A Quick Recap
Residential proxies and malware proxies are one of the core technologies Spur is battling in the fight against fraud. These services have large pools of IP addresses with benign reputations. But how? The answer is SDKs. These semi-legitimate SDKs offer monetization for mobile and desktop developers.
These SDKs are reverse-tunnels connecting back to their parent service and allow the proxy company’s customers access to the end-user’s internet connection. When the end-user agrees to the application’s terms of service, they unknowingly provide consent to the proxy SDK. When an affected device is connected to their home network, the home network can be used by any of the proxy service’s customers. The same is true when that user takes their device to work.
Many of these companies offer Know Your Customer (KYC) checks to prevent abuse of those networks. However, the core purpose of many of these providers is to circumvent blocking/rate-limiting and enabling scraping and e-commerce abuse (for instance, sneaker bots). In the best of cases, your ISP sends you a cease and desist letter for the activities of the proxy user. Worst case, the proxy company allows scraping of internal network resources and you experience a breach. Note: The latter is not allowed by every proxy provider company.
Everything Begins With Ads
While doing research last week on Microleaves/Shifter and identifying how they source their proxies, I was hit with a few ads in my Google search (see below). I know that there are a few providers out there for residential proxies, but how many could there possibly be?
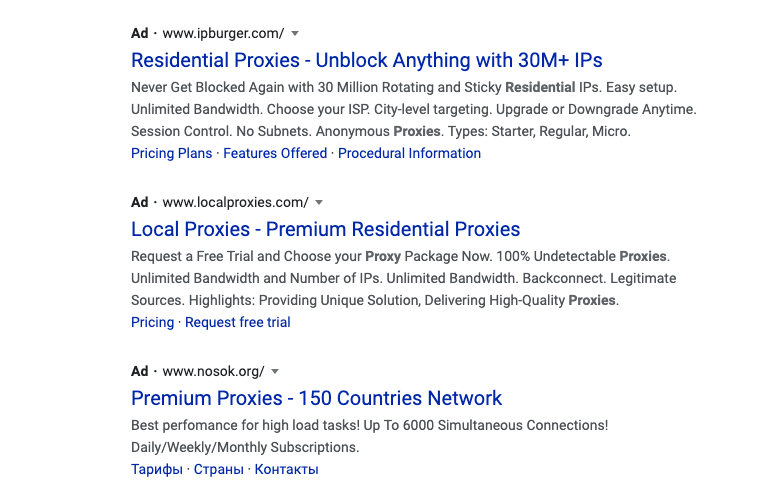
Prior to this ad, I had never heard of IP Burger; however, Local Proxies have popped up before but never warranted much investigation. The thing about IP Burger that made me nervous was their claim of 30 million IPs. How is a company that I have never heard of promising as many IPs as the “big players?” Luminati and OxyLabs have extremely large IP pools but they are the big players in this space. Again, these networks all tend to source their IP addresses in the same manner. They use embedded SDKs in mobile and desktop applications to gain access and hide consent within their terms of service. Which takes me back to this 30M IPs. With 72M from Luminati, 70M from Oxylabs, 30M from IP Burger… these all add up. We know that some devices might have both SDKs so there will be overlap. But still, how do network defenders or e-commerce platforms defend against this scale of available IPs?
Time to `dig` in
My curiosity got the best of me and I had to know how prevalent is IP Burger. I went to check out their dashboard and noticed they use a very similar API to both Luminati and Oxylabs. The general pattern is `http://<username>-<asn>-<country code>:<password>@residential.ipb.cloud:7777` or something very similar. What stood out to me was the `7777`. That is what OxyLabs uses.
Well, I wanted to take a look and see how the backend infrastructure might be organized for “residential.ipb.cloud”. Most providers rely on DNS to round-robin between a swath of backend IPs which manage connections out towards the proxy themselves.
> dig residential.ipb.cloud
; <<>> DiG 9.10.6 <<>> residential.ipb.cloud
;; global options: +cmd
;; Got answer:
;; ->>HEADER<<- opcode: QUERY, status: NOERROR, id: 43536
;; flags: qr rd ra; QUERY: 1, ANSWER: 12, AUTHORITY: 0, ADDITIONAL: 1
;; OPT PSEUDOSECTION:
; EDNS: version: 0, flags:; udp: 512
;; QUESTION SECTION:
;residential.ipb.cloud. IN A
;; ANSWER SECTION:
residential.ipb.cloud. 299 IN CNAME pr.oxylabs.io.
pr.oxylabs.io. 299 IN CNAME geo0node.com.
geo0node.com. 29 IN A 54.39.161.208
geo0node.com. 29 IN A 54.39.218.225
geo0node.com. 29 IN A 158.69.176.129
geo0node.com. 29 IN A 54.39.161.209
geo0node.com. 29 IN A 192.95.37.29
geo0node.com. 29 IN A 51.161.70.129
geo0node.com. 29 IN A 54.39.161.229
geo0node.com. 29 IN A 54.39.163.72
geo0node.com. 29 IN A 149.56.177.65
geo0node.com. 29 IN A 66.70.141.65
;; Query time: 127 msec
;; SERVER: 8.8.8.8#53(8.8.8.8)
;; WHEN: Mon Aug 17 07:09:50 EDT 2020
;; MSG SIZE rcvd: 263Well that explains a lot. IP Burger is either owned by OxyLabs or they lease their infrastructure. This is quite the relief. I would hate to know that IP Burger has a giant pool that is distinct from OxyLabs.
