Detect Bots & Automation Abuse. Expose Hidden Automation at Scale.
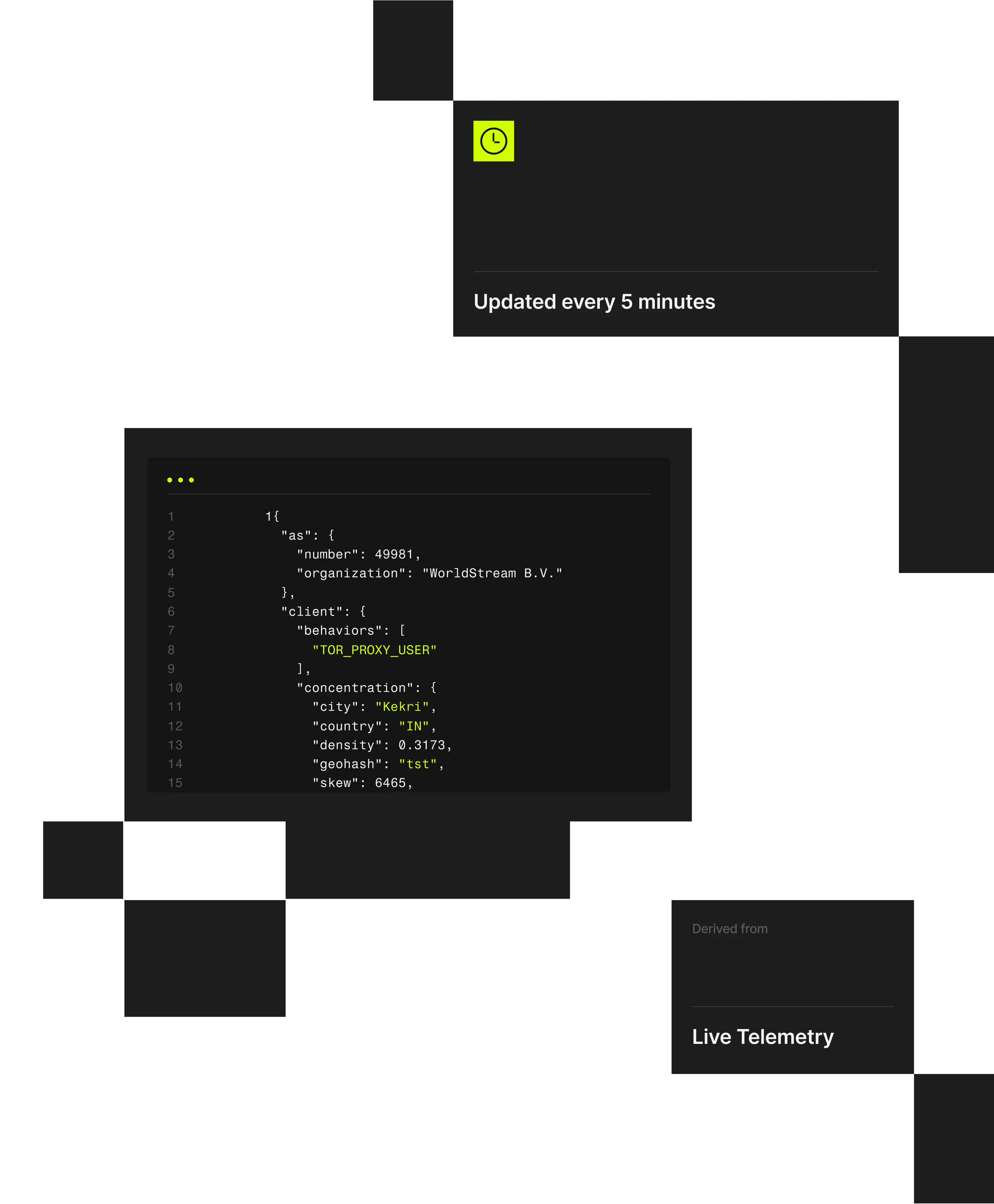
1 "client": {2 "city": "Weldon Springs"3 "behaviors": ["TOR_PROXY_USER"],4 "concentration": {5 "country": "US",6 "density": 0.202,7 "geohash": "9yz",8 "skew": 45,9 "state": "Missouri",
Automated abuse is driven by attackers using scripts and residential proxy infrastructure to make large-scale automation resemble real user activity. Spur exposes the anonymized infrastructure behind automated traffic, enabling teams to detect and control abuse across applications and APIs.

Automation Blends Into Legitimate Application Traffic.
