Session Enrichment.
Detect anonymized sessions and coordinated abuse in real time.
Monocle Session Enrichment enables your security and fraud teams to log, filter, or block bad traffic – defending your digital platforms with minimal user friction.
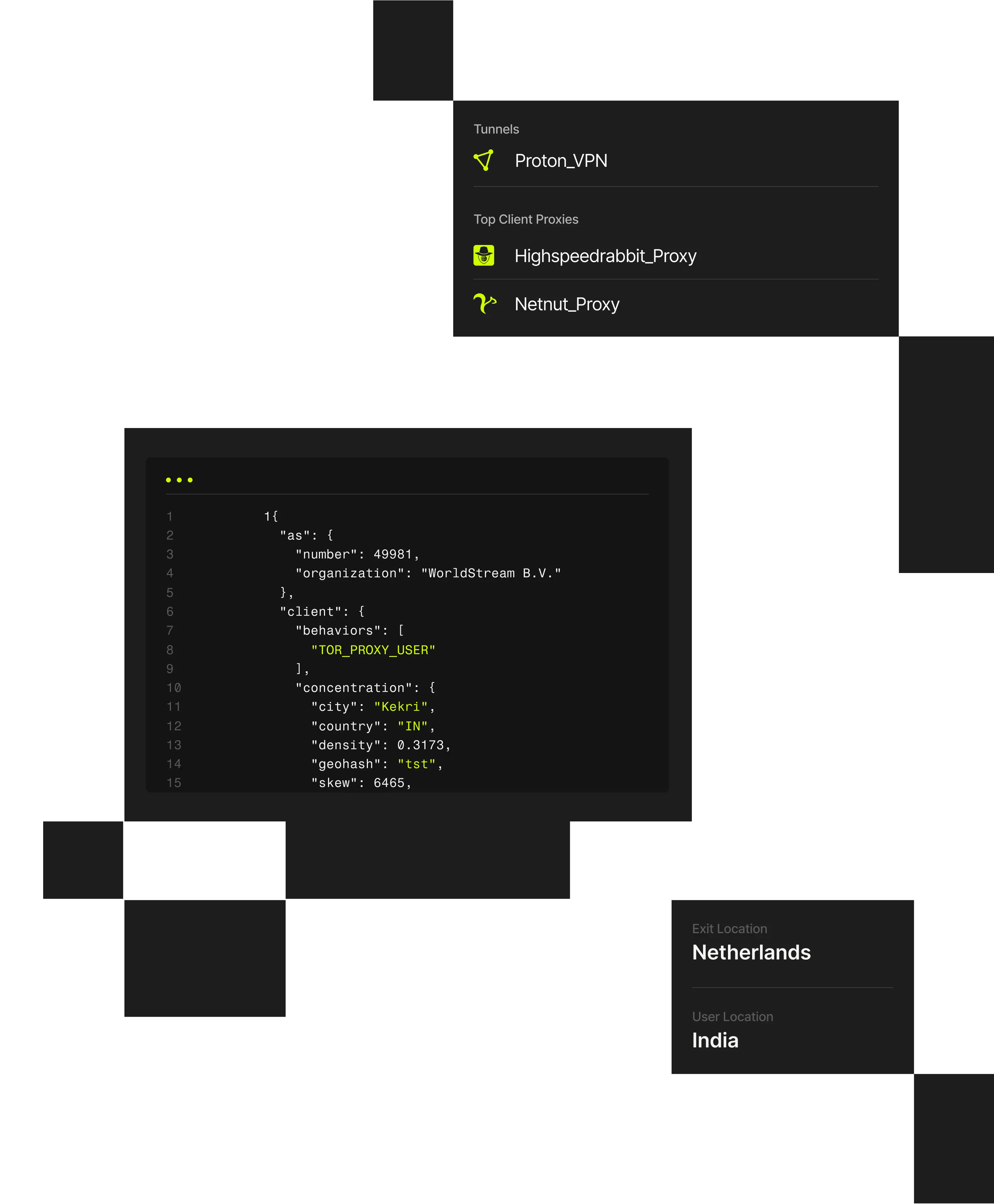