But are there more?
This definitely got me thinking. IP Burger is likely not the only company like this. There are probably many more services that utilize OxyLabs large IP pool for themselves. What better way to look for CNAME records than checking out Security Trails.
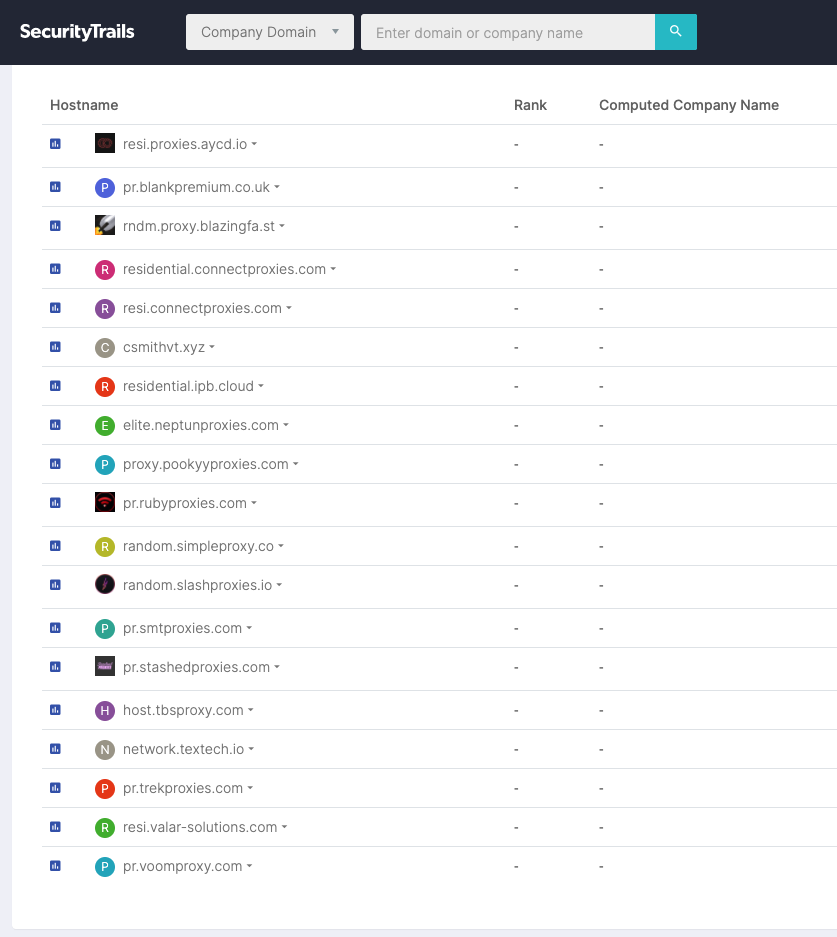
It looks like there are a lot of services out there that utilize OxyLabs for their proxies. They all look like distinct services but in the end, use the same IP pool.
To list a few (also used DNSDB):
proxystrike.io
pureproxies.io
cyperproxies.io
slashproxies.io
blankproxies.co.uk
hexproxy.com
neptunproxies.com
stashedproxies.com
tbsproxy.com
rubyproxies.com…and more. These services all have different levels of vetting. OxyLabs goes with a KYC model. Where as IPBurger does not and accepts cryptocurrency. But in the end, they use the same proxies.
What about other well known players?
I took a look at SmartProxy next. Their gateway to access their proxy network is `gate.smartproxy.com`. Taking a look at CNAME records that point here was quite illuminating. Using both DNSDB and SecurityTrails, again, allowed me to find the following companies/products that simply resell SmartProxy access.
unknownproxies.com
whiskproxies.com
ignify.co.uk
proxyheaven.ioUpon looking closer at Whisk Proxies, I noticed that they are now shutting down operations. They had an open letter about their reason for service termination. This revealed even more information about what is going on. It looks like SmartProxy offers resale or white labeling of their proxies. This is very similar to how WLVPN enabled companies like Ookla and NameCheap to offer VPN solutions under their brands.
The VPN landscape has long suffered from the problem of an oversaturated market of brands, but ultimately those brands are controlled by only a few companies. The parent companies either purchase other brands or create spin-offs. Alternatively, infrastructure providers sell VPN-company-in-a-box which allows for several brands on the same infrastructure. I was well aware of the lack of diversity within the VPN industry, but had no idea about proxy providers.
There are a lot of residential proxies out there. They outnumber VPNs 100:1. However, it looks like their landscape is quite similar to VPN services and many are operated by the same set of actors. In each case, it is hard to tell which are same companies and who is just a reseller of proxies. However, it is clear that each reseller provides different levels of vetting and validating. In the residential proxy space, that is a gigantic risk for all of these unwitting users.
Interested in learning more about anonymous networks and how they might affect you? Reach out to us at info@spur.us