Fraud Teams. Stop Abuse that Looks Legitimate.
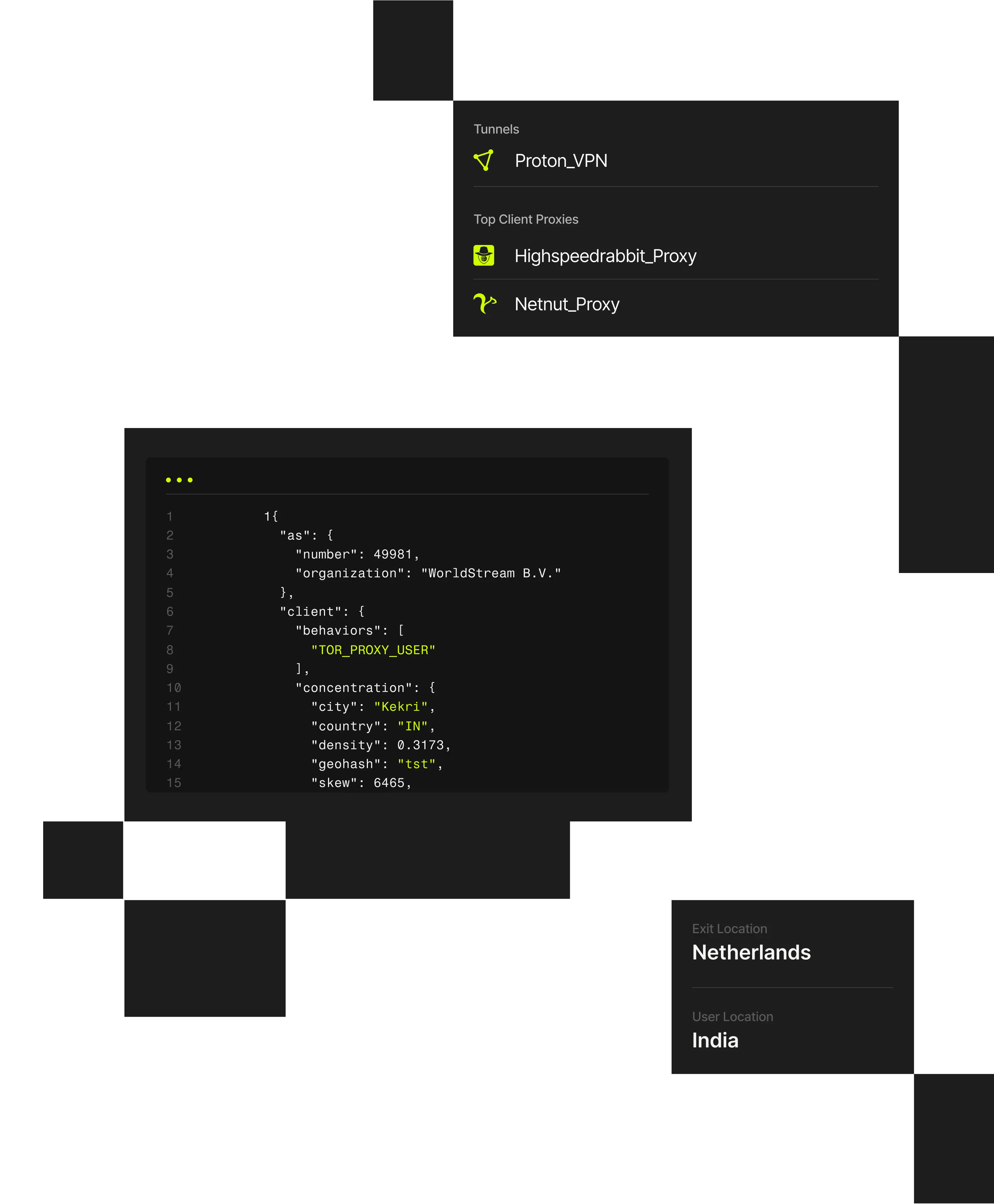
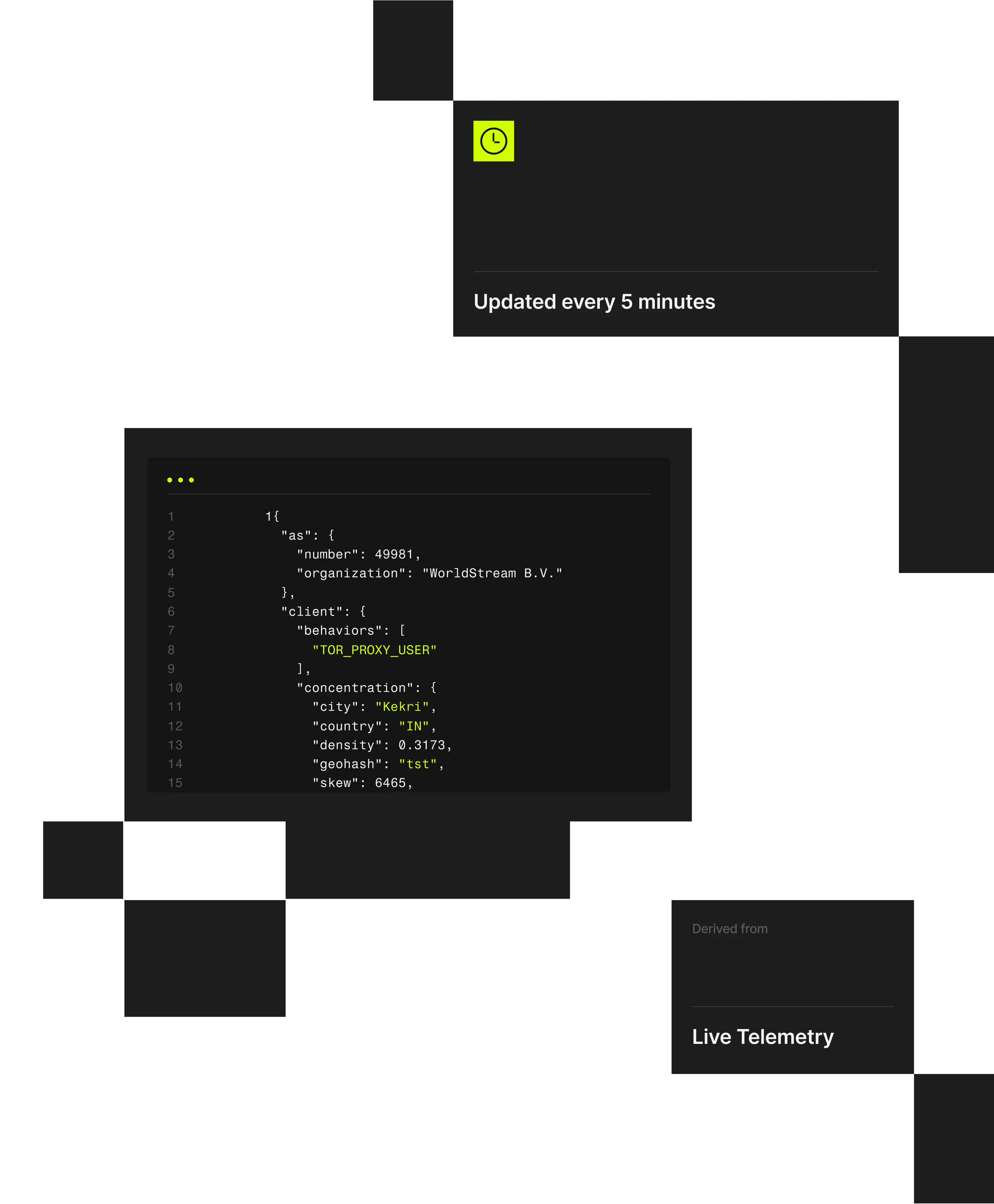
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
Fraud teams face attackers who use VPNs, residential proxies, and automation to make abusive behavior appear like normal user activity. Spur exposes the infrastructure behind fraud attempts, helping teams prevent losses while minimizing friction for legitimate customers.

Fraud Hides Inside Normal User Behavior.
Modern fraud operations must evaluate risk across signups, logins, and transactions where most activity is legitimate. Attackers exploit this by routing abuse through anonymized infrastructure and distributed access patterns that evade traditional rules and velocity checks.
Without reliable network context, fraud teams are forced to choose between missed fraud and false positives. Spur enriches fraud workflows with infrastructure-aware IP intelligence, enabling more precise detection, investigation, and enforcement.

Stop Abuse Without Blocking Growth.
