IT Services Providers. Protect customer environments without adding complexity.
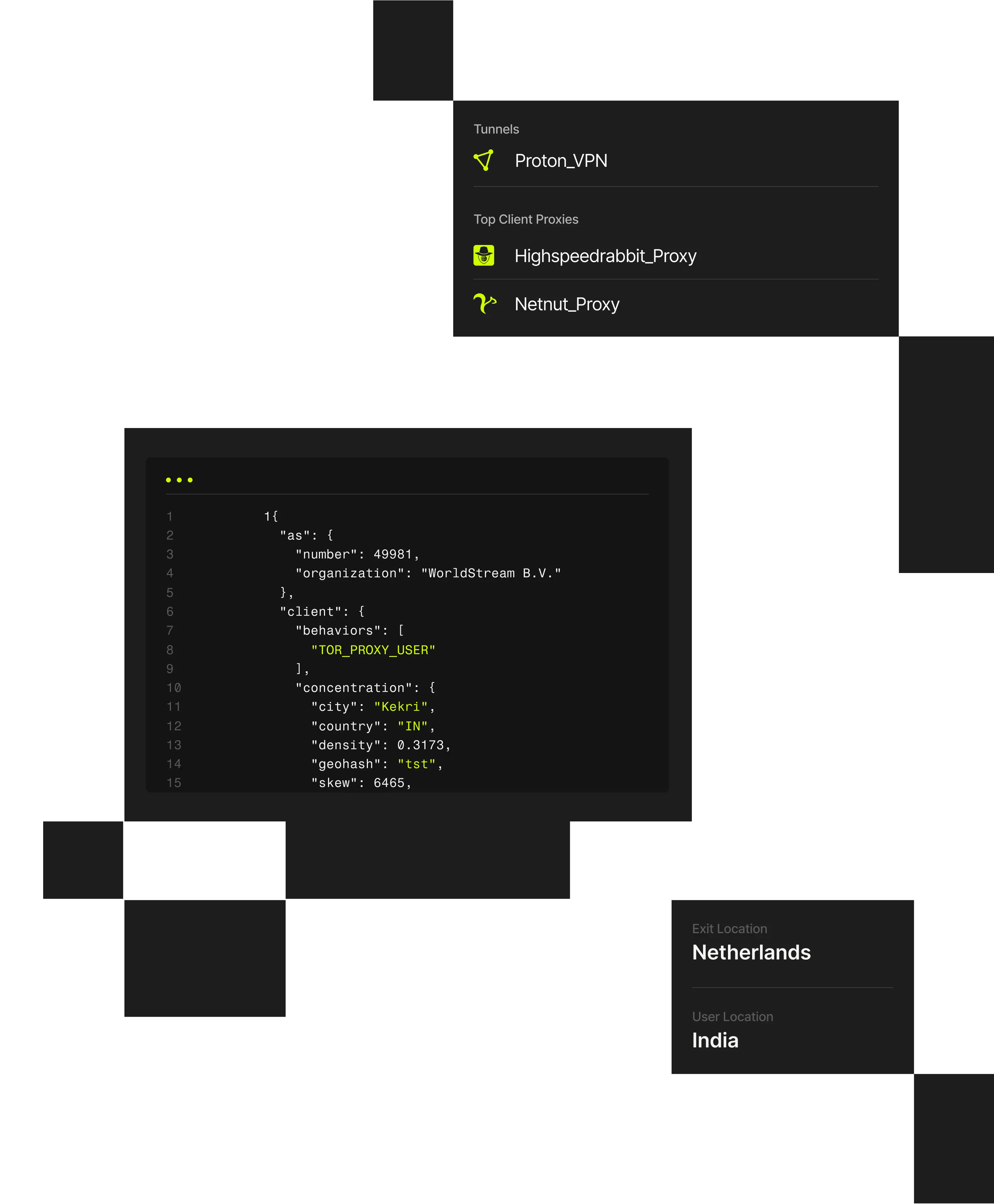
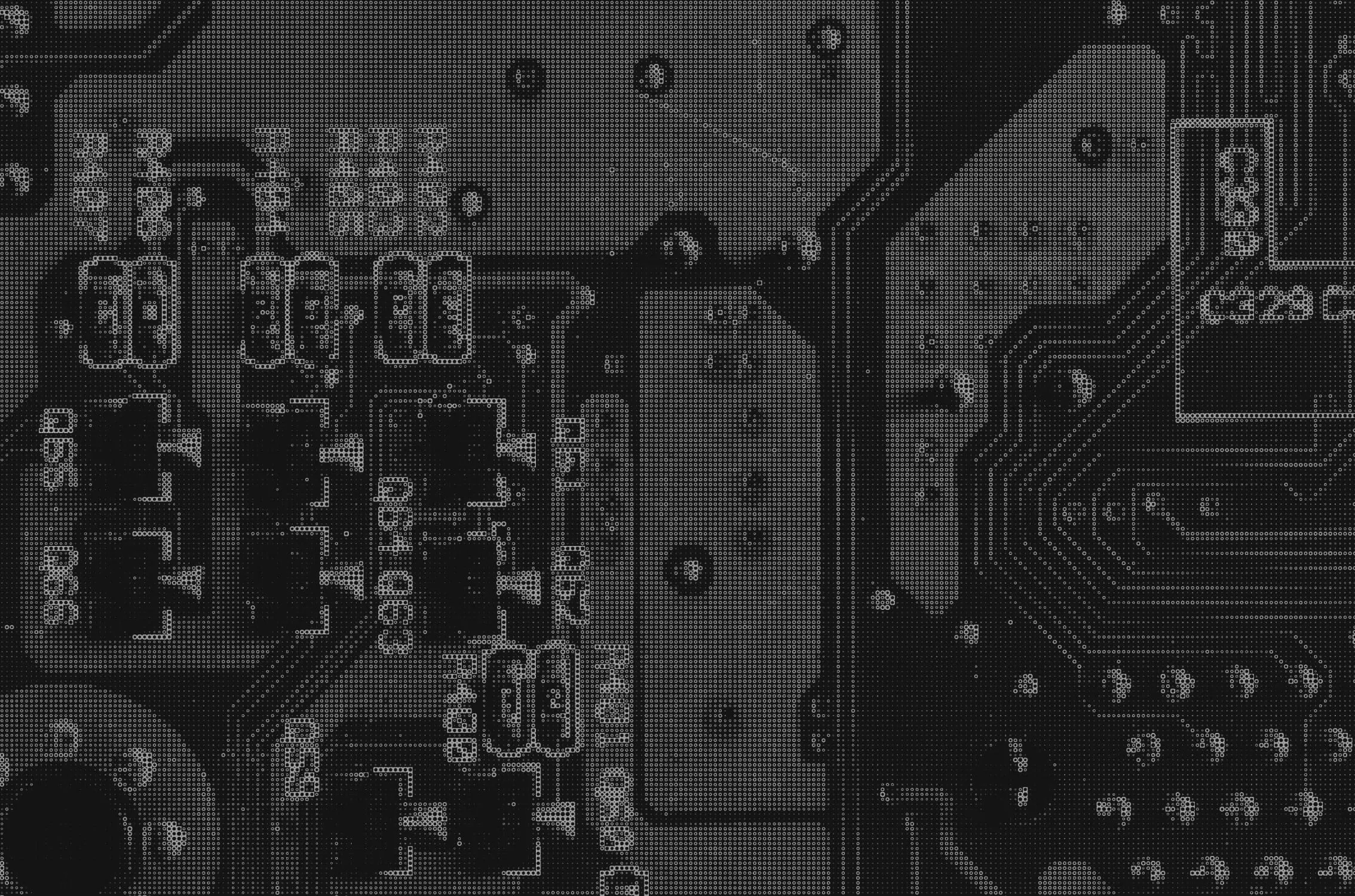
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