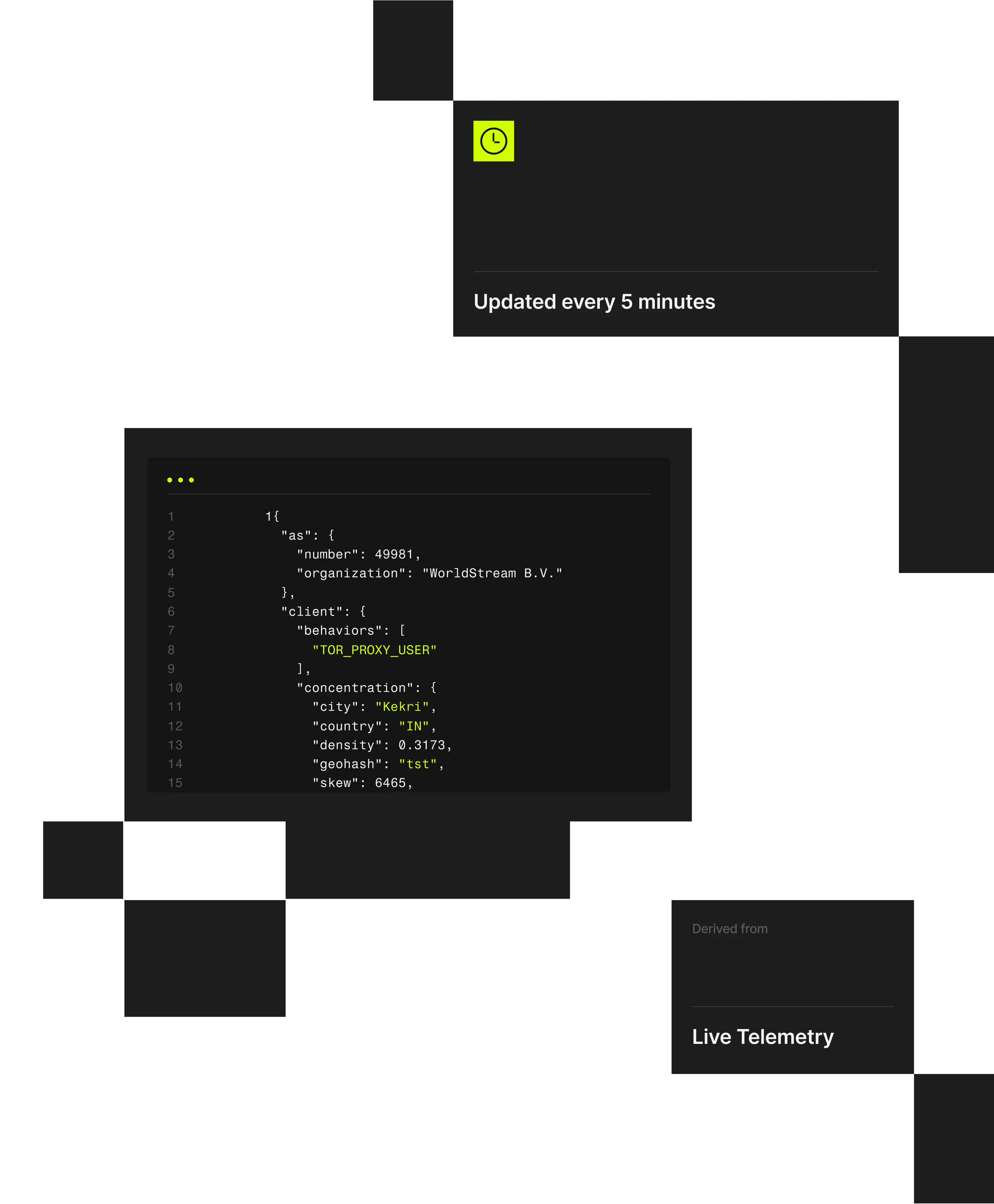
Spur Monocle Session Enrichment passively correlates IP intelligence with live session telemetry to detect automation, anomalies, and abuse in real time. Deployed via a lightweight JavaScript snippet, it operates entirely at the edge – without cookies, tracking, or centralized storage.
