Cutting Costs Through ATO Reduction
Spur tracks anonymity networks at a network and session layer to help our clients combat fraud on their digital properties. This case-study is an example of how our data was put to action by a large financial institution, saving millions of dollars in fraud.
ATO: Fancy Buzzword Acronym
Account Takeovers (ATOs) are a serious threat that have become a popular buzzword in the security industry. ATOs transpire when a malicious actor gains unauthorized access to a user’s account, usually with the goal of illicit financial gain rather than data harvesting. Financial institutions such as banks and brokerages are prime targets for ATO campaigns as the steps required to monetize an account are fewer, and the gains higher.
The financial implications for institutions affected by ATOs are significant. According to industry reports, the average cost of an ATO can range from hundreds to thousands of dollars per incident. This cost comes in the forms of direct financial losses from fraudulent transactions, operational costs of identifying and managing the breach, legal fees for attempted recovery, regulatory fines, and the loss of customer trust and reputation.
ATOs are, of course, nothing new. They have been the primary driver behind the adoption of multi-factor authentication, biometrics, and password managers – each multibillion-dollar industries. Unfortunately, as the industry focuses on initial authentication protections, we have collectively re-opened the door to older forms of ATO being enabled by residential proxies: credential stuffing and cookie replays.
Escalating Tradecraft with Cookie Replays
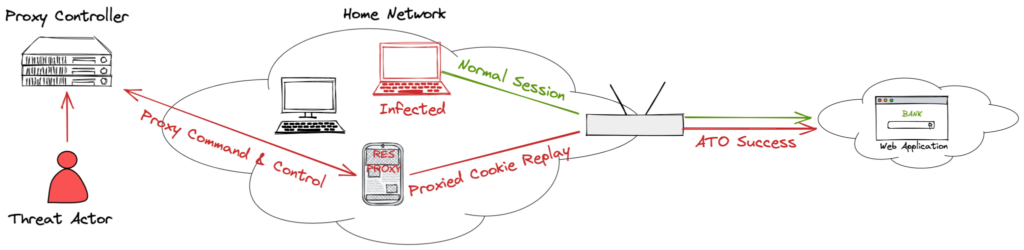
An emerging trend for ATO is the cookie replay attack. Cookies in this context are best described as secret tokens that are issued to a device so that it does not have to keep re-authenticating with a service. Cookies keep your “session” alive with a website. In most businesses, reduced friction means increased user interaction and increased sales or profit. Cookies are long-lived and infrequently invalidated. If an attacker is able to gain access to these cookies (for example through malware, MITM, or a web-site vulnerability), they can use these cookies to access an existing “session” for an account.
Cookie replays are nothing new. There are best practices to follow when issuing and validating cookies. Significant tooling has been done to identify when a session has changed sufficiently to warrant invalidation. Many of these techniques, however, focus on application layer signals. Utilities like browser cloners exist to mimic user-agents and entire device setups. Sandboxes are easy to run and scale. It is has become easy to fake the original browser/device setup.
A key input to cookie validation techniques is source IP Address. If a user session goes from Comcast to AWS, for example, something is unusual and that session should be invalidated. The advent of residential proxies, however, has made this strategy for detection much less reliable. The diversity of IPs provided by residential proxies, means an attacker can find similar IP Addresses to route their traffic, in some cases the same IP Address as the original client. This obfuscation makes the attack particularly insidious and challenging to detect.
Escalating Tradecraft with Credential Stuffing
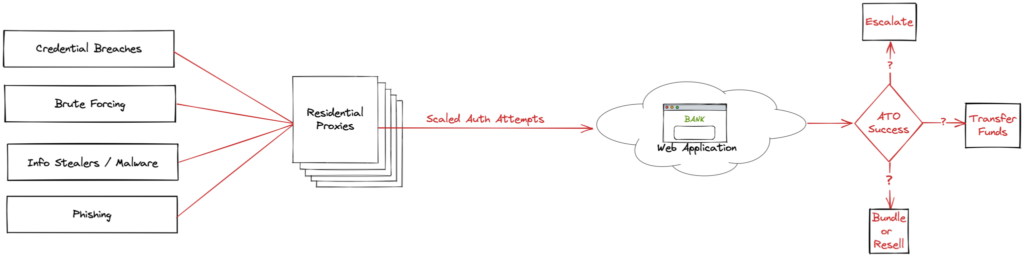
Residential proxies have enabled even more sophisticated credential stuffing attacks. Using a wide diversity of IP Addresses, actors can circumvent brute force protections and captcha challenges. In scenarios where a service (or user) does not have MFA enabled, these attacks can be blind and built on weak password, previously cracked or exposed passwords, or other data breaches. The attack is scaleable and consequently the chance for success is much higher.
Credential replays become even more effective through phishing or mal-vertising campaigns when an MFA code can be elicited from a user in real-time. When an actor goes to mirror the login, they can do so from a similar IP Address or nearby mobile IP to decrease the chance of detection.
The Need for a Network-Based Approach
Residential proxies have become a favored tool for executing both attacks. Unlike traditional VPNs or datacenter proxies, residential proxies use the IP addresses of real residential users, making them harder to detect and block. This provides a cloak of legitimacy, allowing fraudsters to blend in with regular users, making ATOs increasingly difficult to prevent. These techniques are re-enabling the scalability of many types of older attacks.
Given these challenges, a network-based approach to detect and mitigate ATOs is crucial. By focusing on the network characteristics and the specifics of the IP address used during a session, it’s possible to discern legitimate users from fraudsters, even if they are using residential proxies.
Spur’s tools and data provide information on a fully qualified IPv4 and v6 address rather than network blocks, and can even detect proxies at a user session level. This granular focus on network data, as opposed to user behavior, provides a more objective basis for detecting potentially malicious activity and a strong signal for validating existing cookies or new user authentications.
Case Study: Combating ATOs in a Financial Institution
Recently, a US financial institution leveraged Spur’s data feeds to enrich user sessions during account creation and authentication. When authentication attempts from known anonymization networks were detected, the system escalated the requirement for additional verification. For suspected cookie replay attacks, user activities from an IP associated with a known anonymity service were blocked, particularly when these activities involved elevated privileges, such as fund transfers.
These implementations reduced ATOs by over 40%, and the financial institution saved significant sums of money. Besides the direct financial losses averted, the institution also saved on operational costs linked to breach management and mitigation. Furthermore, by maintaining a strong cybersecurity posture, they managed to preserve customer trust and their reputation.
Conclusion
The threat landscape is constantly evolving, with residential proxies posing a significant challenge to preventing ATOs. This infrastructure is making old, seemingly difficult attacks to scale, viable once again. Spur believes that a network-based approach is a necessary signal to any meaningful user risk system.
As the costs associated with ATOs continue to rise, so does the value of innovative, effective defenses. By focusing on network data, we can unmask the fraudsters hiding behind residential proxies, significantly mitigating the risk and financial impact of ATOs. Contact us today to learn about how Spur can help save your company money by reducing ATOs.