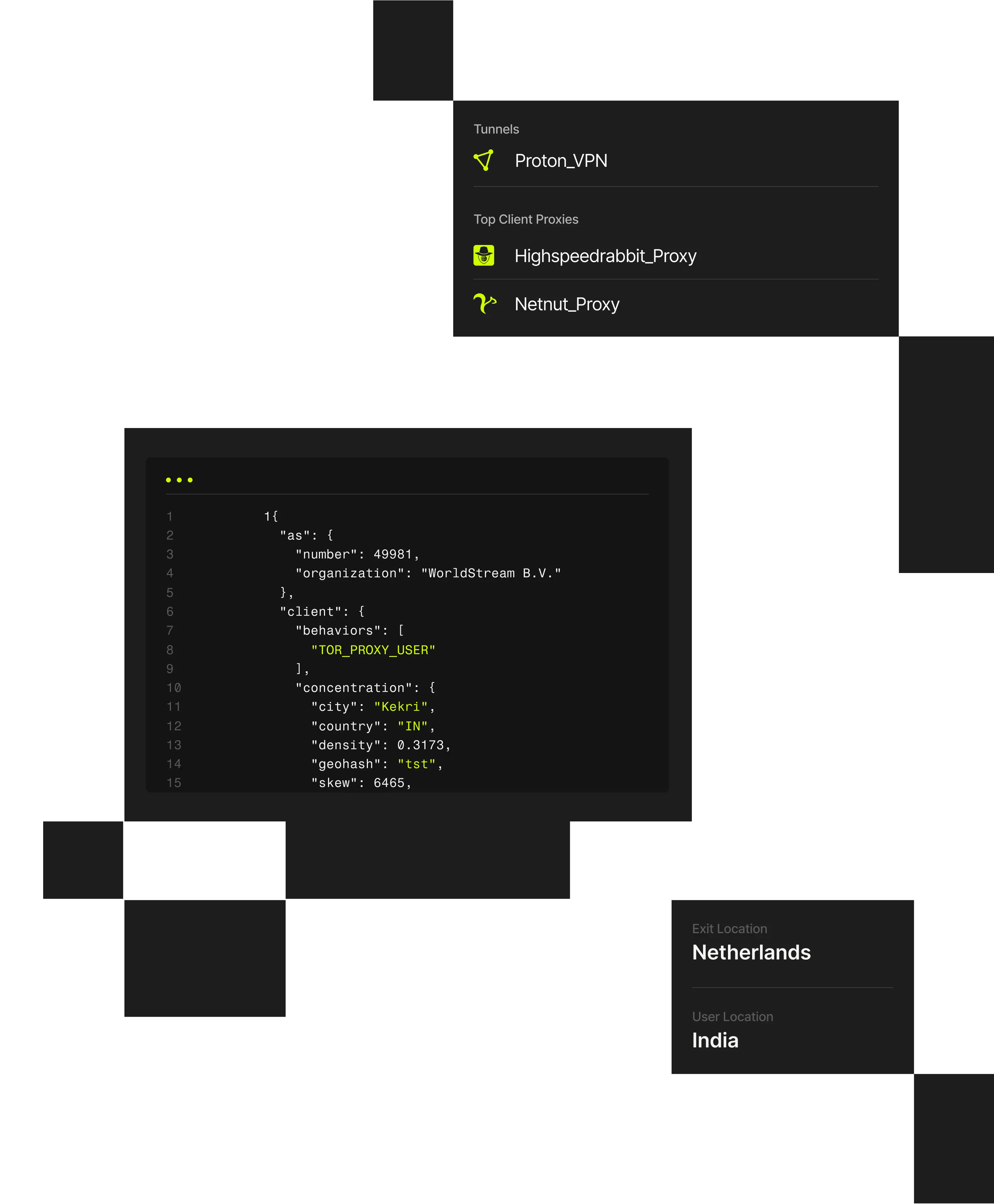
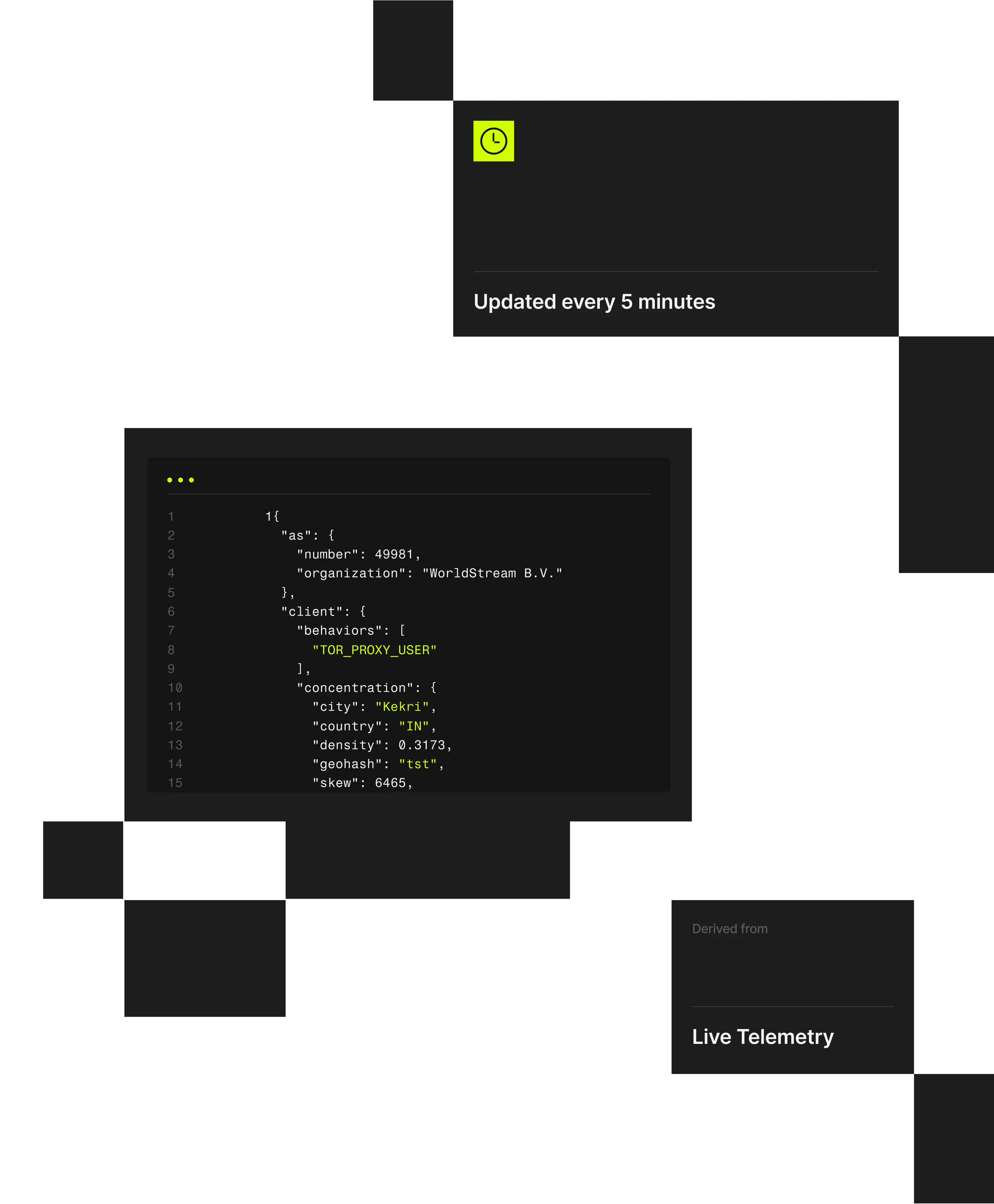
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
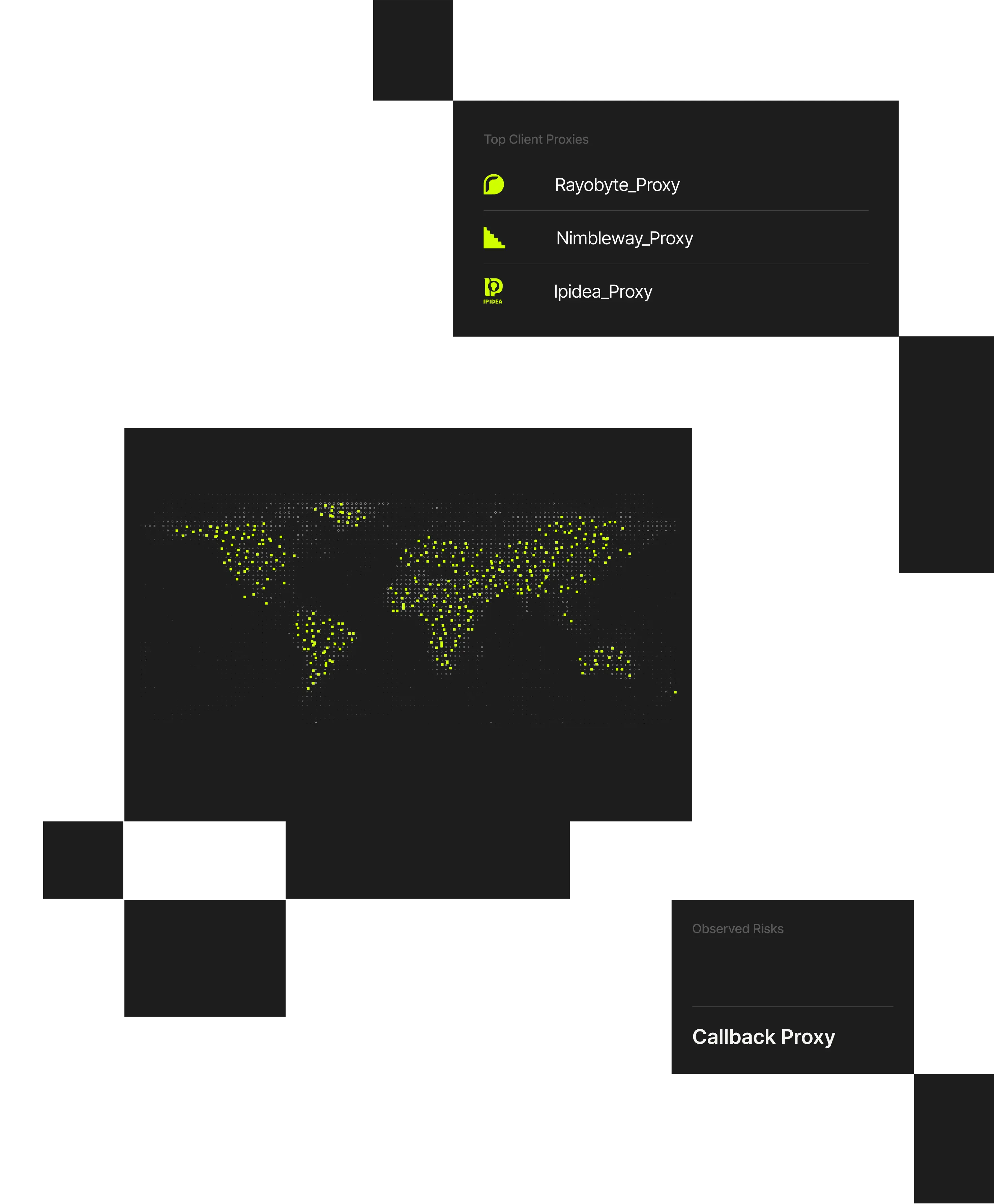
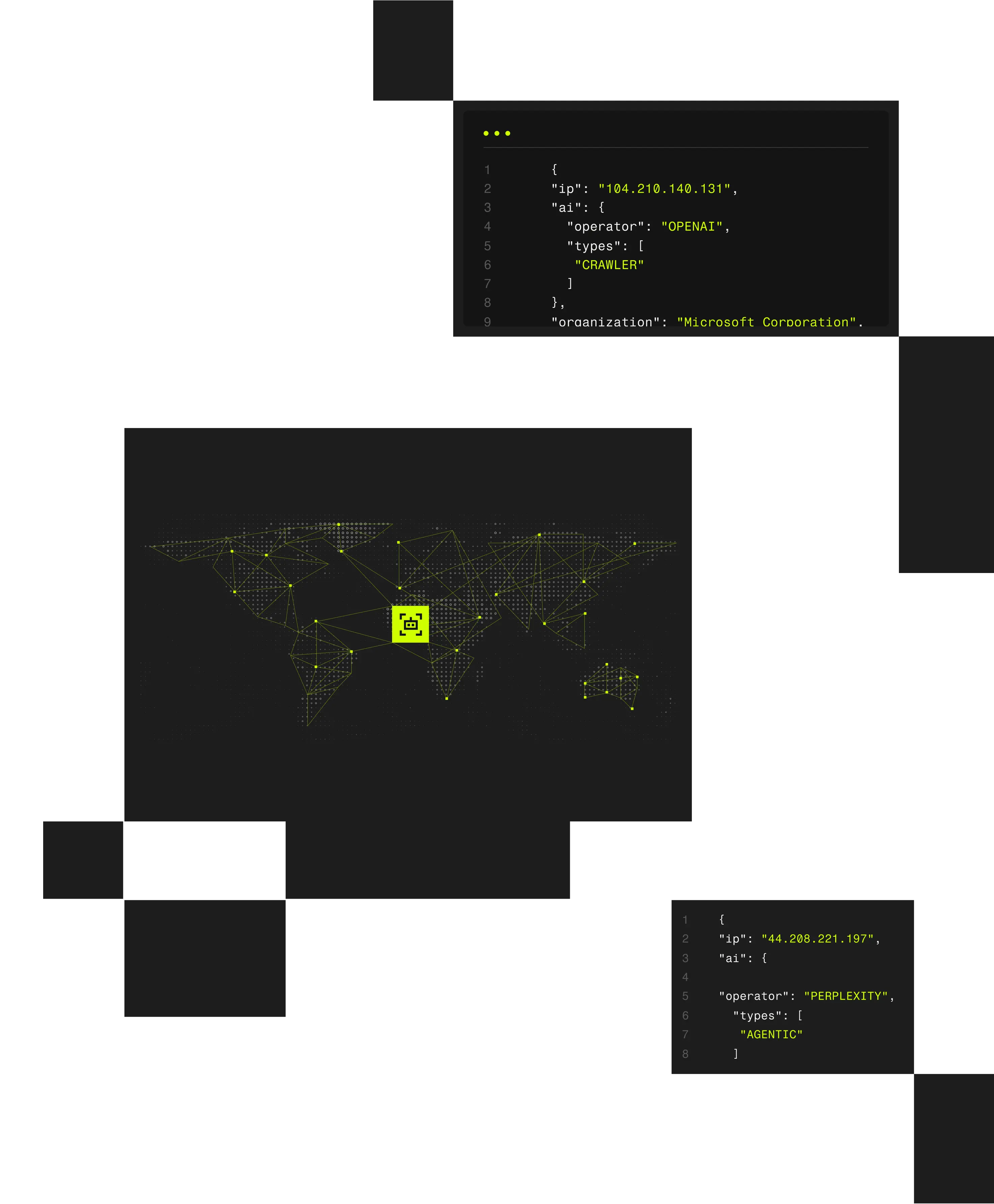
Fraudulent account creation is driven by attackers using residential proxies, VPNs, and automated infrastructure to make fake signups appear legitimate. Spur reveals the anonymized infrastructure behind signup activity so teams can stop abuse before accounts are created.


Fraud Hides Behind Legitimate-Looking Signups.
Digital businesses depend on open registration flows to drive growth, but those same flows are a primary entry point for abuse. As attackers automate account creation and distribute activity across anonymized networks, basic signup controls struggle to separate real users from coordinated fraud.
Spur provides infrastructure-level visibility that strengthens fraud and identity controls at registration, reducing downstream abuse without sacrificing conversion.

How Spur Stops Fraud at Signup.
Spur reveals the anonymized infrastructure behind account creation, enabling fraud and identity teams to selectively block, challenge, or allow signups based on real infrastructure risk.
Technology Company Prevents Fraudulent Account Creation
A technology company reduced fraudulent account creation by over 90% after identifying residential proxy traffic at signup, saving $500K and achieving approximately 40× ROI.
Evidence You Can Act On.