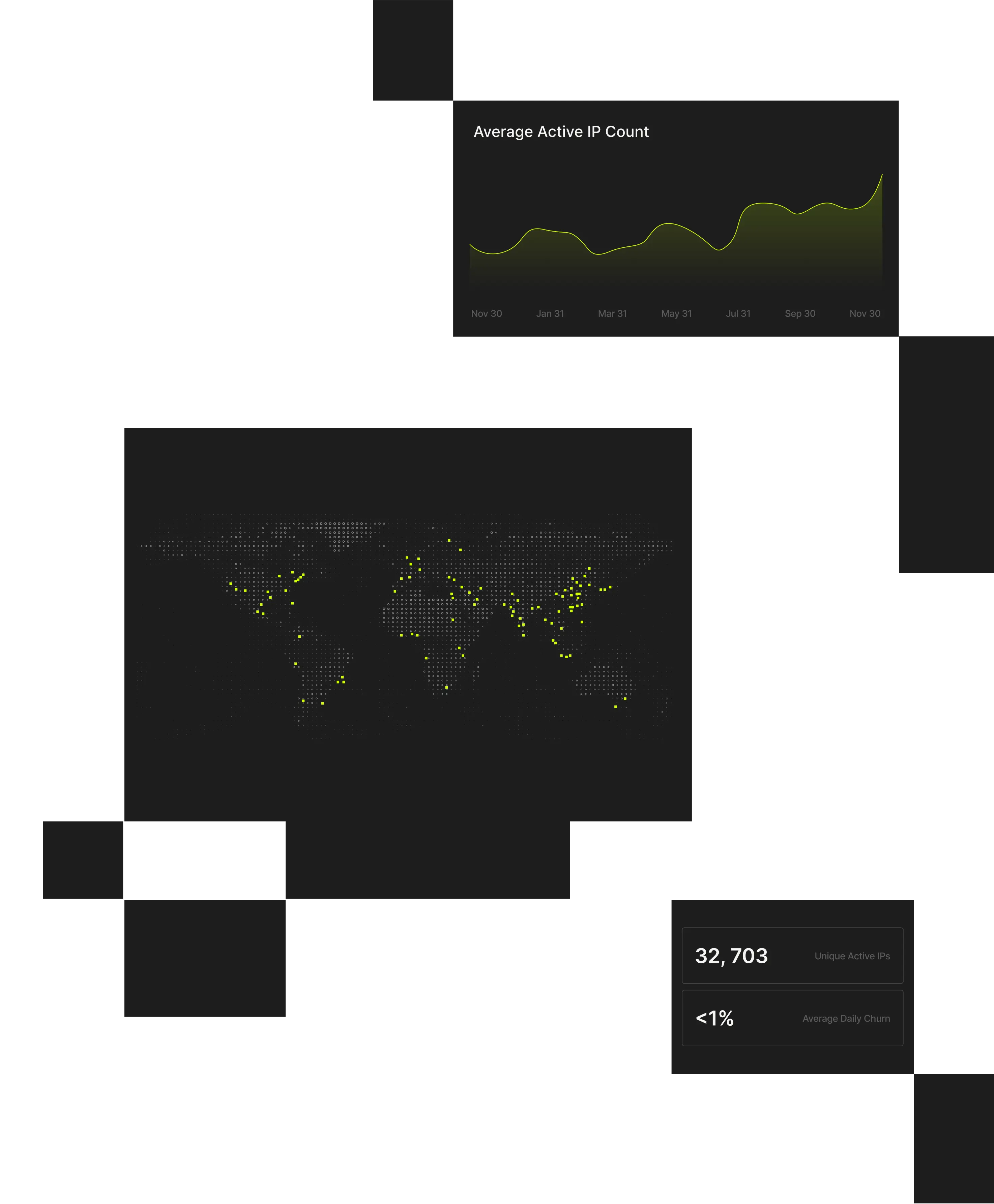
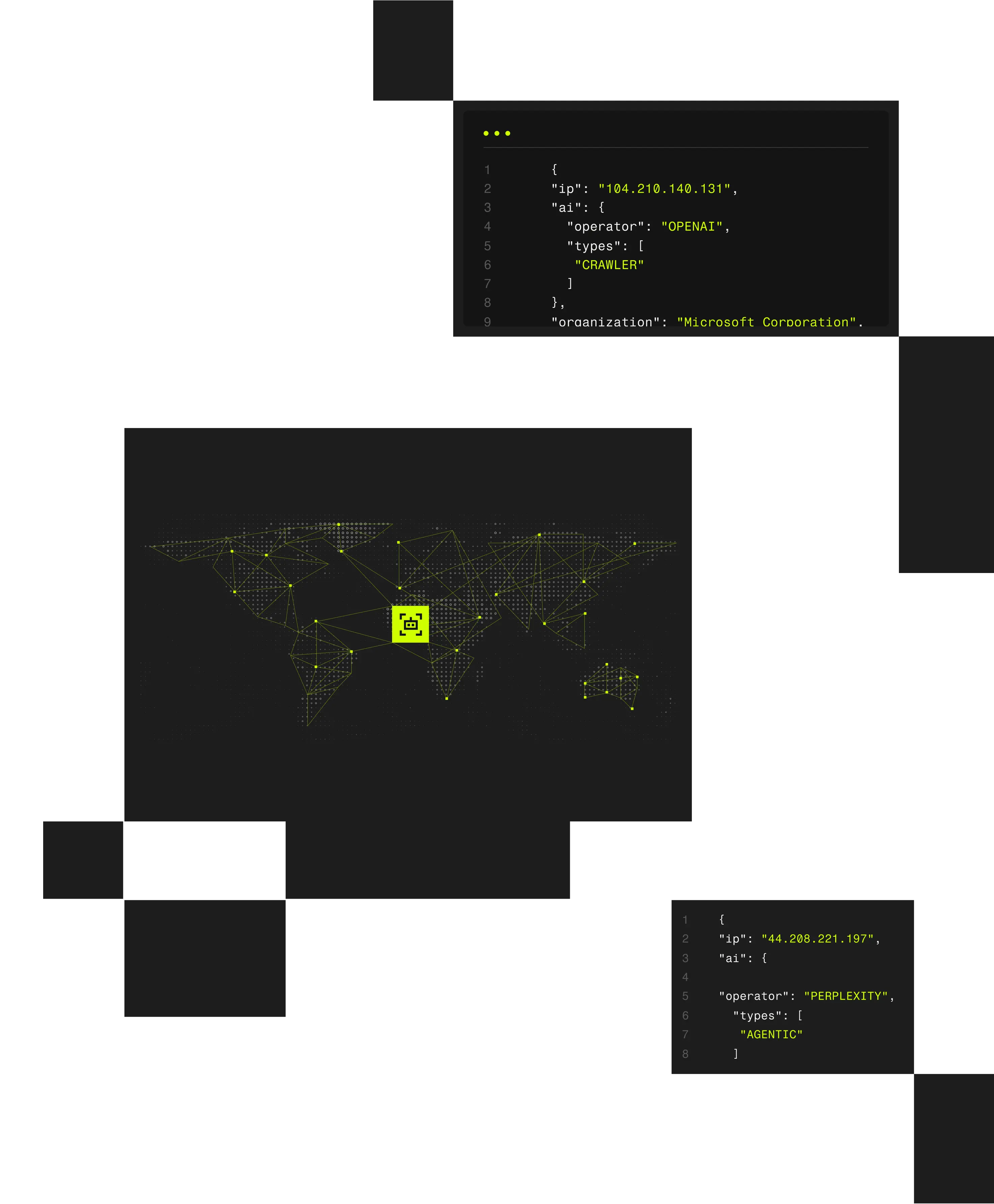
Modern abuse doesn’t occur in isolation; it unfolds across distributed sessions and devices. By combining session data with Spur’s global IP intelligence, Monocle exposes coordinated fraud and automation that traditional IP or device fingerprinting tools can’t detect.
Benefits:
- Detect coordinated automation and credential abuse in real time.
- Correlate behavioral and network indicators to identify hidden threats.
- Strengthen investigations and response workflows without adding friction for legitimate users.