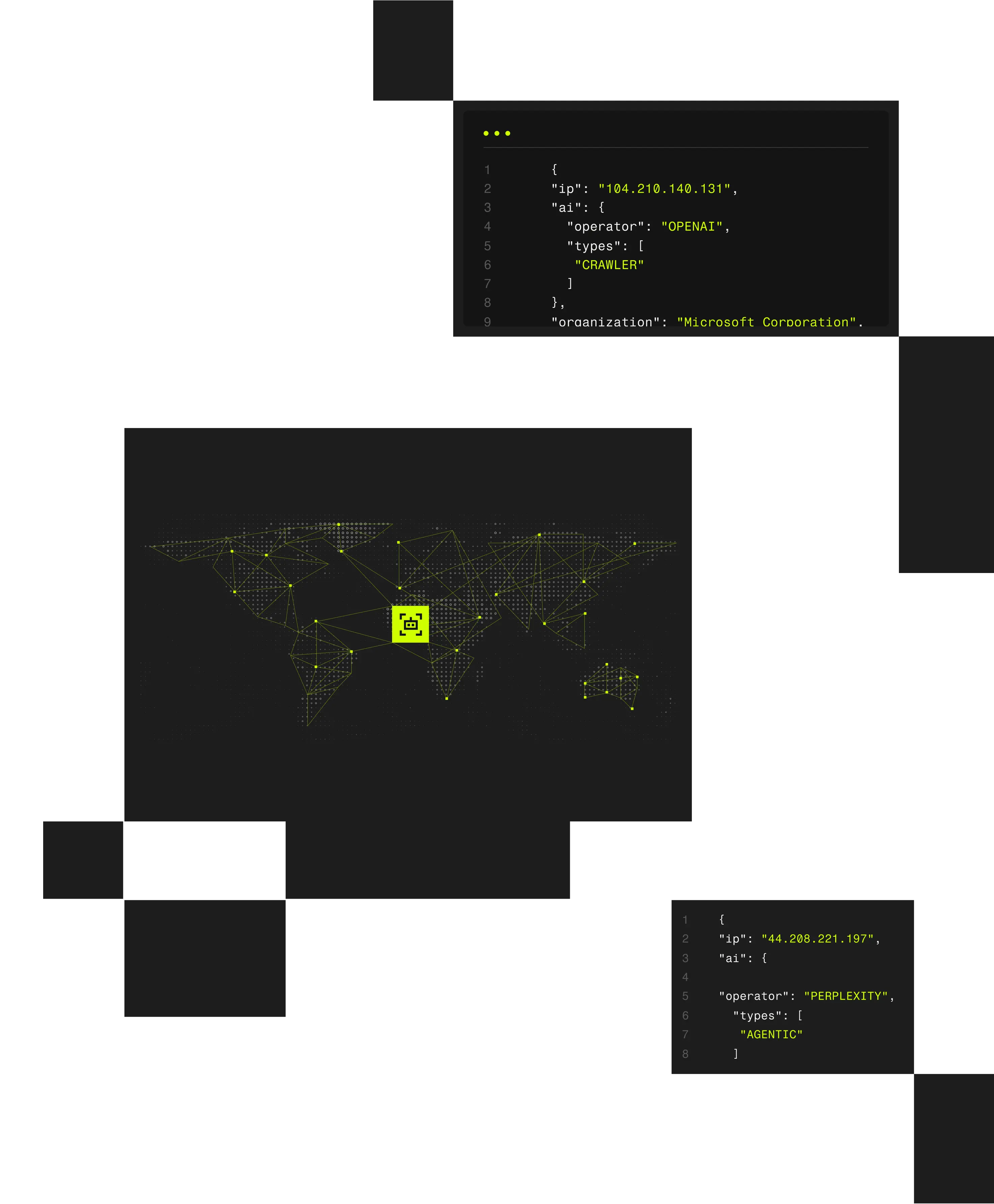
IT services providers support diverse customer environments while defending against fraud, abuse, and cyber threats that often originate from anonymized infrastructure. Spur exposes the network context behind activity, helping providers deliver stronger protection without disrupting customer operations.

Anonymized Infrastructure Complicates Managed Security and Access.