Automation targets applications and APIs through scraping, account farming, and scripted interactions that degrade availability and trust. As bots rotate infrastructure and mimic real users, rule-based and behavior-only defenses become brittle at scale.
Spur adds a durable infrastructure signal that helps teams identify and manage automated abuse even as tactics, tooling, and traffic patterns evolve.

How Spur Detects Bots & Automation Abuse.
Spur provides infrastructure-level visibility that helps security and fraud teams detect detect bot and AI abuse, apply targeted controls, and protect applications at scale.
Online Retailer Prevents Large-Scale Scalping Automation
An online retailer prevented large-scale scalping and automated purchasing by detecting bot traffic routed through residential proxy networks during major product releases.
By exposing proxy-driven automation at scale, the retailer protected inventory availability and reduced abuse without blocking legitimate customers.
Evidence You Can Act On.
Spur’s verified IP intelligence helps teams move faster, detect more, and protect what matters – without adding friction for real users.
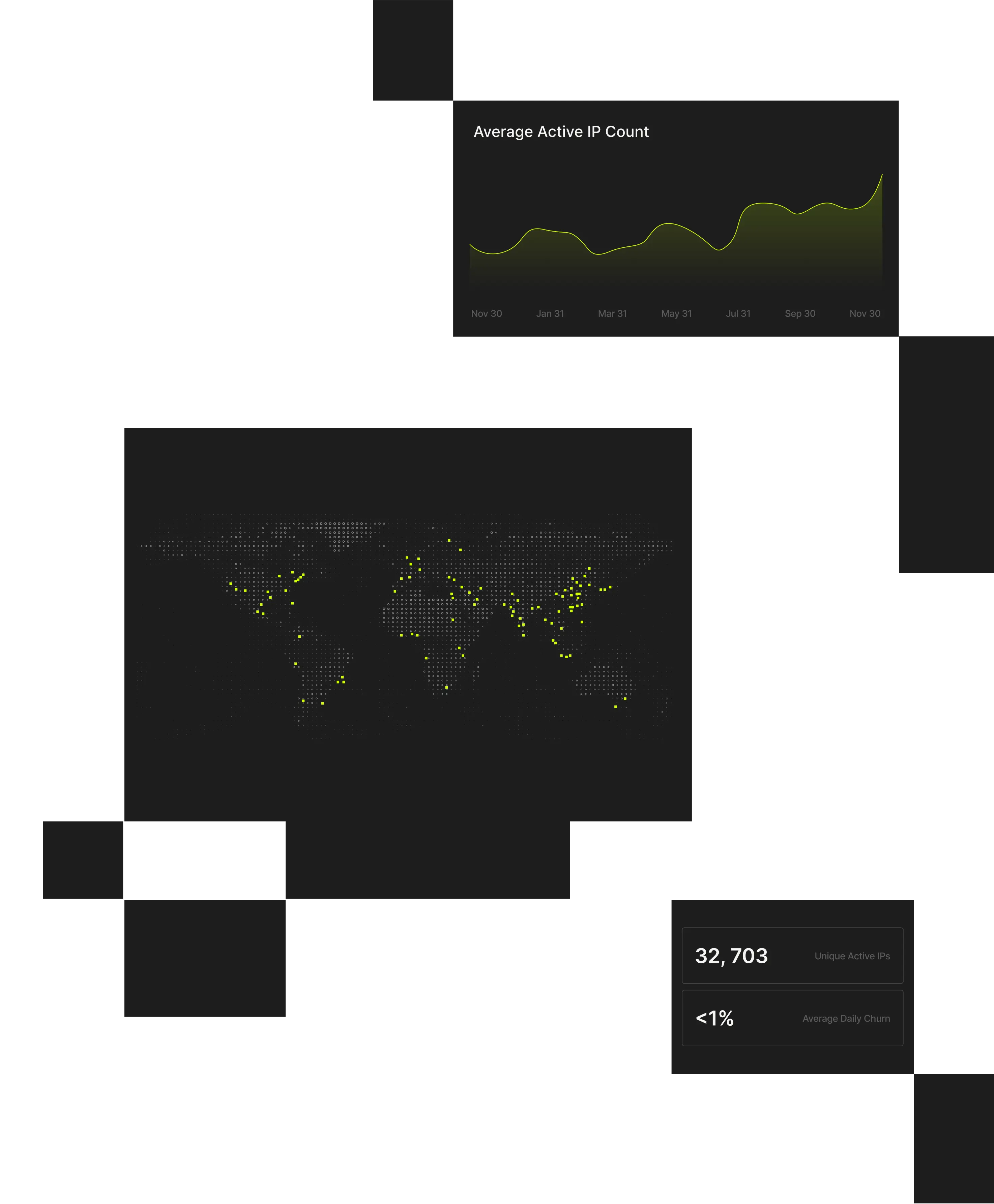
230M+
Unique anonymized IPs detected every 90 days, distilled into 60M suspect IPs daily
1000+
VPN and proxy services detected
20+
Enrichment attributes for full context (geo, ASN, proxy type, device, tunnel entry/exit, etc.)