How Spur Detects Anonymized Sessions
- 01
Assess:
- 02
Correlate:
- 03
Act:
Why Teams Choose Spur Session Enrichment
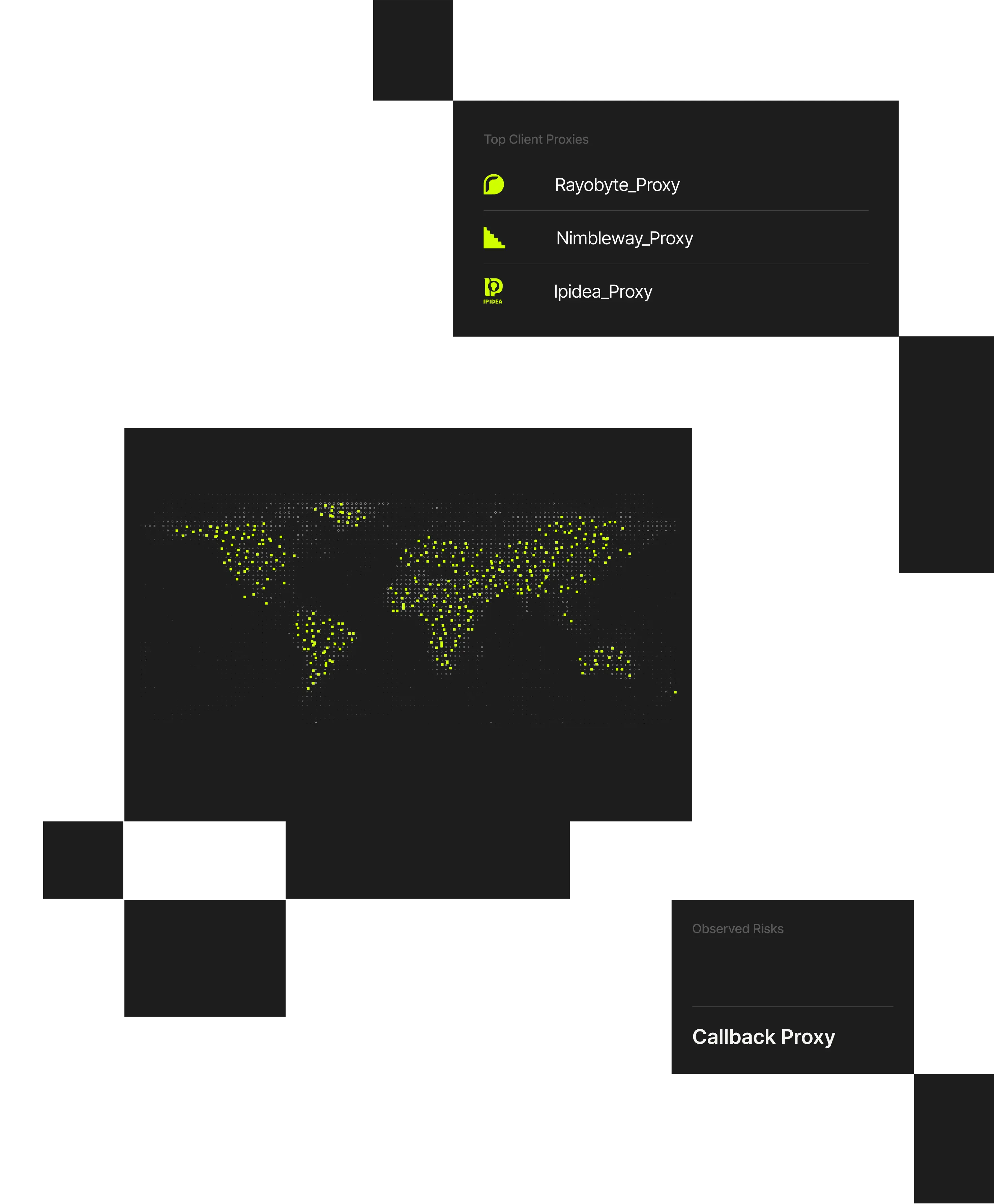
Where Spur Session Enrichment Delivers Value
Trusted by Teams Who Need to See What’s Real.
- Read Case Study
Social Media Platform:
Stopped account farming by correlating residential proxy detection with session behavior.
- Read Case Study
Online Retailer:
Detected coordinated scalping by correlating anonymized sessions during major product releases.
- Read Case Study
Gaming Company:
Exposed proxy-backed abuse by enriching sessions with infrastructure and provider attribution.
FAQs About Spur Session Enrichment
See What's Happening Inside Each Session.
Detect automation, abuse, and anonymized access across user sessions with real-time, privacy-first session enrichment from Spur.