How Gopuff Reduced Undesired Web Traffic and Reclaimed Conversion Accuracy with Spur Monocle

Gopuff, a delivery and logistics platform operating websites including Gopuff.com and BevMo.com, was experiencing increasingly aggressive site crawling that closely mimicked legitimate customer behavior. The abusive behavior was both large enough in volume to cause operational challenges and sophisticated enough to bypass legacy defensive measures. By integrating Monocle — Spur’s innovative session enrichment solution — Gopuff was able to meaningfully reduce unwanted traffic while fully preserving order volume and restoring confidence in critical metrics informing the business.
The Challenge: Residential Proxy Abuse at Scale
Over the past 18 months, the team noticed a sharp rise in visits that looked authentic but behaved nothing like normal customers.
This traffic didn’t match our usual browser/native ratios and was out of phase with customer order volume. At times, up to 80% of our traffic was bots.Sr. Director of Engineering, Gopuff
After a joint investigation with Spur engineers, Gopuff was able to trace the anomaly to BrightData, a residential-proxy network advertising over 50 million household IP addresses. The bots:
- Originated from real ISPs (e.g., Comcast, Verizon, Spectrum)
- Evaded CAPTCHA using BrightData’s “captcha unlocker”
- Were only detectable after the first HTML response via Cloudflare
This unfiltered load:
- Triggered false alerts to engineering teams
- Inflated hosting and CDN costs
- Corrupted analytics, especially conversion rate tracking
The Solution: Monocle Deployed in a Cloudflare Worker
In April 2025, Gopuff partnered with Spur to combat this growing problem. After validating Spur’s industry-leading IP-reputation dataset, the team rolled out Monocle - a lightweight client-side, JavaScript-based sensor built to identify residential-proxy and VPN sessions with high confidence.
Because Gopuff’s perimeter already terminated at Cloudflare, Monocle was injected through a Cloudflare Worker positioned between the visitor and Gopuff’s origin. The Worker:
- checks whether Monocle has classified the session
- issues a challenge only when required
This deployment strategy allowed Gopuff to:
- restrict Monocle to specific high-risk sections of the website
- dramatically reduce Cloudflare-related expenses
- minimize latency by executing logic at the edge
The default integration from Spur’s GitHub repo took only minutes, yet Gopuff was able to add several environment-specific customizations with minimal engineering effort.
The Outcome: Cleaner Analytics, Cost Efficiency, and Operational Relief
Post-launch, Gopuff saw a clear segmentation in traffic patterns. BrightData’s crawler activity, as well as activity from other previously unidentified scrapers, fell drastically. Gopuff was able to track which traffic was served, mitigated by Gopuff WAF rules, or blocked by Monocle:
- Blue - Authentic customers receiving priority serving
- Orange - Gopuff custom WAF rules
- Black - Abuse blocked by Monocle
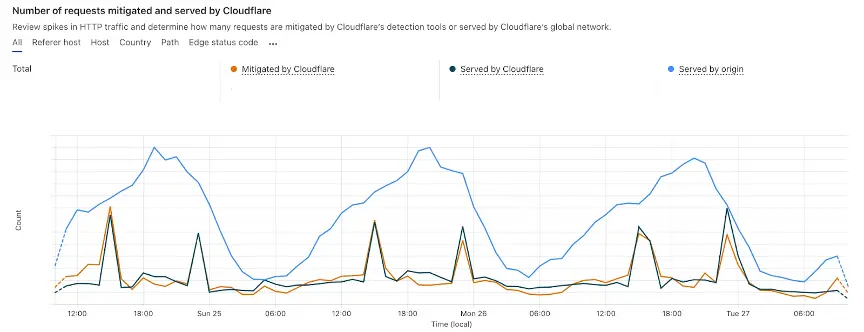
We have seen all of the crawler side effects mitigated. Since rolling out Monocle, we’ve seen lower hosting costs and lower error rates related to crawling. Our customer conversion rate now matches expectations, and has resumed being a useful key performance metric for the Gopuff business.Sr. Director of Engineering, Gopuff
Other benefits:
- Reduced Cloudflare spend
- Less engineering time lost to false investigations
- Real-time traffic segmentation and trend visibility
Precise Bot Defense with Measurable ROI
By embedding Monocle, Gopuff added a precise, low-latency layer to its defensive stack, decisively distinguishing genuine users from automated scraping tools that had slipped past Cloudflare. The result: improved visibility, cleaner analytics, and reduced infrastructure spend — all without negative impact to the customer experience.
Want to reclaim your analytics from scraping bots?
Spur session enrichment can be live in minutes and immediately segments real users from noise — no re-architecture required. Contact Spur for a live demo or test it on your site today.
See the Difference Between Raw Data & Real Intelligence
Start enriching IPs with Spur to reveal the residential proxies, VPNs, and bots hiding in plain sight.