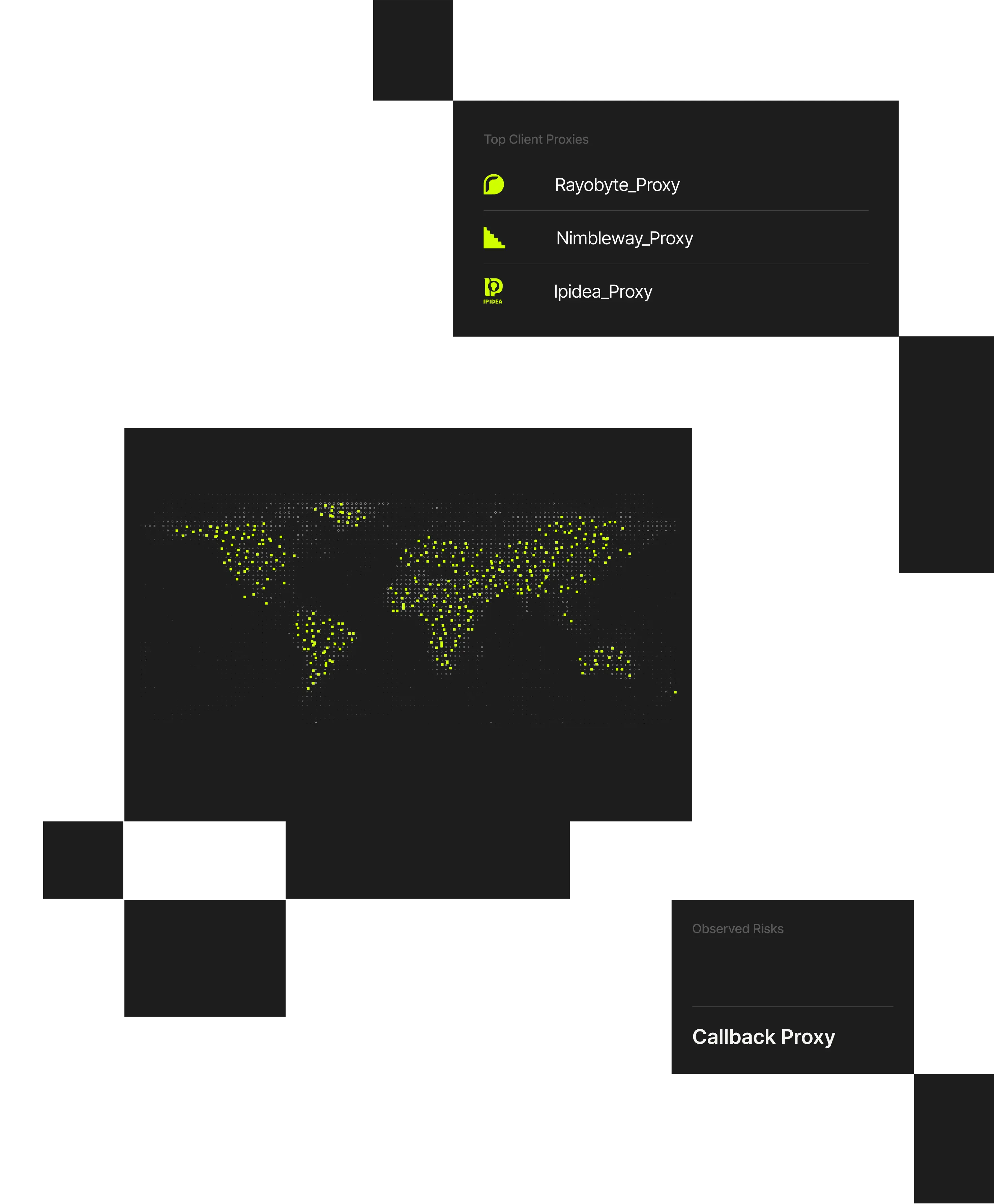
Managed service providers, system integrators, and IT consultancies operate across many customer networks, applications, and access models. Attackers exploit VPNs, residential proxies, and shared infrastructure to mask abusive activity, making it difficult to distinguish real user behavior from coordinated threats against service provider customers.
When visibility is limited, providers risk missed detections or unnecessary disruption. Spur delivers infrastructure-aware IP intelligence that helps IT services providers identify masked activity, support investigations, and strengthen customer security across environments.

Protect Customer Environments and Deliver Defensible Security Outcomes.
Spur provides infrastructure-aware IP intelligence that helps IT services providers detect masked abuse, support investigations, and deliver consistent protection across diverse customer environments.
Evidence You Can Act On.