Spur delivers infrastructure-aware IP intelligence that helps fraud teams detect proxy-backed abuse, reduce false positives, and make confident risk decisions across signup, login, and transaction workflows.
Online Retailer Reduces Fraud and Abuse Without Blocking Customers
An online retailer reduced large-scale fraud and abuse by identifying automated and proxy-backed activity targeting account creation and purchasing workflows.
By enriching fraud decisions with high-fidelity IP intelligence, the fraud team disrupted coordinated abuse campaigns, protected revenue during high-demand releases, and reduced false positives that would have impacted legitimate customers.
Evidence You Can Act On.
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
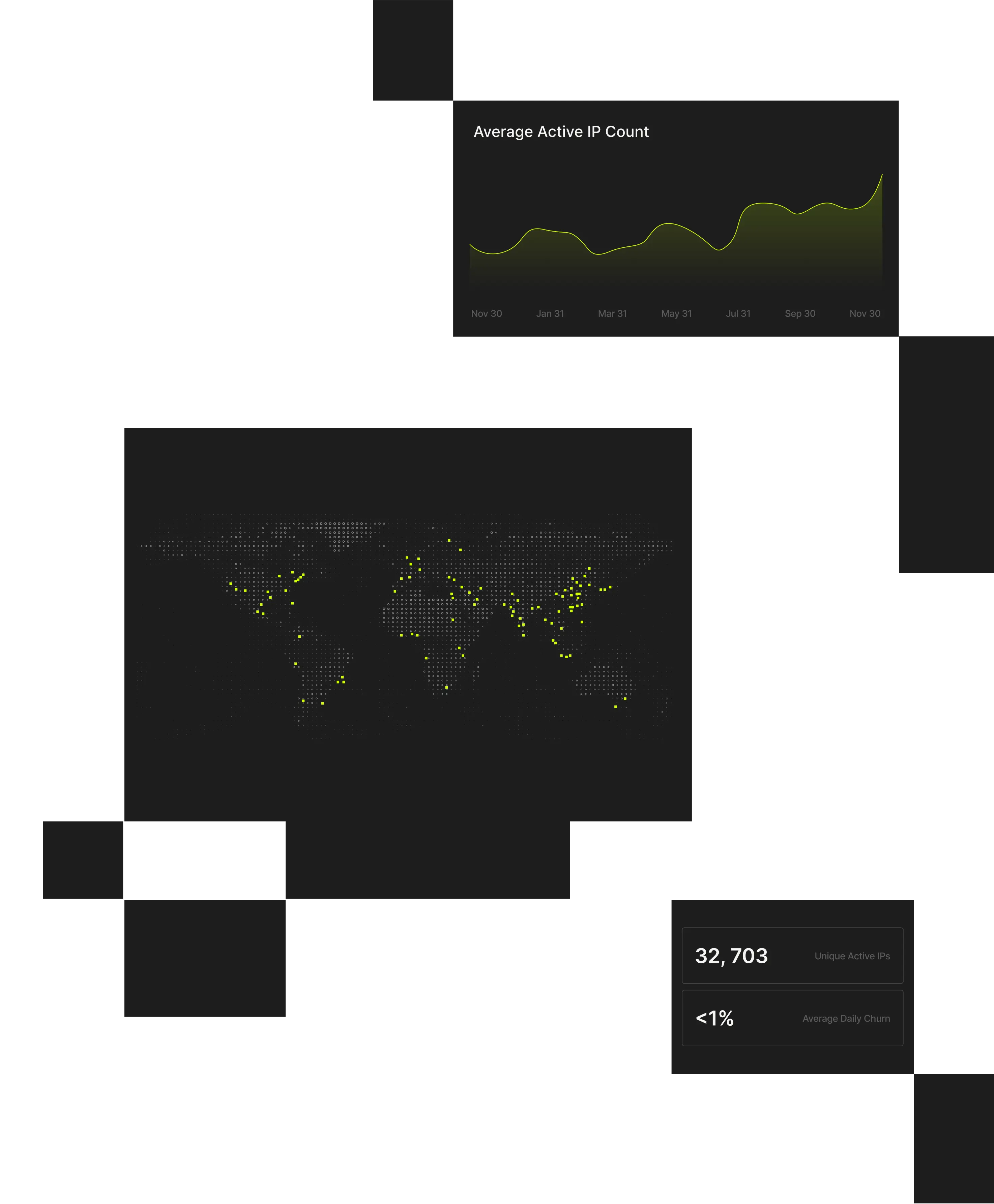
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
1000+
VPN and proxy services detected
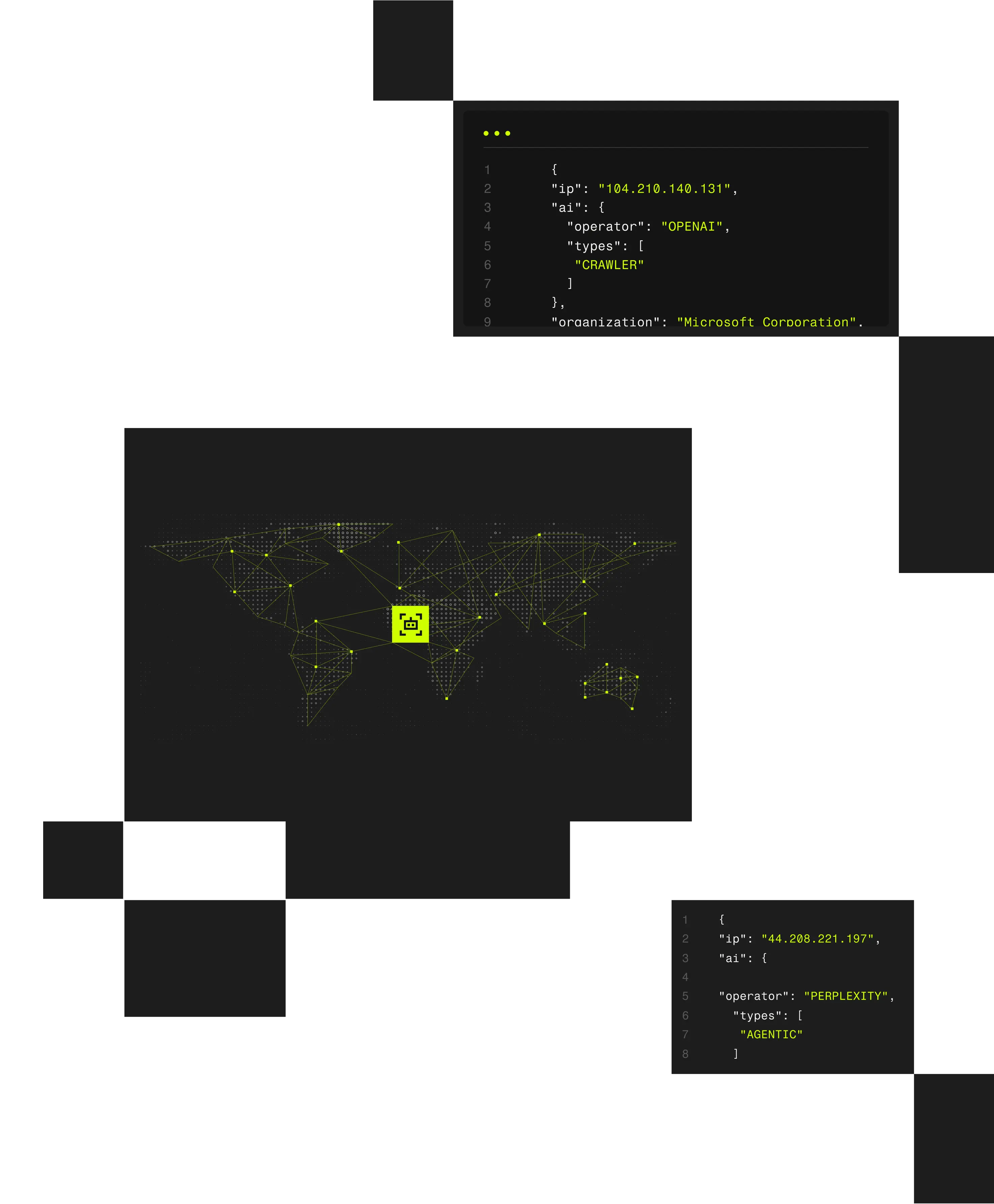
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Strengthen Every Team’s Visibility with Verified IP Intelligence.
Stop Fraud Without Slowing Growth.
Detect proxy-backed abuse, reduce false positives, and make confident fraud decisions across signup, login, and transaction workflows using Spur’s infrastructure-aware IP intelligence.