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
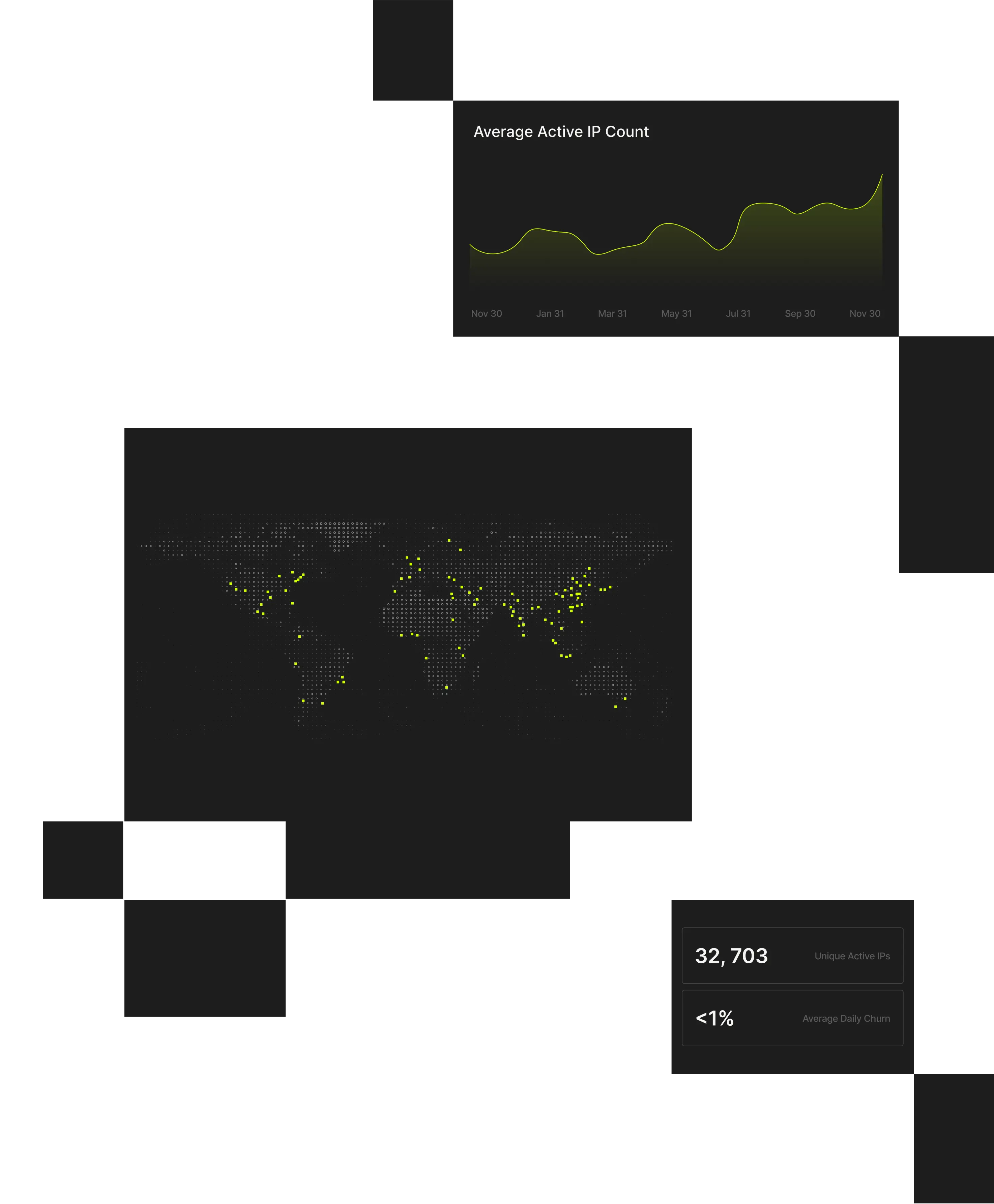
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
1000+
VPN and proxy services detected
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Where Spur Strengthens Every Layer of Defense.
Stop Fake Accounts at the Door.
Detect proxy-backed signup abuse, assess infrastructure risk in real time, and block fraudulent account creation without disrupting legitimate users.