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
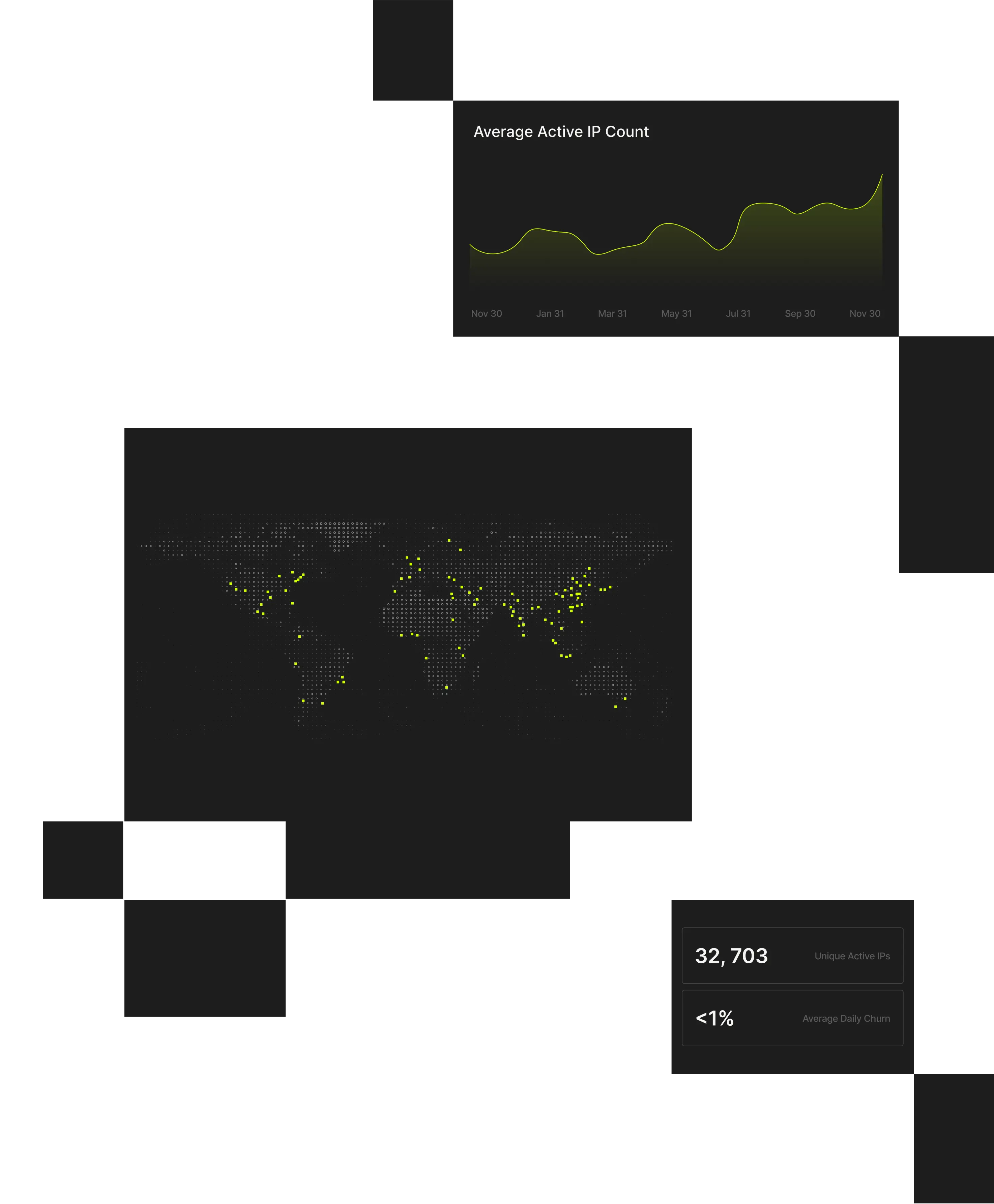
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
1000+
VPN and proxy services detected
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Reveal the truth hiding in plain sight across the sectors Spur protects.
Deliver Stronger Security Across Customer Environments.
Detect anonymized activity, support investigations, and protect customer systems with infrastructure-aware IP intelligence built for multi-tenant and managed service environments.