Where Spur Strengthens Every Layer of Defense.
See Automation Others Miss.
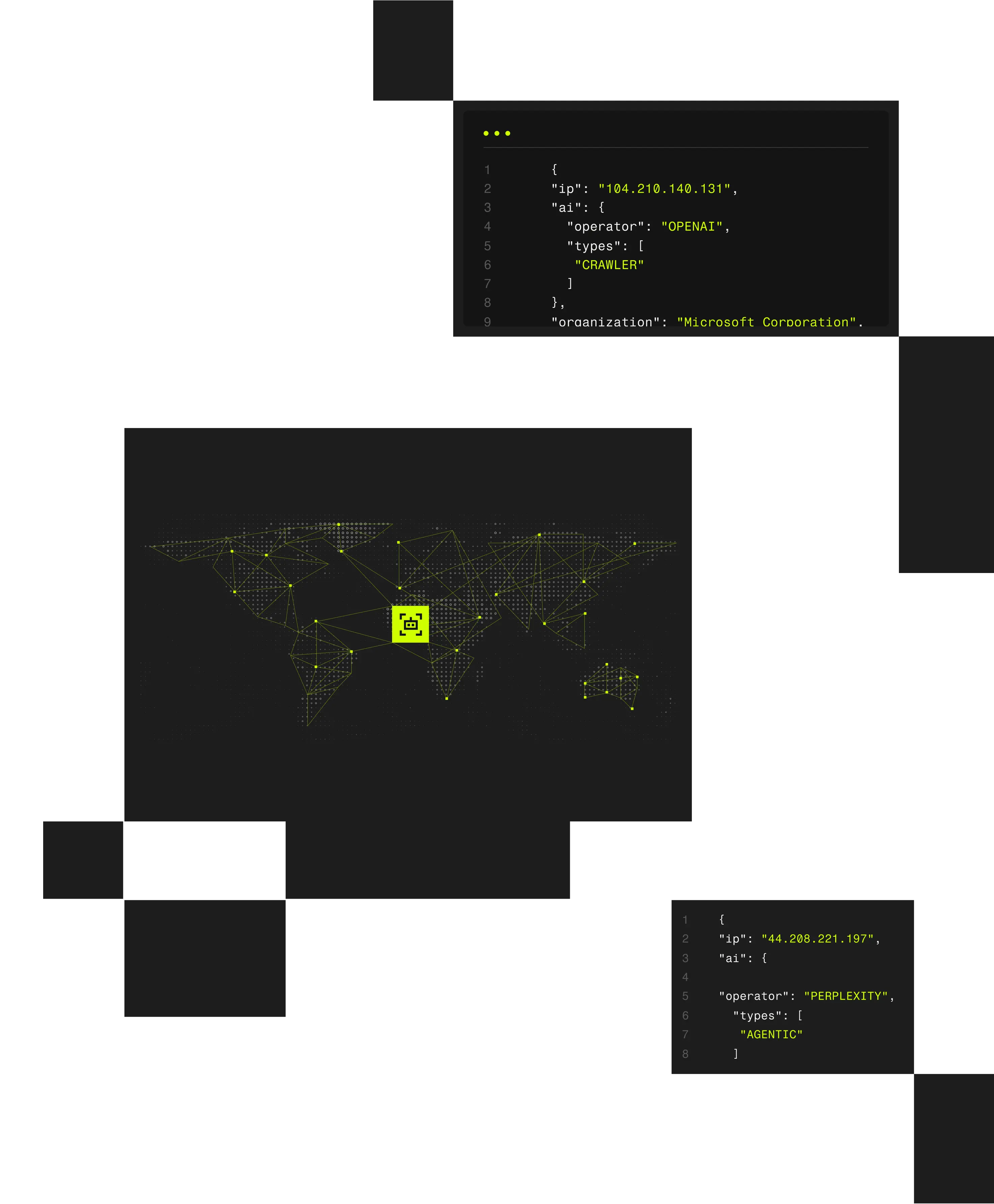
Expose proxy-backed bots, scripted abuse, and agentic activity using network-level intelligence that scales across applications and APIs.